Securing Critical Infrastructure and Protecting Industrial Control Systems (ICS)
WHAT IS OT /INDUSTRIAL CONTROL SYSTEMS SECURITY?
Operational technology (OT) describes environments comprising of Industrial Control Systems (ICS). These include Industrial Automated Control Systems (IACS), Supervisory Control and Data Acquisition (SCADA), and Process Control Networks (PCN). Cyber risks pertaining to these environments pose a great threat to all of us. The ramifications of cyber-attacks in these domains could lead to calamitous and catastrophic outcomes.
WHO IS OPERATIONAL TECHNOLOGY SECURITY FOR?
Critical Infrastructure such as Power, Chemical, Water treatment, Aviation, Maritime, and Transportation are some examples of where Operational Technology forms the backbone of their operations.
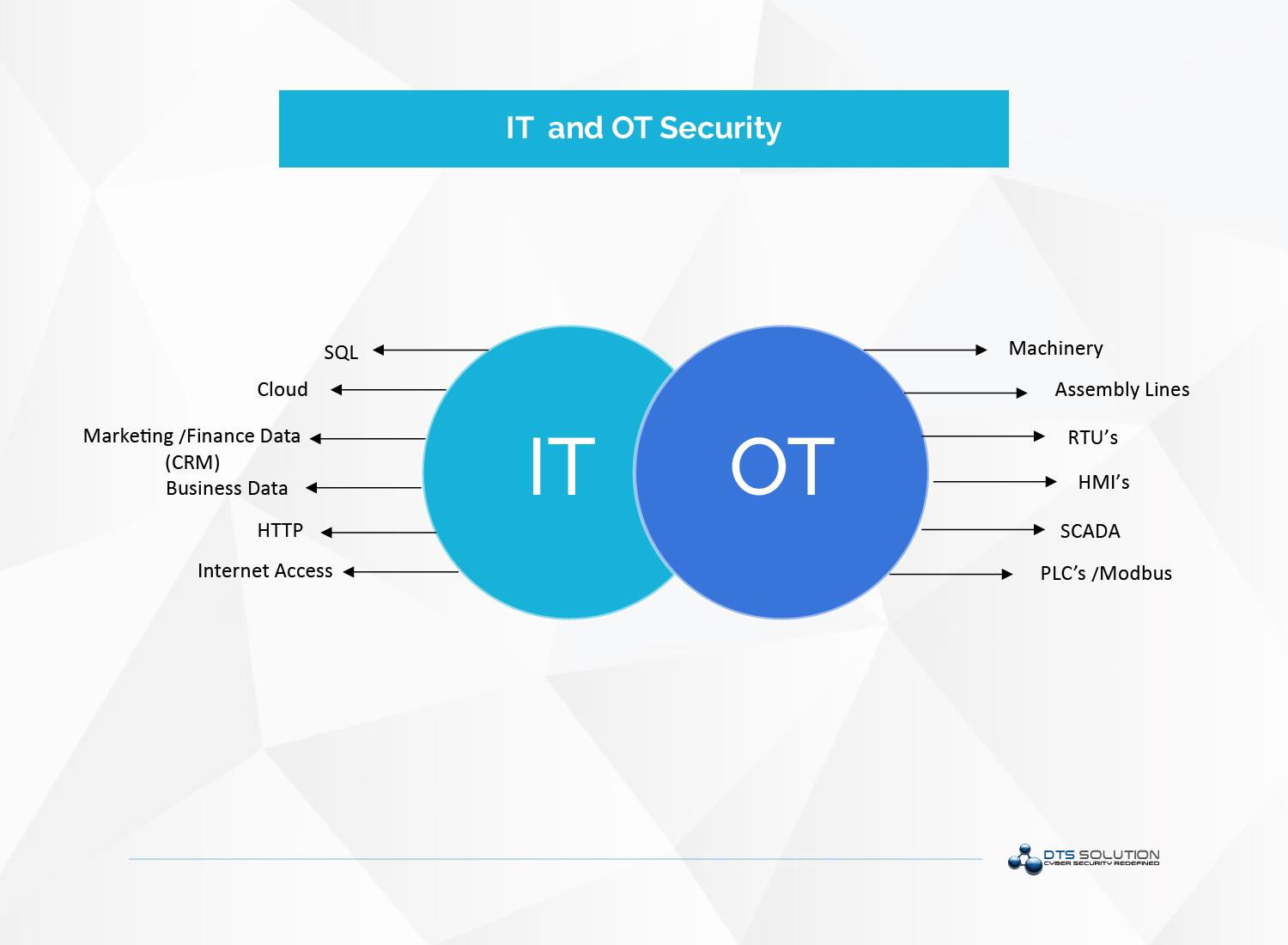
THE BLURRY LINES BETWEEN OPERATIONS AND INFORMATION
Today, OT security mainly stands for the protection of traditional operations and assets from cyber incidents due to the increased connectivity between cyber and physical realms. It involves the detection and mitigation of weak spots and changes in systems that control physical devices such as valves and pumps as well as vulnerabilities stemming from their integration with enterprise software.
Securing Critical Infrastructure and Protecting Industrial Control Systems (ICS)
WHAT IS OT /INDUSTRIAL CONTROL SYSTEMS SECURITY?
Operational technology (OT) describes environments comprising of Industrial Control Systems (ICS). These include Industrial Automated Control Systems (IACS), Supervisory Control and Data Acquisition (SCADA), and Process Control Networks (PCN). Cyber risks pertaining to these environments pose a great threat to all of us. The ramifications of cyber-attacks in these domains could lead to calamitous and catastrophic outcomes.
WHO IS OPERATIONAL TECHNOLOGY SECURITY FOR?
Critical Infrastructure such as Power, Chemical, Water treatment, Aviation, Maritime, and Transportation are some examples of where Operational Technology forms the backbone of their operations.
THE BLURRY LINES BETWEEN OPERATIONS AND INFORMATION
Today, OT security mainly stands for the protection of traditional operations and assets from cyber incidents due to the increased connectivity between cyber and physical realms. It involves the detection and mitigation of weak spots and changes in systems that control physical devices such as valves and pumps as well as vulnerabilities stemming from their integration with enterprise software.
WHY IS OPERATIONAL TECHNOLOGY SECURITY IMPORTANT FOR YOUR ORGANISATION? WHY DOES OT SECURITY MATTER?
Traditionally, OT was an ‘air-gapped’ environment, meaning that it was not connected to external networks or digital technologies. In recent years, what was known as “traditional OT” has started to change, since the rise of the fourth industrial revolution, also known as “Industry 4.0”.
The OT systems that were once isolated from security threats are now vulnerable and exposed. Programmable logic controllers (PLCs), distributed control systems (DCS), human-machine interfaces (HMI), and other field devices are now able to share data and performance metrics with business-analytics processes through standardized protocols. These systems and networks are critical, so any misstep can pose a significant risk to the organization. OT has a high inherent risk as compared to IT systems due to weak access control across physical & logical regions, high functionality-dependent design principles, and complexity of personnel involved in various project stages.
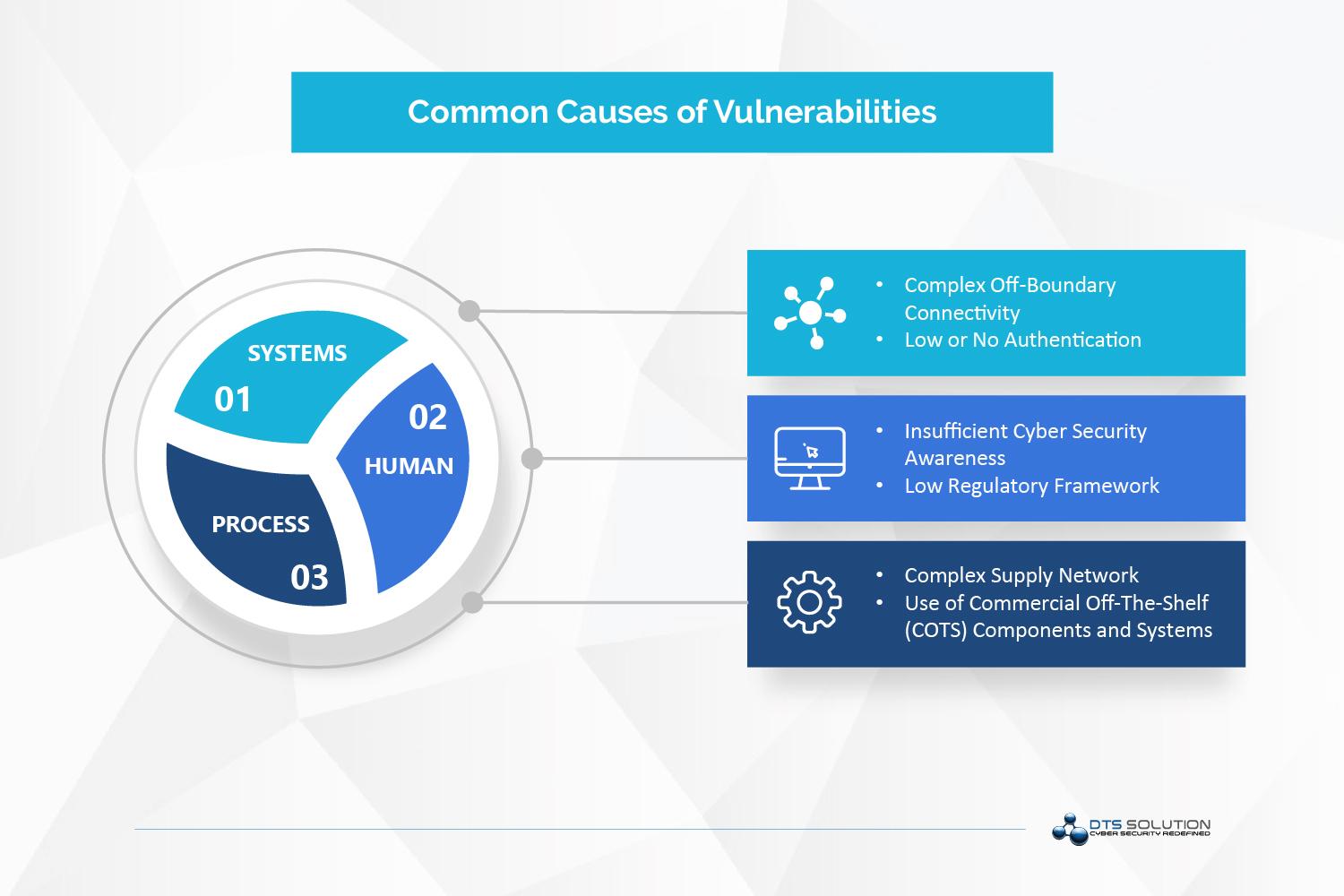
Various vulnerabilities have been exploited by hackers worldwide, resulting in loss of public reputation, equipment damage, leakage of sensitive data and information, and even the lives of citizens. Typical contributing factors of vulnerabilities are:
WHY IS OPERATIONAL TECHNOLOGY SECURITY IMPORTANT FOR YOUR ORGANISATION? WHY DOES OT SECURITY MATTER?
Traditionally, OT was an ‘air-gapped’ environment, meaning that it was not connected to external networks or digital technologies. In recent years, what was known as “traditional OT” has started to change, since the rise of the fourth industrial revolution, also known as “Industry 4.0”.
The OT systems that were once isolated from security threats are now vulnerable and exposed. Programmable logic controllers (PLCs), distributed control systems (DCS), human-machine interfaces (HMI), and other field devices are now able to share data and performance metrics with business-analytics processes through standardized protocols. These systems and networks are critical, so any misstep can pose a significant risk to the organization. OT has a high inherent risk as compared to IT systems due to weak access control across physical & logical regions, high functionality-dependent design principles, and complexity of personnel involved in various project stages.
Various vulnerabilities have been exploited by hackers worldwide, resulting in loss of public reputation, equipment damage, leakage of sensitive data and information, and even the lives of citizens. Typical contributing factors of vulnerabilities are:
DTS SOLUTION CAN HELP YOU
- Help you understand the cyber risk to your operations
- Help you to understand and monitor activities across the OT network
- Provide an approach to prepare for and respond to security incidents
- Improve your security posture
DTS SOLUTION CAN HELP YOU
- Help you understand the cyber risk to your operations
- Help you to understand and monitor activities across the OT network
- Provide an approach to prepare for and respond to security incidents
- Improve your security posture
DTS SOLUTION’s OPERATIONAL TECHNOLOGY SECURITY SERVICES
Organizations can secure their OT environment with the help of our three-stage services approach:
- At the first stage, we perform the gap analysis against the industry best practices (i.e., ISA 62443, NIST 800-53, and ISO 27001). After completing the security gap assessment and gathering the information, it is necessary to understand your OT security baseline status. For this matter, risk assessment services would do best to highlight the existing risks towards the OT environment.
- The next stage of a comprehensive industrial cyber security program is to create a set of well-defined policies and procedures. (Details about the CSMS Framework can be found in chapter # 02 of OT Security Series).
- To go into more technical details and to assess the threats associated with the OT assets we recommend performing vulnerability assessment along with the penetration testing services where applicable. This gives the true picture of where the implemented security controls stand within your environment.
DTS SOLUTION’s OPERATIONAL TECHNOLOGY SECURITY SERVICES
Organizations can secure their OT environment with the help of our three-stage services approach:
- At the first stage, we perform the gap analysis against the industry best practices (i.e., ISA 62443, NIST 800-53, and ISO 27001). After completing the security gap assessment and gathering the information, it is necessary to understand your OT security baseline status. For this matter, risk assessment services would do best to highlight the existing risks towards the OT environment.
- The next stage of a comprehensive industrial cyber security program is to create a set of well-defined policies and procedures. (Details about the CSMS Framework can be found in chapter # 02 of OT Security Series).
- To go into more technical details and to assess the threats associated with the OT assets we recommend performing vulnerability assessment along with the penetration testing services where applicable. This gives the true picture of where the implemented security controls stand within your environment.
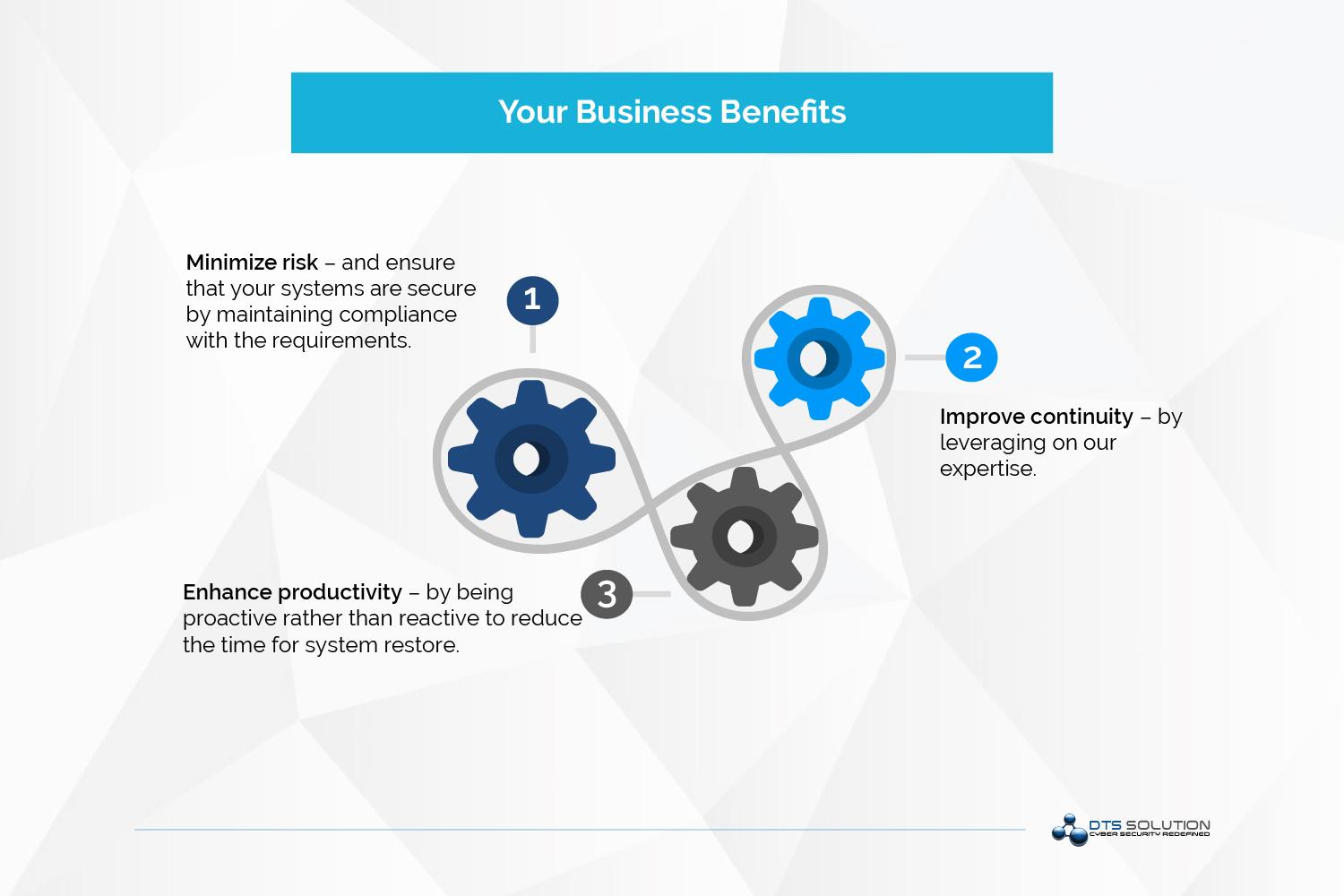
Your Business Benefits
See also: