For now, however, unless you take an active interest in your online security, all it would take for your bank accounts, email and social media accounts to be hacked into is for someone to want to do it badly enough.

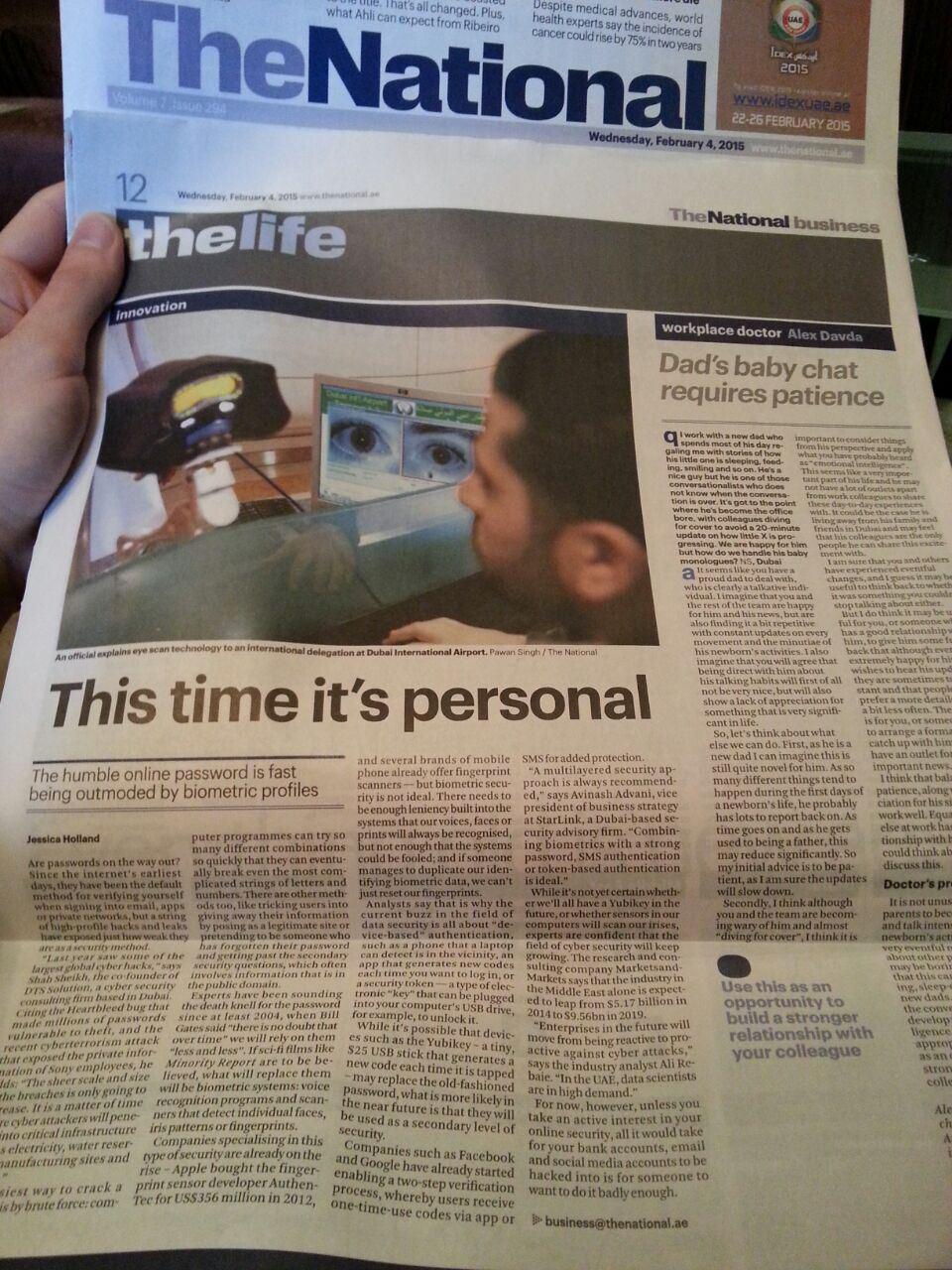
Experts have been sounding the death knell for the password since at least 2004, when Bill Gates said “there is no doubt that over time” we will rely on them “less and less”. If sci-fi films like Minority Report are to be believed, what will replace them will be biometric systems: voice recognition programs and scanners that detect individual faces, iris patterns or fingerprints.
Companies specialising in this type of security are already on the rise – Apple bought the fingerprint sensor developer AuthenTec for US$356 million in 2012, and several brands of mobile phone phone already offer fingerprint scanners – but biometric security is not ideal. There needs to be enough leniency built into the systems that our voices, faces or prints will always be recognised, but not enough that the systems could be fooled; and if someone manages to duplicate our identifying biometric data, we can’t just reset our fingerprints.
Analysts say that is why the current buzz in the field of data security is all about “device-based” authentication, such as a phone that a laptop can detect is in the vicinity, an app that generates new codes each time you want to log in, or a security token – a type of electronic “key” that can be plugged into your computer’s USB drive, for example, to unlock it.
While it’s possible that devices such as the Yubikey – a tiny, $25 USB stick that generates a new code each time it is tapped – may replace the old-fashioned password, what is more likely in the near future is that they will be used as a secondary level of security. Companies like Facebook and Google have already started enabling a two-step verification process, whereby users receive one-time-use codes via app or SMS for added protection.
“A multilayered security approach is always recommended,” says Avinash Advani, vice president of business strategy at StarLink, a Dubai-based security advisory firm. “Combining biometrics with a strong password, SMS authentication or token-based authentication is ideal.”
While it’s not yet certain whether we’ll all have a Yubikey in the future, or whether sensors in our computers will scan our irises, experts are confident that the field of cyber security will keep growing. The research and consulting company MarketsandMarkets says that the industry in the Middle East alone is expected to leap from $5.17 billion in 2014 to $9.56bn in 2019.
“Enterprises in the future will move from being reactive to proactive against cyber attacks,” says the industry analyst Ali Rebaie. “In the UAE, data scientists are in high demand.”
For now, however, unless you take an active interest in your online security, all it would take for your bank accounts, email and social media accounts to be hacked into is for someone to want to do it badly enough.
See also: