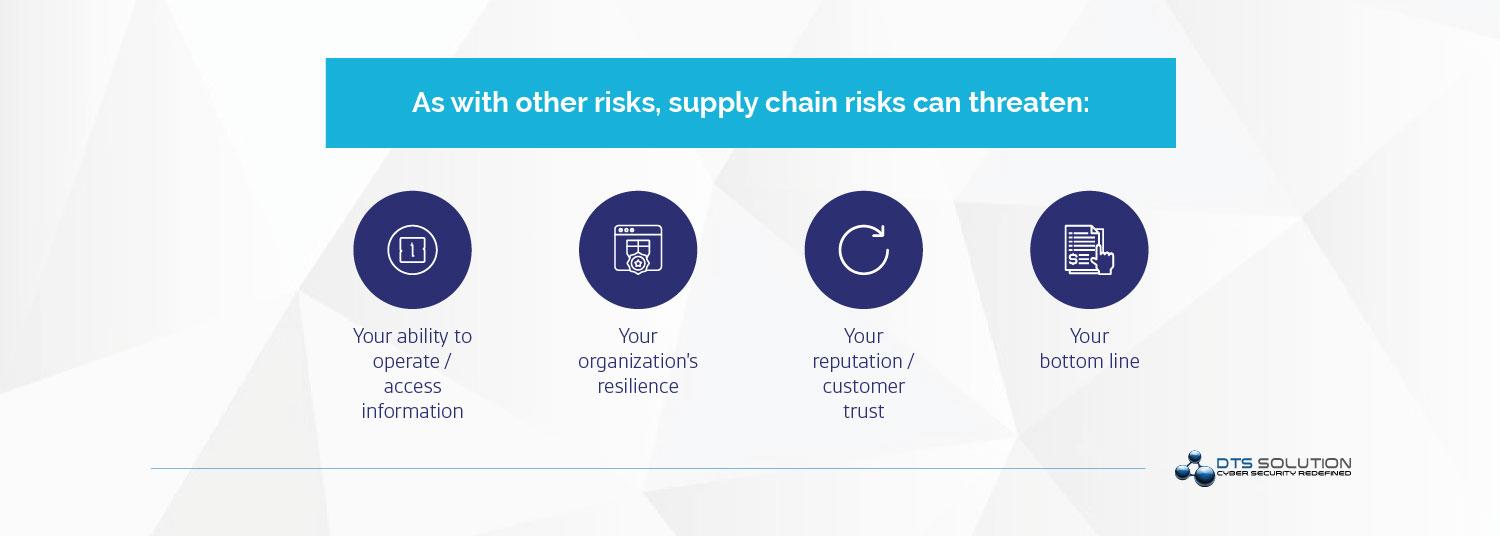
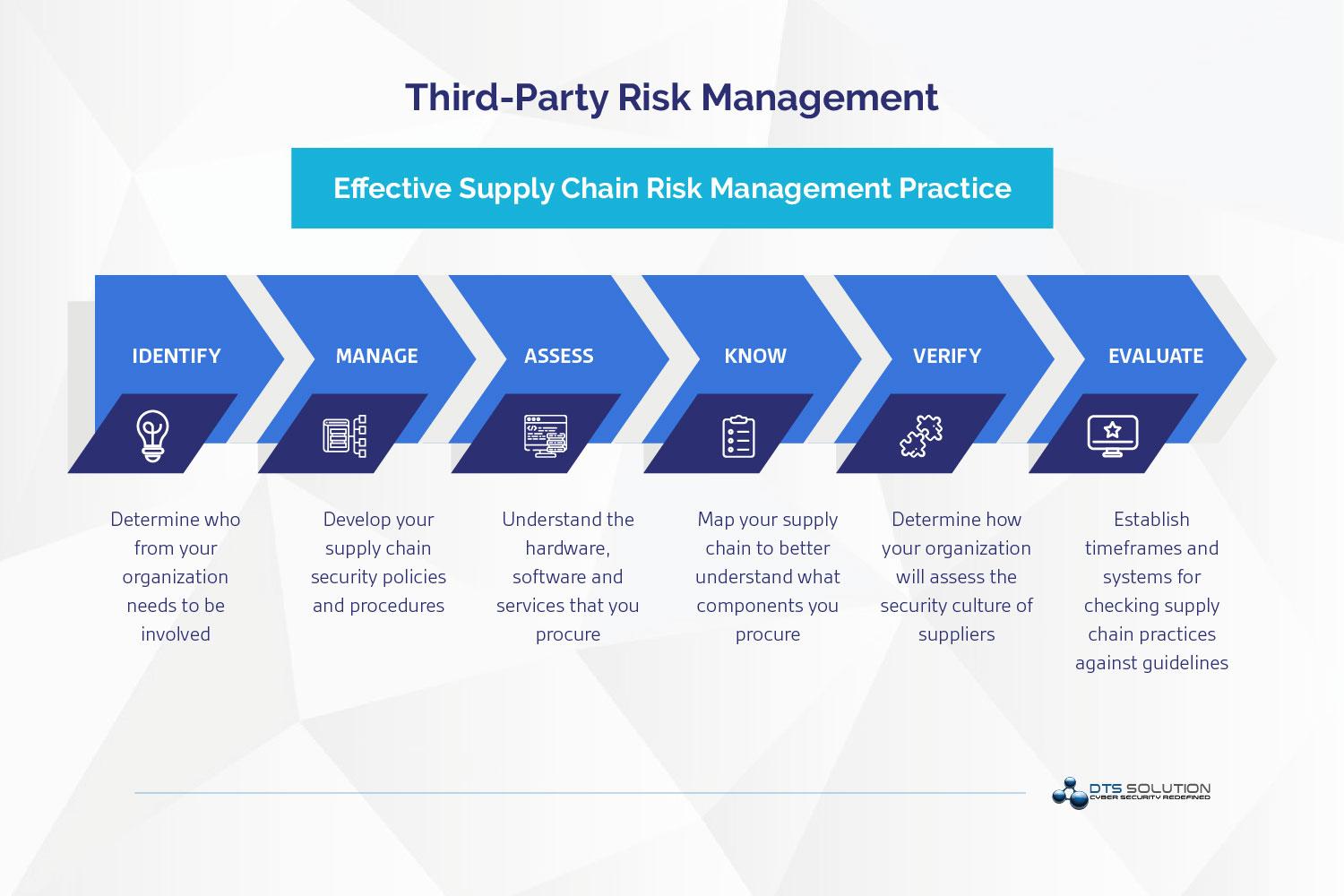
When organization outsource software development or managed services, they must also manage the cybersecurity risks that come with those third parties. Third-Party Risk Management is defined as managing the risk third parties pose to your organization and defining the company’s risk appetite to ensure that these parties you work with are not a source of liability.
The term is often used interchangeably with “vendor risk management” or “supply-chain security” because suppliers and vendors are classified as third parties, where this entity exists outside of your organization.
When organization outsource software development or managed services, they must also manage the cybersecurity risks that come with those third parties. Third-Party Risk Management is defined as managing the risk third parties pose to your organization and defining the company’s risk appetite to ensure that these parties you work with are not a source of liability.
The term is often used interchangeably with “vendor risk management” or “supply-chain security” because suppliers and vendors are classified as third parties, where this entity exists outside of your organization.
Basically, any organization that sells you a product, solution or service puts you at risk. However, many organizations take a siloed approach to managing third-party risks. A finance or IT department may know most of their relevant third parties, but not the complete picture. This is unfortunate because disruptions in one part of the business are likely to impact overall operations.
DTS Solution can help your organization build a comprehensive Third-Party Risk Management (TPRM) security framework.
Basically, any organization that sells you a product, solution or service puts you at risk. However, many organizations take a siloed approach to managing third-party risks. A finance or IT department may know most of their relevant third parties, but not the complete picture. This is unfortunate because disruptions in one part of the business are likely to impact overall operations.
DTS Solution can help your organization build a comprehensive Third-Party Risk Management (TPRM) security framework.
Why Managing Third-Party Risk is Important
Third-party risk management is critical to ensuring that the companies you do business with comply with relevant laws, regulations, and industry standards. Traditionally, third-party management addresses risks arising from financial status, information security standards, system security, or data protection. However, compliance and reputational risks are also important. When illegal or malformed practices by third parties are exposed, consumers can be relentless in defaming or causing reputational damage, and your company can suffer these consequences.
As third-party relationships continue to expand, security frameworks (NIST CSF, ISO27001) and regulators (UAE IA, NCA) has introduced more controls around addressing supply chain security and third-party risks.
To help deal with complexity, third-party risk management processes should include all aspects of advanced supply chain risk management. Therefore, it can be argued that a company needs a third-party risk framework to assess the existing risk objects, and a set of standardized plans for handling identified third-party risk.
Why Managing Third-Party Risk is Important
Third-party risk management is critical to ensuring that the companies you do business with comply with relevant laws, regulations, and industry standards. Traditionally, third-party management addresses risks arising from financial status, information security standards, system security, or data protection. However, compliance and reputational risks are also important. When illegal or malformed practices by third parties are exposed, consumers can be relentless in defaming or causing reputational damage, and your company can suffer these consequences.
As third-party relationships continue to expand, security frameworks (NIST CSF, ISO27001) and regulators (UAE IA, NCA) has introduced more controls around addressing supply chain security and third-party risks.
To help deal with complexity, third-party risk management processes should include all aspects of advanced supply chain risk management. Therefore, it can be argued that a company needs a third-party risk framework to assess the existing risk objects, and a set of standardized plans for handling identified third-party risk.
Key Areas of Third-Party Risk Management
Third-Party Risk Assessment
Procurement performs a rigorous third-party risk assessment (also known as a vendor risk assessment) when a new partner is onboarded during RFP stages. Typically, you gather information from companies through questionnaires or interviews and may involve external rating providers. Such assessments help uncover weaknesses or vulnerabilities between third-party vendors and suppliers, and you can qualify and categorize the third-party risk posed by each company based on the data collected.
Key Areas of Third-Party Risk Management
Third-Party Risk Assessment
Procurement performs a rigorous third-party risk assessment (also known as a vendor risk assessment) when a new partner is onboarded during RFP stages. Typically, you gather information from companies through questionnaires or interviews and may involve external rating providers. Such assessments help uncover weaknesses or vulnerabilities between third-party vendors and suppliers, and you can qualify and categorize the third-party risk posed by each company based on the data collected.
As part of a company’s risk assessment, questions regarding the security controls, industry best practices and industry certifications (ISO27001 and SOC Type1/2) a third-party may hold should be asked. The rule of thumb is that your due diligence process ensures that third parties are compliant and have the same level of ethical conduct as your business. In other words, a company should only do business with vendors and suppliers that have the same level of security controls or higher than the company itself. When a company you’re affiliated with violates the rules or even worse, is chosen as a third-party while lacking controls and has significant risk, your company can suffer serious financial and reputational loss.
Process of Risk Assessment
Tailor Your Vendor Assessments by Identifying Primary Risks Domains
There is no need to send a generic questionnaire irrelevant to the scope of work the potential third-party will provide. Instead, it is best to scope the amount of system access, privileges, and data access a company might need in your system. Based on that, send a customized questionnaire that will address all areas of concern. Things to think about.
- 3rd Party Remote Access
- Data Exchange and Data Processing
- Service Level Agreement
- Incident Reporting and Breach Notification Policy and Procedure
- Security Controls adopted within the 3rd Party
- Site Visit or Walk-Through
Set Your Standards
Crafting questionnaires for the third-party risk assessment is not something that should be copied and pasted from a generic list of questions you find online. It is recommended to define your company’s standards and what you expect from your potential third parties. This way, you can select and write questions in a manner where the questions themselves will set the standards of what kind of answer you expect and require.
Don’t Base Your Assessment on Third-Party Questionnaires
Even though the initial risk assessment of third parties is easiest by using questionnaires, companies need to consider that the results of the questionnaires are only based on what the third-party chooses to disclose. To increase the overall maturity of your third-party risk assessment program, additional tools for continuous monitoring of third parties should be used. These tools provide a necessary insight into the third-party risk posture from the outside in.
Process of Risk Assessment
Tailor Your Vendor Assessments by Identifying Primary Risks Domains
There is no need to send a generic questionnaire irrelevant to the scope of work the potential third-party will provide. Instead, it is best to scope the amount of system access, privileges, and data access a company might need in your system. Based on that, send a customized questionnaire that will address all areas of concern. Things to think about.
- 3rd Party Remote Access
- Data Exchange and Data Processing
- Service Level Agreement
- Incident Reporting and Breach Notification Policy and Procedure
- Security Controls adopted within the 3rd Party
- Site Visit or Walk-Through
Set Your Standards
Crafting questionnaires for the third-party risk assessment is not something that should be copied and pasted from a generic list of questions you find online. It is recommended to define your company’s standards and what you expect from your potential third parties. This way, you can select and write questions in a manner where the questions themselves will set the standards of what kind of answer you expect and require.
Don’t Base Your Assessment on Third-Party Questionnaires
Even though the initial risk assessment of third parties is easiest by using questionnaires, companies need to consider that the results of the questionnaires are only based on what the third-party chooses to disclose. To increase the overall maturity of your third-party risk assessment program, additional tools for continuous monitoring of third parties should be used. These tools provide a necessary insight into the third-party risk posture from the outside in.
Implement Enterprise TPRM Platforms to Support the Process
Using spreadsheets and drives to save third-party risk assessment reports might be feasible for small-sized start-ups, but it is not scalable for larger companies who seek to promote their third-party risk management process to the optimal level. Third-party risk management (TPRM) software is thus a must for many companies to streamline and standardize the process of sending and collecting risk assessment questionnaires. Additionally, many risk management software solutions provide automatic risk identification and remediation suggestions based on the risk assessment responses. Perhaps the biggest benefit of these software solutions is managing your company’s residual risk.
DTS partners with Security Scorecard and CyberGRX to provide organizations like yourself with an enterprise platform to managing the risks of third parties.
Implement Enterprise TPRM Platforms to Support the Process
Using spreadsheets and drives to save third-party risk assessment reports might be feasible for small-sized start-ups, but it is not scalable for larger companies who seek to promote their third-party risk management process to the optimal level. Third-party risk management (TPRM) software is thus a must for many companies to streamline and standardize the process of sending and collecting risk assessment questionnaires. Additionally, many risk management software solutions provide automatic risk identification and remediation suggestions based on the risk assessment responses. Perhaps the biggest benefit of these software solutions is managing your company’s residual risk.
DTS partners with Security Scorecard and CyberGRX to provide organizations like yourself with an enterprise platform to managing the risks of third parties.
The Complexities of Managing Third Parties
Companies may work with hundreds of third-party suppliers and vendors, each with different contract terms, security frameworks, and contract details. With third-party risk management, companies can realistically evaluate third parties based on preset and standardized procedures. However, many companies do not have a comprehensive third-party risk management process and are lacking an enterprise-wide awareness.
When each department manages its own third-party risk from an isolated point of view, it is impossible for a large enterprise to understand all its risk exposures. The situation quickly gets complicated when it comes to managing a wide range of third-party vendors.
Third-Party Risk Management Made Simple
Companies may work with hundreds of third-party suppliers and vendors, each with different contract terms, security frameworks, and contract details. With third-party risk management, companies can realistically evaluate third parties based on preset and standardized procedures. However, many companies do not have a comprehensive third-party risk management process and are lacking an enterprise-wide awareness.
When each department manages its own third-party risk from an isolated point of view, it is impossible for a large enterprise to understand all its risk exposures. The situation quickly gets complicated when it comes to managing a wide range of third-party vendors.
The Complexities of Managing Third Parties
Companies may work with hundreds of third-party suppliers and vendors, each with different contract terms, security frameworks, and contract details. With third-party risk management, companies can realistically evaluate third parties based on preset and standardized procedures. However, many companies do not have a comprehensive third-party risk management process and are lacking an enterprise-wide awareness.
When each department manages its own third-party risk from an isolated point of view, it is impossible for a large enterprise to understand all its risk exposures. The situation quickly gets complicated when it comes to managing a wide range of third-party vendors.
Third-Party Risk Management Made Simple
Companies may work with hundreds of third-party suppliers and vendors, each with different contract terms, security frameworks, and contract details. With third-party risk management, companies can realistically evaluate third parties based on preset and standardized procedures. However, many companies do not have a comprehensive third-party risk management process and are lacking an enterprise-wide awareness.
When each department manages its own third-party risk from an isolated point of view, it is impossible for a large enterprise to understand all its risk exposures. The situation quickly gets complicated when it comes to managing a wide range of third-party vendors.
DTS approach to TPRM
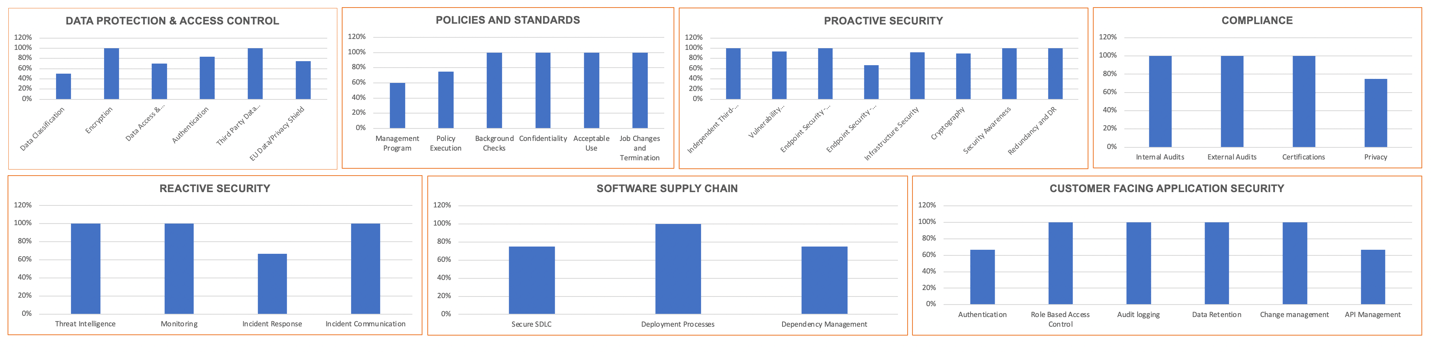
DTS approach to TPRM
DTS has developed a comprehensive cybersecurity framework for TPRM and can support your organization in building such a framework. Another more detailed blog https://www.dts-solution.com/managing-third-party-and-supply-chain-security/ provides technical guidance on managing TPRM in an effective manner.
DTS has built TPRM dashboard for many organizations and a sample can be seen below.

See also: