- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
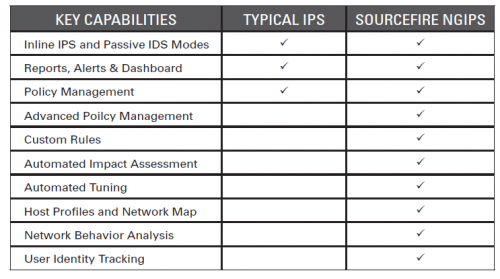
Next Generation IPS
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
NGIPS also provides essential information about users of a network, either individually or as members of groups.
NGIPS maximizes choice by providing systems offering a range of security functionality, across both physical and virtual platforms.
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce auctor diam in est ullamcorper, sit amet tempus metus egestas. Fusce dignissim, sem at maximus tempus, sapien arcu
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce auctor diam in est ullamcorper, sit amet tempus metus egestas. Fusce dignissim, sem at maximus tempus, sapien arcu
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce auctor diam in est ullamcorper, sit amet tempus metus egestas. Fusce dignissim, sem at maximus tempus, sapien arcu
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Fusce auctor diam in est ullamcorper, sit amet tempus metus egestas. Fusce dignissim, sem at maximus tempus, sapien arcu
What is a Next Generation IPS?
- Inline, bump-in-the-wire configuration: Should never disrupt network operations.
- Standard first-generation IPS capabilities: Should support vulnerability-and threat-facing signatures.
- Application awareness and full-stack visibility: Should identify applications and enforce network security policy at the application layer.
- Context awareness: Should bring information from sources outside the IPS to make improved blocking decisions or to modify the blocking rule set.
- Content awareness: Should be able to inspect and classify inbound executables and other similar file types, such as PDF and Microsoft Office files.
- Agile engine: Should support upgrade paths for the integration of new information feeds and new techniques to address future threats.
Importantly, the NGIPS does not include traditional enterprise network firewall capabilities. Many organizations will benefit from a security system that combines high performing network inspection and control functions, such as a Next-Generation Firewall (NGFW). However, it’s also clear such an offering isn’t universally applicable. According to Gartner1, “the high end of the security market will tend to continue to use separate firewalls and IPSs, driven by complexity, desire for ‘defense in depth’ and network operational considerations.” . This “Agile Security” strategy offers security teams a high degree of flexibility in deployment decisions, as well as the potential for significant capital and operational expense savings.
What is a Next Generation IPS?
- Inline, bump-in-the-wire configuration: Should never disrupt network operations.
- Standard first-generation IPS capabilities: Should support vulnerability-and threat-facing signatures.
- Application awareness and full-stack visibility: Should identify applications and enforce network security policy at the application layer.
- Context awareness: Should bring information from sources outside the IPS to make improved blocking decisions or to modify the blocking rule set.
- Content awareness: Should be able to inspect and classify inbound executables and other similar file types, such as PDF and Microsoft Office files.
- Agile engine: Should support upgrade paths for the integration of new information feeds and new techniques to address future threats.
Importantly, the NGIPS does not include traditional enterprise network firewall capabilities. Many organizations will benefit from a security system that combines high performing network inspection and control functions, such as a Next-Generation Firewall (NGFW). However, it’s also clear such an offering isn’t universally applicable. According to Gartner1, “the high end of the security market will tend to continue to use separate firewalls and IPSs, driven by complexity, desire for ‘defense in depth’ and network operational considerations.” . This “Agile Security” strategy offers security teams a high degree of flexibility in deployment decisions, as well as the potential for significant capital and operational expense savings.
Inline, Bump-in-the-Wire Configuration
In the event of service disruption from a network IPS device configured for inline operation—perhaps caused by onboard hardware failure, software malfunction, or power loss—in most instances, the network IPS should be configured to “fail open” as not to cause disruption in network connectivity. In this case, ingress and egress interfaces of an interface set are mechanically bridged, thus continuing to pass traffic (without further inspection). Unlike other providers that offer limited or no failopen interfaces, 100% of Sourcefire’s purpose-built 3D Appliances come equipped with fail-open copper and/or fiber interfaces. This often negates the need to purchase expensive inline taps, saving considerable time and money.
Standard, First-Generation IPS Capabilities
Sourcefire is consistently recognized for offering the best protection in the business. Based on the award-winning open source Snort detection engine, which has rapidly become the most widely used IPS detection engine in the world today, Sourcefire has been recognized by NSS Labs as offering the industry’s best overall protection among all major IPS providers for two years running. Results like these are a consequence of the rigorous development methodology employed by the Sourcefire Vulnerability Research Team™ (VRT), which is designed to maximize performance, eliminate false negatives, and minimize false positives.
Inline, Bump-in-the-Wire Configuration
In the event of service disruption from a network IPS device configured for inline operation—perhaps caused by onboard hardware failure, software malfunction, or power loss—in most instances, the network IPS should be configured to “fail open” as not to cause disruption in network connectivity. In this case, ingress and egress interfaces of an interface set are mechanically bridged, thus continuing to pass traffic (without further inspection). Unlike other providers that offer limited or no failopen interfaces, 100% of Sourcefire’s purpose-built 3D Appliances come equipped with fail-open copper and/or fiber interfaces. This often negates the need to purchase expensive inline taps, saving considerable time and money.
Standard, First-Generation IPS Capabilities
Sourcefire is consistently recognized for offering the best protection in the business. Based on the award-winning open source Snort detection engine, which has rapidly become the most widely used IPS detection engine in the world today, Sourcefire has been recognized by NSS Labs as offering the industry’s best overall protection among all major IPS providers for two years running. Results like these are a consequence of the rigorous development methodology employed by the Sourcefire Vulnerability Research Team™ (VRT), which is designed to maximize performance, eliminate false negatives, and minimize false positives.
Application Awareness and Full-Stack Visibility
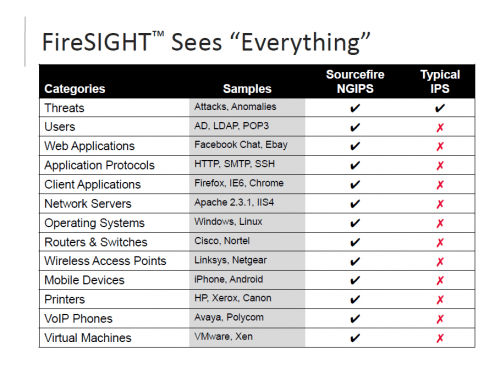
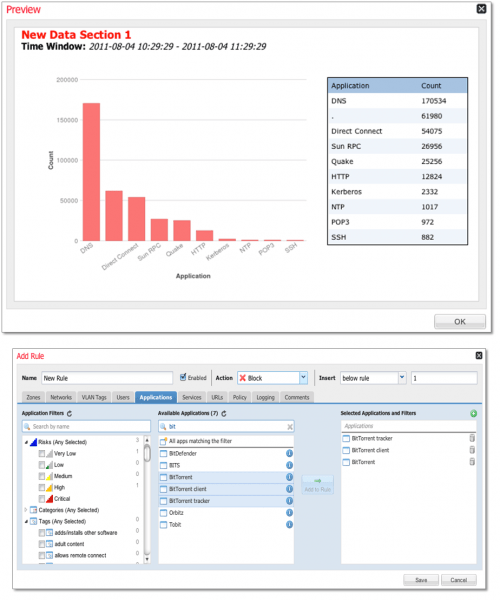
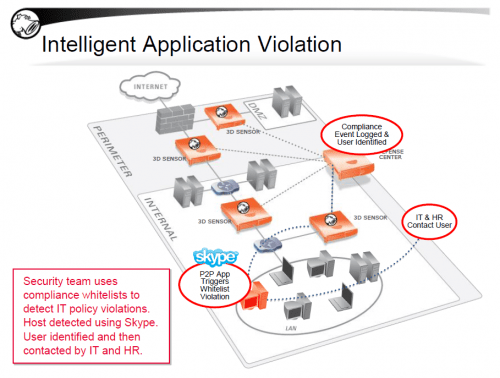
Sourcefire is the first and only IPS provider to offer passive, real-time network intelligence gathering. Sourcefire FireSIGHT™ (formerly Sourcefire RNA®) aggregates rich network intelligence in realtime to enable security administrators to actually enforce corporate acceptable use policies (AUPs) regarding usage of approved operating systems and applications. This can be accomplished within Sourcefire’s NGIPS solution through compliance rules and whitelists. By limiting the use of operating systems and applications that can be used on the network, organizations can improve productivity and reduce risk by minimizing the network’s surface area of attack.
Contextual Awareness
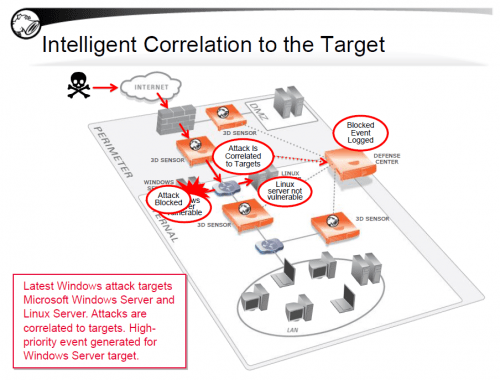
Accurate and timely detection of attacks is an essential requirement of an NGIPS. But equally important is deciding how to respond, or even whether to respond, to those attacks. Context, the complex set of circumstances that surround a specific attack, is a crucial element in assessing the risk posed by an attack, dictating the priority of the response. Sourcefire was the first vendor to deliver commercial IPS solutions that provided essential information about both the behavior and composition of a network under attack, as well as the identification of the specific individuals affected by a security incident.
Application Awareness and Full-Stack Visibility
Sourcefire is the first and only IPS provider to offer passive, real-time network intelligence gathering. Sourcefire FireSIGHT™ (formerly Sourcefire RNA®) aggregates rich network intelligence in realtime to enable security administrators to actually enforce corporate acceptable use policies (AUPs) regarding usage of approved operating systems and applications. This can be accomplished within Sourcefire’s NGIPS solution through compliance rules and whitelists. By limiting the use of operating systems and applications that can be used on the network, organizations can improve productivity and reduce risk by minimizing the network’s surface area of attack.
Contextual Awareness
Accurate and timely detection of attacks is an essential requirement of an NGIPS. But equally important is deciding how to respond, or even whether to respond, to those attacks. Context, the complex set of circumstances that surround a specific attack, is a crucial element in assessing the risk posed by an attack, dictating the priority of the response. Sourcefire was the first vendor to deliver commercial IPS solutions that provided essential information about both the behavior and composition of a network under attack, as well as the identification of the specific individuals affected by a security incident.
Network Awareness
Similarly, contextual data can be used when evaluating attacks for possible response. Sourcefire employs “Impact Flags” to guide security staff in identifying the most pressing attacks. Attacks against devices not susceptible to an exploit—an IIS exploit directed at an Apache server, for example—are of little operational concern. While the attack itself may be recorded to provide information for statistical and historical analysis, the NGIPS set Impact Flags for such events to a low priority. This signals to security analysts and event responders that they can safely ignore the attacks. Experience has demonstrated that this approach reduces actionable events by up to 99%, delivering a dramatic productivity gain. Augmenting the identifying information passively gathered by Sourcefire with specific knowledge about known vulnerabilities further refines the accuracy of Impact Flags. To that end, Sourcefire supports an application-programming interface (API) that facilitates information sharing between vulnerability management systems (and other security and configuration management systems) and the NGIPS. This enables users to share information with virtually any such system, and a fully tested and supported interface for the market-leading QualysGuard® vulnerability management product is available. Contextual data also helps enhance the performance of other network and system security programs. For example, the identification of new systems on a network enables patch management systems to evaluate their status, helping prevent insecure systems from exposing a network to unnecessary risks.
Network Awareness
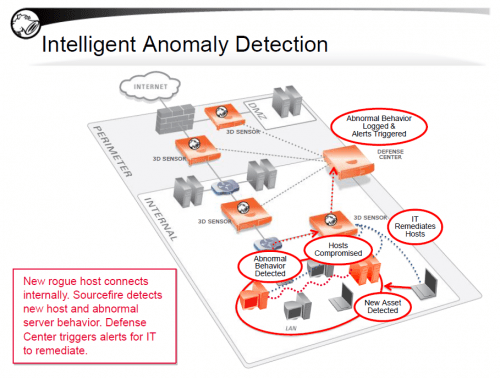
Contextual information about the network provides benefits by enabling proactive responses to developing situations before an attack or breach. Sourcefire NGIPS provides continuous network visibility, including identification of new hosts as they join the network, network and host configuration changes, and compliance with IT policies. The experience of Sourcefire customers has shown the value of incorporating this contextual data into threat response and ongoing operational and administrative activities. For example, if certain operating systems, devices, or applications are not expected to exist in a network, protections related to those systems can be turned off, eliminating unneeded checks. However, if Sourcefire detects the emergence of an unexpected device, relevant protections can automatically be engaged—protecting the devices from attack while security staffers investigate the network addition.
Similarly, contextual data can be used when evaluating attacks for possible response. Sourcefire employs “Impact Flags” to guide security staff in identifying the most pressing attacks. Attacks against devices not susceptible to an exploit—an IIS exploit directed at an Apache server, for example—are of little operational concern. While the attack itself may be recorded to provide information for statistical and historical analysis, the NGIPS set Impact Flags for such events to a low priority. This signals to security analysts and event responders that they can safely ignore the attacks. Experience has demonstrated that this approach reduces actionable events by up to 99%, delivering a dramatic productivity gain. Augmenting the identifying information passively gathered by Sourcefire with specific knowledge about known vulnerabilities further refines the accuracy of Impact Flags. To that end, Sourcefire supports an application-programming interface (API) that facilitates information sharing between vulnerability management systems (and other security and configuration management systems) and the NGIPS. This enables users to share information with virtually any such system, and a fully tested and supported interface for the market-leading QualysGuard® vulnerability management product is available. Contextual data also helps enhance the performance of other network and system security programs. For example, the identification of new systems on a network enables patch management systems to evaluate their status, helping prevent insecure systems from exposing a network to unnecessary risks.
Application Awareness
Sourcefire has long supported the ability to identify the use of applications and has led the market in delivering the ability to detect operating systems, virtual machines, consumer devices like smart phones and tablet computers, VoIP systems, network devices, printers, and more. This data, which is gathered passively in a way that poses no operational risks to the network, makes a broad range of compliance and policy enforcement initiatives possible.
Identity Awareness
This data—available from both Microsoft Active Directory systems and a variety of open standards-based LDAP directory servers—is frequently used to identify the potential victims of an attack, speeding response. For example, most intrusion prevention and detection systems operate solely on the basis of an affected system’s IP address. If a device has been compromised, it’s often essential that security staff communicate with its owner. They may need to speak with the individual to investigate the circumstances of a breach, warn the individual of interruptions in network services, or prompt the person to undertake remediation and restoration efforts. With only an IP address to go on, those activities are delayed. The Sourcefire NGIPS automatically makes the connection between device and owner, and conveniently provides contact information that speeds and simplifies incident workflows.
Application Awareness
Sourcefire has long supported the ability to identify the use of applications and has led the market in delivering the ability to detect operating systems, virtual machines, consumer devices like smart phones and tablet computers, VoIP systems, network devices, printers, and more. This data, which is gathered passively in a way that poses no operational risks to the network, makes a broad range of compliance and policy enforcement initiatives possible.
Identity Awareness
This data—available from both Microsoft Active Directory systems and a variety of open standards-based LDAP directory servers—is frequently used to identify the potential victims of an attack, speeding response. For example, most intrusion prevention and detection systems operate solely on the basis of an affected system’s IP address. If a device has been compromised, it’s often essential that security staff communicate with its owner. They may need to speak with the individual to investigate the circumstances of a breach, warn the individual of interruptions in network services, or prompt the person to undertake remediation and restoration efforts. With only an IP address to go on, those activities are delayed. The Sourcefire NGIPS automatically makes the connection between device and owner, and conveniently provides contact information that speeds and simplifies incident workflows.
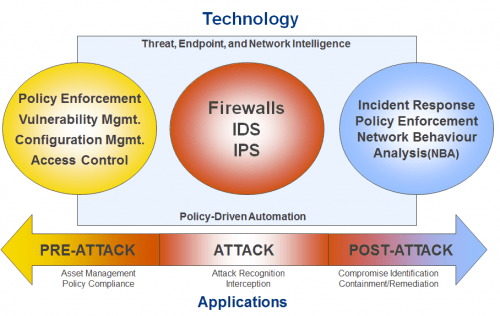
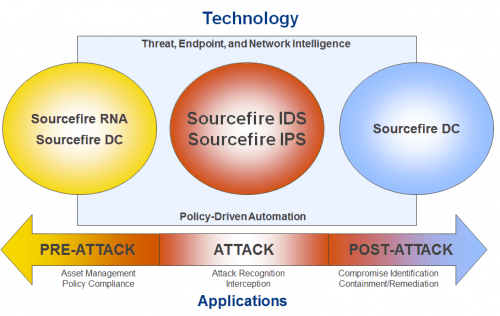
Intelligent Automation
- Automated IPS Tuning
- Network Systems Management and Integration
- Compliance Reporting and Assessment
- Remediation
- Workflow and Incident Response
Content Awareness
The ability to detect threats is by far the most important aspect of any network IPS device. But today’s threats are constantly evolving and more sophisticated than ever. Network security vendors must raise the bar by not only detecting more “traditional” threats (e.g., worms, Trojans, spyware, buffer overflows, denial-of-service attacks), but also threats embedded in “content,” such as Adobe PDFs and Microsoft Office files. Sourcefire leads the industry in preventing threats embedded in content within its NGIPS solution and its comprehensive Snort rules library.
Intelligent Automation
- Automated IPS Tuning
- Network Systems Management and Integration
- Compliance Reporting and Assessment
- Remediation
-
Workflow and Incident Response
Content Awareness
The ability to detect threats is by far the most important aspect of any network IPS device. But today’s threats are constantly evolving and more sophisticated than ever. Network security vendors must raise the bar by not only detecting more “traditional” threats (e.g., worms, Trojans, spyware, buffer overflows, denial-of-service attacks), but also threats embedded in “content,” such as Adobe PDFs and Microsoft Office files. Sourcefire leads the industry in preventing threats embedded in content within its NGIPS solution and its comprehensive Snort rules library.
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
+971 4 3383365
[email protected]
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.
Privacy Overview
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |