Introduction
Global dependence on carbon-emitting energy has caused unnatural climate change, leading to many problems, such as global warming, air pollution, and the depletion of non-renewable energy resources. This has made it imperative to seek a more sustainable energy source to help slow down these catastrophic effects. Hence, the gradual leaning towards renewable energy.
Renewable energy refers to energy sources that are replenished naturally and can be used indefinitely. These energy sources include solar, wind, hydro, geothermal, and biomass. The increasing demand for clean and sustainable energy has driven the growth of the renewable energy industry in recent years, providing economic benefits, such as job creation and reduced dependence on foreign oil. Using renewable energy also increases energy security and reduces greenhouse gas emissions.
As renewable energy plants become increasingly reliant on digital technologies and remote-control systems, cybersecurity is becoming an increasingly critical concern. Any cyberattacks or vulnerabilities in a renewable energy plant can disrupt operations, damage equipment, or even pose physical threats to employees or the environment.
Introduction
Global dependence on carbon-emitting energy has caused unnatural climate change, leading to many problems, such as global warming, air pollution, and the depletion of non-renewable energy resources. This has made it imperative to seek a more sustainable energy source to help slow down these catastrophic effects. Hence, the gradual leaning towards renewable energy.
Renewable energy refers to energy sources that are replenished naturally and can be used indefinitely. These energy sources include solar, wind, hydro, geothermal, and biomass. The increasing demand for clean and sustainable energy has driven the growth of the renewable energy industry in recent years, providing economic benefits, such as job creation and reduced dependence on foreign oil. Using renewable energy also increases energy security and reduces greenhouse gas emissions.
As renewable energy plants become increasingly reliant on digital technologies and remote-control systems, cybersecurity is becoming an increasingly critical concern. Any cyberattacks or vulnerabilities in a renewable energy plant can disrupt operations, damage equipment, or even pose physical threats to employees or the environment.
Digitally Enabled Renewable Energy: The Intersection
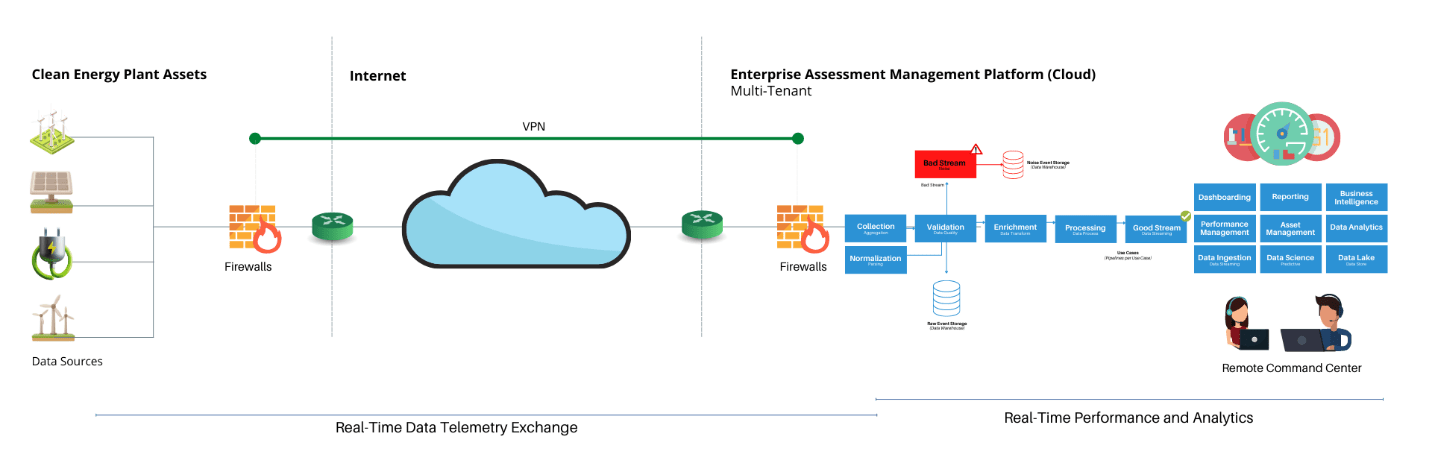
- Cloud Energy Management Systems: SaaS platform that monitors and manages energy flow within a renewable energy system. This includes monitoring the energy production from the energy harvesting devices, controlling the energy conversion devices, and managing energy storage systems. Energy management software can also be integrated with the electrical grid to control energy flow to and from the grid.
- Real-Time Predictive Maintenance: SaaS platform essential to analyzing, monitoring and diagnostic systems data lake to predict using AI/ML when maintenance is needed for energy harvesting, energy conversion, and energy storage devices. This allows for proactive maintenance to be performed, reducing downtime, and improving the system’s overall efficiency.
- Performance Optimization: Platform is used to analyze data from the monitoring and diagnostic systems to optimize the performance of the renewable energy system. This includes optimizing the angle of solar panels, adjusting the speed of wind turbines, and balancing the flow of energy within the system to ensure maximum efficiency.
- Cost Optimization: As part of the data analysis use case of this platform in the renewable energy industry, it also helps to understand and optimize the cost of energy production. This includes determining the most cost-effective times to use energy from the grid or energy storage systems and optimizing the size of the energy storage system to minimize costs.
- Data Analytics: Platform is used to analyze data from the renewable energy system to provide insights into its performance and identify improvement areas. This data can be used to optimize the design of future renewable energy projects.
- Cloud-based Asset Management Systems: Renewable energy companies use cloud-based asset management systems to collect, store, and analyze data from their energy production assets. This data is used to optimize energy production, reduce downtime, and improve efficiency. Cloud-based asset management systems also provide real-time energy production monitoring, allowing companies to identify and resolve any issues that may arise quickly.
- Cloud Connectivity: Renewable energy systems are connected to the cloud, allowing companies to remotely access and control their systems. This connectivity provides increased flexibility and allows companies to respond quickly to changes in energy demand or production.
- Remote Access: Renewable energy companies use remote access to monitor and control their systems from remote locations, reducing the need for on-site personnel and improving efficiency. Remote access also provides increased flexibility, allowing companies to respond quickly to changes in energy demand or production.
Digitally Enabled Renewable Energy: The Intersection

Digital enablement plays a critical role in the renewable energy industry, particularly in managing and optimizing renewable energy systems. Here are some ways network connectivity, enterprise platforms, cloud and big data and is transforming the industry.
- Cloud Energy Management Systems: SaaS platform that monitors and manages energy flow within a renewable energy system. This includes monitoring the energy production from the energy harvesting devices, controlling the energy conversion devices, and managing energy storage systems. Energy management software can also be integrated with the electrical grid to control energy flow to and from the grid.
- Real-Time Predictive Maintenance: SaaS platform essential to analyzing, monitoring and diagnostic systems data lake to predict using AI/ML when maintenance is needed for energy harvesting, energy conversion, and energy storage devices. This allows for proactive maintenance to be performed, reducing downtime, and improving the system’s overall efficiency.
- Performance Optimization: Platform is used to analyze data from the monitoring and diagnostic systems to optimize the performance of the renewable energy system. This includes optimizing the angle of solar panels, adjusting the speed of wind turbines, and balancing the flow of energy within the system to ensure maximum efficiency.
- Cost Optimization: As part of the data analysis use case of this platform in the renewable energy industry, it also helps to understand and optimize the cost of energy production. This includes determining the most cost-effective times to use energy from the grid or energy storage systems and optimizing the size of the energy storage system to minimize costs.
- Data Analytics: Platform is used to analyze data from the renewable energy system to provide insights into its performance and identify improvement areas. This data can be used to optimize the design of future renewable energy projects.
- Cloud-based Asset Management Systems: Renewable energy companies use cloud-based asset management systems to collect, store, and analyze data from their energy production assets. This data is used to optimize energy production, reduce downtime, and improve efficiency. Cloud-based asset management systems also provide real-time energy production monitoring, allowing companies to identify and resolve any issues that may arise quickly.
- Cloud Connectivity: Renewable energy systems are connected to the cloud, allowing companies to remotely access and control their systems. This connectivity provides increased flexibility and allows companies to respond quickly to changes in energy demand or production.
- Remote Access: Renewable energy companies use remote access to monitor and control their systems from remote locations, reducing the need for on-site personnel and improving efficiency. Remote access also provides increased flexibility, allowing companies to respond quickly to changes in energy demand or production.
In the News – No Longer Science Fiction

In the News – No Longer Science Fiction
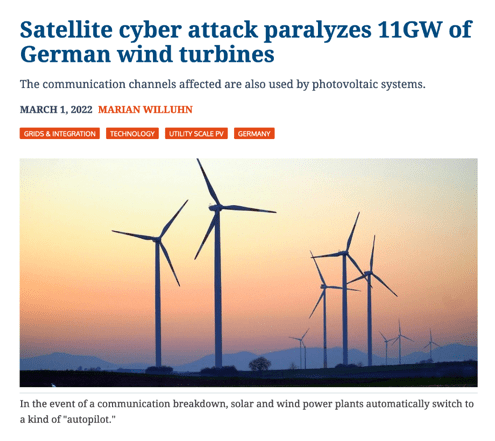

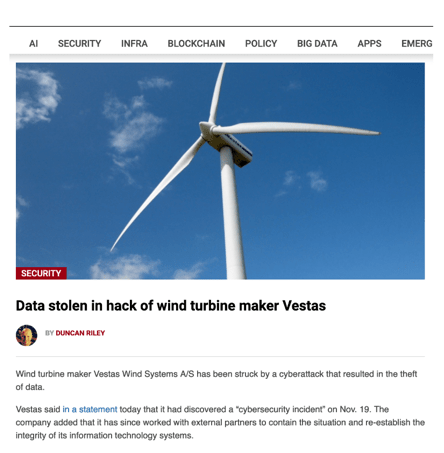
Cyber Threat Scenarios in Sustainable Energy
- A cyber attacker could target a wind farm’s SCADA (Supervisory Control and Data Acquisition) system to take control of the wind turbines, manipulating the wind turbines to increase or decrease power output, which could cause physical damage to the wind turbine. They could also interfere with the control systems of a solar plant or hydro plant, causing the facility to operate in an unstable or unsafe manner.
- A data breach of the cloud-based SaaS Enterprise Asset Management that is used in renewable energy plants for real-time performance monitoring and remote diagnostic. Data breaches in such systems can lead to the loss of sensitive data related to the plant’s operations or the leakage of confidential information that can be used in malicious ways.
- Supply chain attack on a cloud-based SaaS Enterprise Asset Management provider leading to a compromise of plant environment due to VPN connectivity between the sites.
- Ransomware attacks can result in the loss of control over the plant’s operations, leading to a loss of productivity and revenue. To prevent such attacks, renewable energy plants can implement strong network segmentation, data backups, and disaster recovery plans.
- Remote access to plant control systems can be a vulnerability, allowing attackers to gain access to critical systems. To prevent unauthorized access, renewable energy plants can implement two-factor authentication and strong access controls for remote access.
- The use of third-party vendors and contractors can introduce additional cybersecurity risks. Renewable energy plants can mitigate these risks by implementing a vendor management program that includes regular security assessments and contractual provisions that require vendors to comply with the plant’s cybersecurity policies.
- A wind turbine hacked and controlled by a malicious attacker, and able to manipulate the turbine’s control systems remotely. The attacker can use various methods to infiltrate, and one common method would be a targeted phishing email to an onsite operator and infected the operator workstation to gain access to the control system, which would allow them to gain control of the turbine’s systems and manipulate its operation.
Cyber Threat Scenarios in Sustainable Energy
- A cyber attacker could target a wind farm’s SCADA (Supervisory Control and Data Acquisition) system to take control of the wind turbines, manipulating the wind turbines to increase or decrease power output, which could cause physical damage to the wind turbine. They could also interfere with the control systems of a solar plant or hydro plant, causing the facility to operate in an unstable or unsafe manner.
- A data breach of the cloud-based SaaS Enterprise Asset Management that is used in renewable energy plants for real-time performance monitoring and remote diagnostic. Data breaches in such systems can lead to the loss of sensitive data related to the plant’s operations or the leakage of confidential information that can be used in malicious ways.
- Supply chain attack on a cloud-based SaaS Enterprise Asset Management provider leading to a compromise of plant environment due to VPN connectivity between the sites.
- Ransomware attacks can result in the loss of control over the plant’s operations, leading to a loss of productivity and revenue. To prevent such attacks, renewable energy plants can implement strong network segmentation, data backups, and disaster recovery plans.
- Remote access to plant control systems can be a vulnerability, allowing attackers to gain access to critical systems. To prevent unauthorized access, renewable energy plants can implement two-factor authentication and strong access controls for remote access.
- The use of third-party vendors and contractors can introduce additional cybersecurity risks. Renewable energy plants can mitigate these risks by implementing a vendor management program that includes regular security assessments and contractual provisions that require vendors to comply with the plant’s cybersecurity policies.
- A wind turbine hacked and controlled by a malicious attacker, and able to manipulate the turbine’s control systems remotely. The attacker can use various methods to infiltrate, and one common method would be a targeted phishing email to an onsite operator and infected the operator workstation to gain access to the control system, which would allow them to gain control of the turbine’s systems and manipulate its operation.
Typical Critical and Safety Assets to Protect
- Wind turbines
- Control systems
- Power converters
- Transformers
- Solar panels
- Photovoltaic modules
- Meteorological stations
- Weather monitoring equipment
- Environmental sensors
- Inverters
- Transformers
- Monitoring equipment
- Mounting systems
- Electrical switchgear and protection devices
- Batteries and energy storage systems
- Cables and wiring
Typical Critical and Safety Assets to Protect
Here are some typical critical and safety assets that Clean Energy producers should protect to ensure the safety and security of their operations:
- Wind turbines
- Control systems
- Power converters
- Transformers
- Solar panels
- Photovoltaic modules
- Meteorological stations
- Weather monitoring equipment
- Environmental sensors
- Inverters
- Transformers
- Monitoring equipment
- Mounting systems
- Electrical switchgear and protection devices
- Batteries and energy storage systems
- Cables and wiring
Strategies to Improve Cybersecurity in the Renewable Energy Industry
- Implement Strong Access Controls: Renewable energy plants should implement strong access controls to prevent unauthorized access to control systems, enterprise asset management platform, VPNs, telemetry data, and remote diagnostic capabilities. These access controls should include two-factor authentication, biometric authentication, and password policies to ensure that only authorized personnel can access the systems.
- Regular Patch Management: Renewable energy plants should ensure that all control systems and software are kept up-to-date and free from known vulnerabilities through regular patch management.
- Network Segmentation: Network segmentation can be used to isolate the control systems from the plant’s general network, making it more difficult for attackers to gain access. This can also help limit the impact of any successful cyber attacks on the plant’s overall network.
- Implement Secure VPN architectures to ensure only relevant systems are allowed to communicate and follow the “outbound” model. Data is sent from plant to cloud and restrict “inbound” access to landing zones architecture.
- Implement zero trust security architecture to ensure that all access to the renewable energy infrastructure is authenticated, authorized, and continuously monitored, thereby minimizing the risk of unauthorized access, data breaches, and cyber-attacks.
- Implement Firewalls and Intrusion Prevention Systems: Renewable energy plants should implement firewalls and intrusion detection systems to protect the plant’s networks and systems from unauthorized access and malware attacks. Regular security monitoring can help detect and respond to any security incidents quickly.
- Encrypt Data: Renewable energy plants should use encryption to protect sensitive data, such as telemetry data, as it is transmitted from the plant to the cloud. This can help prevent unauthorized access and manipulation of the plant’s data.
- Regular Security Assessment: Renewable energy plants should conduct regular security assessments to identify potential vulnerabilities and implement necessary controls to mitigate any identified risks.
- Disaster Recovery and Business Continuity Planning: Renewable energy plants should have a disaster recovery and business continuity plan in place to ensure the plant can continue to operate even in the event of a security breach or other disruptive event. Implement immutable backups across the workstation and server infrastructure.
- Ensure Cloud SaaS providers in Renewable Energy are vetted for cybersecurity practices, perform TPRM, ensure compliance towards ISO27001:2022 and SOC Type 2 and verify their strong internal governance controls. Supply-chain attacks are real and not just hypothetical anymore.
To learn more about cybersecurity in the renewable energy industry and how DTS can help protect your critical assets, please visit our website or contact us directly for more information.
Strategies to Improve Cybersecurity in the Renewable Energy Industry
If you are a renewable energy operator here are some key technical strategies, you can adopt.
- Implement Strong Access Controls: Renewable energy plants should implement strong access controls to prevent unauthorized access to control systems, enterprise asset management platform, VPNs, telemetry data, and remote diagnostic capabilities. These access controls should include two-factor authentication, biometric authentication, and password policies to ensure that only authorized personnel can access the systems.
- Regular Patch Management: Renewable energy plants should ensure that all control systems and software are kept up-to-date and free from known vulnerabilities through regular patch management.
- Network Segmentation: Network segmentation can be used to isolate the control systems from the plant’s general network, making it more difficult for attackers to gain access. This can also help limit the impact of any successful cyber attacks on the plant’s overall network.
- Implement Secure VPN architectures to ensure only relevant systems are allowed to communicate and follow the “outbound” model. Data is sent from plant to cloud and restrict “inbound” access to landing zones architecture.
- Implement zero trust security architecture to ensure that all access to the renewable energy infrastructure is authenticated, authorized, and continuously monitored, thereby minimizing the risk of unauthorized access, data breaches, and cyber-attacks.
- Implement Firewalls and Intrusion Prevention Systems: Renewable energy plants should implement firewalls and intrusion detection systems to protect the plant’s networks and systems from unauthorized access and malware attacks. Regular security monitoring can help detect and respond to any security incidents quickly.
- Encrypt Data: Renewable energy plants should use encryption to protect sensitive data, such as telemetry data, as it is transmitted from the plant to the cloud. This can help prevent unauthorized access and manipulation of the plant’s data.
- Regular Security Assessment: Renewable energy plants should conduct regular security assessments to identify potential vulnerabilities and implement necessary controls to mitigate any identified risks.
- Disaster Recovery and Business Continuity Planning: Renewable energy plants should have a disaster recovery and business continuity plan in place to ensure the plant can continue to operate even in the event of a security breach or other disruptive event. Implement immutable backups across the workstation and server infrastructure.
- Ensure Cloud SaaS providers in Renewable Energy are vetted for cybersecurity practices, perform TPRM, ensure compliance towards ISO27001:2022 and SOC Type 2 and verify their strong internal governance controls. Supply-chain attacks are real and not just hypothetical anymore.
To learn more about cybersecurity in the renewable energy industry and how DTS can help protect your critical assets, please visit our website or contact us directly for more information.
See also:

