Telco Security Assessment
Telco Security Introduction
The Telecom sector has grown rapidly. With the extensive growth and the addition of various network services, the threat of compromising security has also grown. The need for expansion of the telecom industry overlooked the security issues. With the sensitive nature of data collection by the telecom service provider, it becomes critical to adopt and implement highly secure cyber strategy.
Telco Security Assessment
Telco Security Introduction
The Telecom sector has grown rapidly. With the extensive growth and the addition of various network services, the threat of compromising security has also grown. The need for expansion of the telecom industry overlooked the security issues. With the sensitive nature of data collection by the telecom service provider, it becomes critical to adopt and implement highly secure cyber strategy.
Why Telco security is important?
Cyberattacks being considered as third highest global risk, the industry must recognize that operators are a major target for attackers. In order to respond to this threat, the mobile ecosystem needs to focus its efforts to prevent as well as respond to the increasing threat.
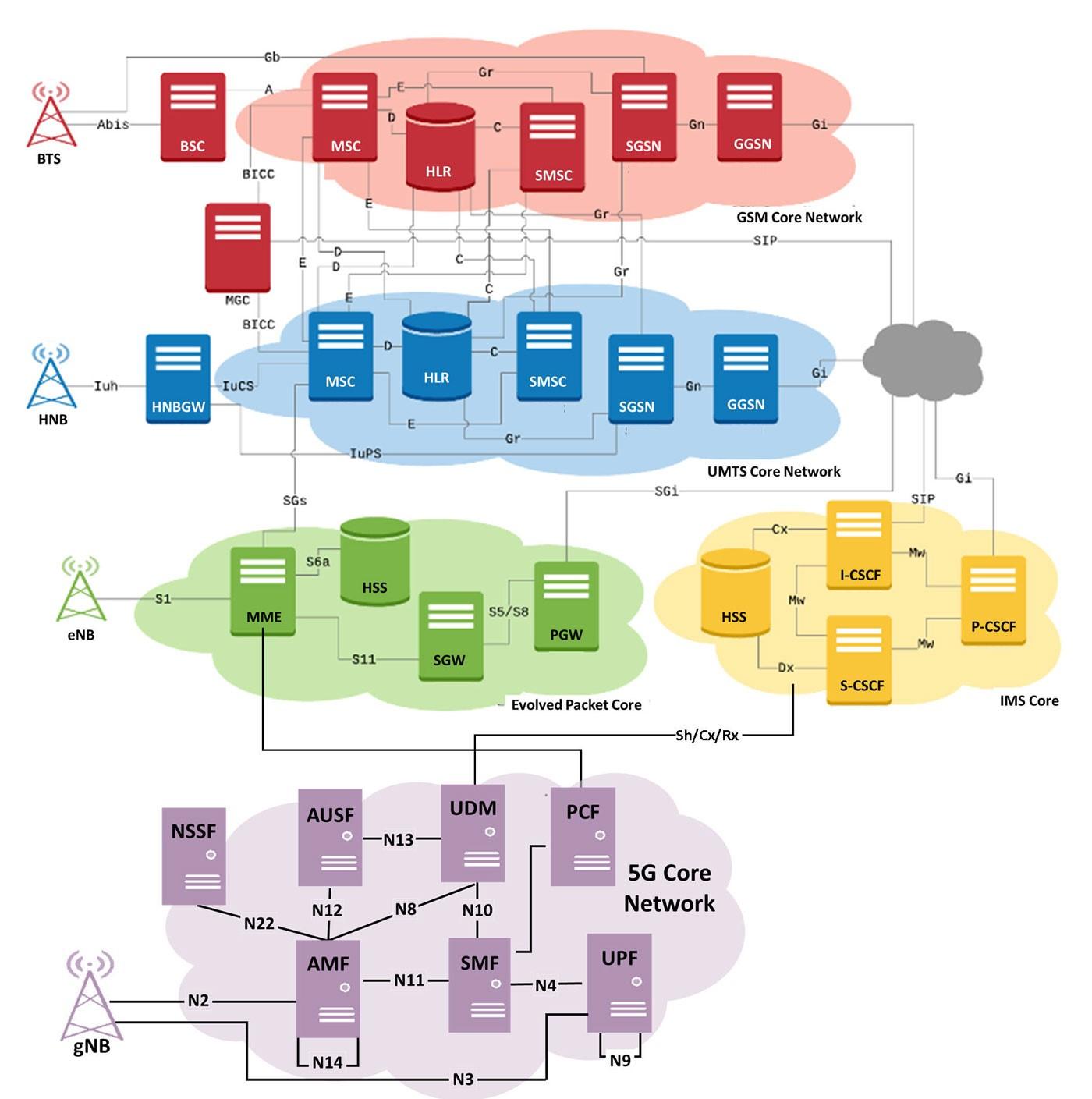
Core network (Network Switching Subsystems – NSS) is the backbone of every telco, which links network elements and handles interconnects with other telecom operators. Fundamental flaws in signaling protocols and configuration errors in network equipment cause severe security threats for telecom ecosystems.
Telecom Security Assessment is an essential step to building an effective signaling vulnerability management process and shielding your core network and subscribers from cyberattacks.
Telco Security Threats Landscape
1. Supply Chain
- Mobile operators rely on numerous external suppliers to deliver infrastructure, products and services. This enables and complements their own. In turn operators' customers, enterprise or consumer, rely on these to manage and enable their lives and businesses. This represents a complex supply chain where downstream links inherit risks and vulnerabilities from suppliers if they are not properly mitigated.
- Attackers do not need to compromise their intended target directly but in many cases can achieve their aim by compromising the supply chain where it is least secure. This potential threat highlights the importance of managing the supply chain holistically and driving out or mitigating insecure elements.
2. Privacy and Data Protection
- Operators must collect, process and store data to operate effectively. This requires the appropriate handling of customer data with required consideration based on the location of the data. Laws that restrict the flow of data reduce the operator’s overarching view of their network, which can cause inefficiencies for the network, and increase the opportunity for an attacker to go undetected. A future threat is that, to protect the privacy and security of citizens’ data, legislative bodies will develop legislation resulting in data flows being restricted.
3. Signaling Service Threats
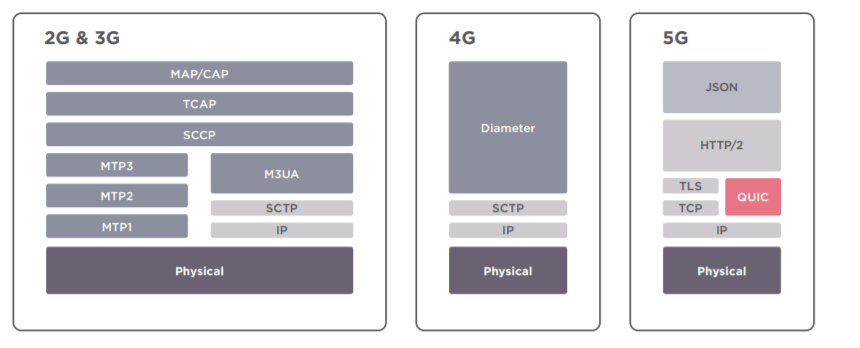
- Signaling exchange is required to establish/maintain a communication channel or session on mobile telecommunications networks as well as allocate resources and manage networks holistically. 2/3G uses SS7 and SIGTRAN and 4G relies on Diameter; all generations use SIP and GTP. Many fundamental services, such as short messaging service (SMS), are managed by these protocols. Many of these protocols are dated and were implemented without an authority model but relied on assumed trust within a closed industry. Couple this insecurity with their essential nature to operate many network functions and any security threats realized against these services will have a high impact.
4. Cloud Threats
- The network perimeter is disappearing, and cloud computing is now used regularly to support operators’ operations either as direct service capability or ‘offline’ capability. The cloud is where network, storage, compute resources, and applications are managed by an external supplier.
- The loss of direct control of such operations, as they are devolved to the cloud provider, may reduce the operator’s level of control over the network performance, optimization, data and quality of services. Additionally, the operator loses the ability to evaluate and mitigate security threats directly, relying solely on contractual or service level agreements with a provider. Therefore, cloud services pose a potential combination of threats relating to network availability, supply chain, and privacy.
5. The Internet of Things Threats
- Most IoT threats come from attackers abusing factory default or poorly configured devices. IoT devices are a desirable target as many of them use commodity components and the volume of devices means many potential victims. An attacker can use the same technique to attack different types of devices regardless of their primary function, leading to a large surface subject to attack with minimal effort on the part of the attacker.
6. Human Threats
- Social engineering attacks: Where the attacker manipulates the user into doing something. These are highly successful due to lack of awareness by the user.
- Misconfiguration: Where devices are left in an insecure default state or configured insecurely by mistake.
- Disregarding processes: Processes are often outlined but not followed. Humans will step outside of a process if it does not suit them or they find it laborious.
- Insider threat: This is when someone internal intentionally acts in a malicious way. These are difficult to monitor for and insider threats pose a major threat as they have insider knowledge of the way the organization is managed.
7. Device Threats
- This threat is being compounded by the hand-off mentality with consumers where older vulnerable devices will remain active in the ecosystem with their 2nd, 3rd or 4th owner
Telco Network based Attacks
- Femto-Cell Based Signaling Attack
- Billing System Flooding for Prepaid Abuse
- SMSC Scanning, Discovery and abuse
- SS7 MSU Bill Artificial Inflation
- VoIP Originated SS7 Injection
- Location Based Services Unauthorized Usage
- HLR Authentication Flooding
- VLR Stuffing
- Illegal Call Redirection
- Fixed Lines Capacity DoS
- SMS to MSC Direct Addressing
- Region or Country Network Instability
- GTP Tunnel disconnection DoS attacks
- Fake Charging attacks
- GRX Subscriber Information Leakage
- Relocation Cancel Attack
-
SGSN and GGSN DoS attacks
Why Telco security is important?
Cyberattacks being considered as third highest global risk, the industry must recognize that operators are a major target for attackers. In order to respond to this threat, the mobile ecosystem needs to focus its efforts to prevent as well as respond to the increasing threat.
Core network (Network Switching Subsystems – NSS) is the backbone of every telco, which links network elements and handles interconnects with other telecom operators. Fundamental flaws in signaling protocols and configuration errors in network equipment cause severe security threats for telecom ecosystems.
Telecom Security Assessment is an essential step to building an effective signaling vulnerability management process and shielding your core network and subscribers from cyberattacks.
Telco Security Threats Landscape
1. Supply Chain
- Mobile operators rely on numerous external suppliers to deliver infrastructure, products and services. This enables and complements their own. In turn operators' customers, enterprise or consumer, rely on these to manage and enable their lives and businesses. This represents a complex supply chain where downstream links inherit risks and vulnerabilities from suppliers if they are not properly mitigated.
- Attackers do not need to compromise their intended target directly but in many cases can achieve their aim by compromising the supply chain where it is least secure. This potential threat highlights the importance of managing the supply chain holistically and driving out or mitigating insecure elements.
4. Cloud Threats
- The network perimeter is disappearing, and cloud computing is now used regularly to support operators’ operations either as direct service capability or ‘offline’ capability. The cloud is where network, storage, compute resources, and applications are managed by an external supplier.
- The loss of direct control of such operations, as they are devolved to the cloud provider, may reduce the operator’s level of control over the network performance, optimization, data and quality of services. Additionally, the operator loses the ability to evaluate and mitigate security threats directly, relying solely on contractual or service level agreements with a provider. Therefore, cloud services pose a potential combination of threats relating to network availability, supply chain, and privacy.
2. Privacy and Data Protection
- Operators must collect, process and store data to operate effectively. This requires the appropriate handling of customer data with required consideration based on the location of the data. Laws that restrict the flow of data reduce the operator’s overarching view of their network, which can cause inefficiencies for the network, and increase the opportunity for an attacker to go undetected. A future threat is that, to protect the privacy and security of citizens’ data, legislative bodies will develop legislation resulting in data flows being restricted.
5. The Internet of Things Threats
- Most IoT threats come from attackers abusing factory default or poorly configured devices. IoT devices are a desirable target as many of them use commodity components and the volume of devices means many potential victims. An attacker can use the same technique to attack different types of devices regardless of their primary function, leading to a large surface subject to attack with minimal effort on the part of the attacker.
3. Signaling Service Threats
- Signaling exchange is required to establish/maintain a communication channel or session on mobile telecommunications networks as well as allocate resources and manage networks holistically. 2/3G uses SS7 and SIGTRAN and 4G relies on Diameter; all generations use SIP and GTP. Many fundamental services, such as short messaging service (SMS), are managed by these protocols. Many of these protocols are dated and were implemented without an authority model but relied on assumed trust within a closed industry. Couple this insecurity with their essential nature to operate many network functions and any security threats realized against these services will have a high impact.
6. Human Threats
- Social engineering attacks: Where the attacker manipulates the user into doing something. These are highly successful due to lack of awareness by the user.
- Misconfiguration: Where devices are left in an insecure default state or configured insecurely by mistake.
- Disregarding processes: Processes are often outlined but not followed. Humans will step outside of a process if it does not suit them or they find it laborious.
- Insider threat: This is when someone internal intentionally acts in a malicious way. These are difficult to monitor for and insider threats pose a major threat as they have insider knowledge of the way the organization is managed.
7. Device Threats
- This threat is being compounded by the hand-off mentality with consumers where older vulnerable devices will remain active in the ecosystem with their 2nd, 3rd or 4th owner
Telco Network based Attacks
- Femto-Cell Based Signaling Attack
- Billing System Flooding for Prepaid Abuse
- SMSC Scanning, Discovery and abuse
- SS7 MSU Bill Artificial Inflation
- VoIP Originated SS7 Injection
- Location Based Services Unauthorized Usage
- HLR Authentication Flooding
- VLR Stuffing
- Illegal Call Redirection
- Fixed Lines Capacity DoS
- SMS to MSC Direct Addressing
- Region or Country Network Instability
- GTP Tunnel disconnection DoS attacks
- Fake Charging attacks
- GRX Subscriber Information Leakage
- Relocation Cancel Attack
-
SGSN and GGSN DoS attacks
Securing Telco Networks
The architecture of 2G, 3G, and 4G networks did not account for the possibility of an intruder inside the network or even one on a roaming network. The model of trust was absolute. Anyone with access to the inter-operator network can gain access to the network of any operator—a serious security flaw.
Several new security features ensure that the subscriber and the network interact in a verifiable and authenticated way:
1. Inter-Operator Security
- Owing to fundamental vulnerabilities in the architecture of the SS7 and Diameter protocols, several security issues have been identified in 2G/3G and 4G networks. Inter-operator security in 5G will be provided by security proxy servers, which are essentially an evolution of 2G, 3G, and 4G signaling firewalls.
2. Privacy
- Prevent disclosure of subscriber identifiers, 5G networks will use the home network public key for asymmetric encryption.
3. Primary Authentication
- Network and devices in 5G are mutually authenticated
4. Secondary Authentication
- Data transmission networks outside the mobile operator domain, such as Wi-Fi calling, undergo secondary authentication.
5. Key Hierarchy
- Implement the updated trust model, 5G employs key separation. This limits the damage if a part of the infrastructure is compromised and protects the integrity of data transmitted by the user.
6. Radio Network Protection
- In the base station (gNB) in 5G, the data processing module (Central Unit, or CU) and the radio module (Distributed Unit, or DU) are separated at the architecture level. The CU and DU interact via a secure interface. Such separation prevents the attacker from breaching the operator's network, even if successful in gaining access to the radio module.
Securing Telco Networks
The architecture of 2G, 3G, and 4G networks did not account for the possibility of an intruder inside the network or even one on a roaming network. The model of trust was absolute. Anyone with access to the inter-operator network can gain access to the network of any operator—a serious security flaw.
Several new security features ensure that the subscriber and the network interact in a verifiable and authenticated way:
1. Inter-Operator Security
- Owing to fundamental vulnerabilities in the architecture of the SS7 and Diameter protocols, several security issues have been identified in 2G/3G and 4G networks. Inter-operator security in 5G will be provided by security proxy servers, which are essentially an evolution of 2G, 3G, and 4G signaling firewalls.
4. Secondary Authentication
- Data transmission networks outside the mobile operator domain, such as Wi-Fi calling, undergo secondary authentication.
2. Privacy
- Prevent disclosure of subscriber identifiers, 5G networks will use the home network public key for asymmetric encryption.
5. Key Hierarchy
- Implement the updated trust model, 5G employs key separation. This limits the damage if a part of the infrastructure is compromised and protects the integrity of data transmitted by the user.
3. Primary Authentication
- Network and devices in 5G are mutually authenticated
6. Radio Network Protection
- In the base station (gNB) in 5G, the data processing module (Central Unit, or CU) and the radio module (Distributed Unit, or DU) are separated at the architecture level. The CU and DU interact via a secure interface. Such separation prevents the attacker from breaching the operator's network, even if successful in gaining access to the radio module.
See also: