- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Data Leakage Prevention
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Data Leakage Prevention (DLP) systems enables your organization to have strict control of information and data in how it is used, transferred and removed.
DLP systems are able to identify, monitor and protect data in use through endpoint actions. DLP systems are also able to protect your intellectual data when data is in motion or in transit referred to as network actions or data that is at rest known as data storage.
The need for Data Leakage Prevention in your Enterprise.....
DTS can assist your organization to identify the right DLP solution to meet your business requirements; solutions that are network, storage or endpoint based all have different characteristics and is important to make the selection.
The need for Data Leakage Prevention in your Enterprise.....
DTS can assist your organization to identify the right DLP solution to meet your business requirements; solutions that are network, storage or endpoint based all have different characteristics and is important to make the selection.
Lumeta - The leaders in network leakage detection.....
Active network discovery solutions enable IT organizations to gain real-time situational awareness of a large, complex geographically disperse networks. This insight allows the enterprise to validate IT policies, analyze the connectivity between assets and networks, uncovering risk patterns and policy weaknesses.
Lumeta Corporation is the developer of IPsonar®, the most widely deployed network discovery solution for large enterprise and government. The company was founded in 2000 as a spin out of Bell Labs, based on the technology developed there to map the Internet. That core technology of the Bell Labs Internet Mapping Project became the foundation of our innovative network discovery solution for large enterprise and government agencies, Lumeta IPsonar.
IPsonar
Lumeta IPsonar® is the world’s most widely deployed network discovery solution for large, geographically distributed organizations. Lumeta’s patented, award-winning network discovery technology discovers and maps every IP asset, host and node on the network, giving CIOs, CSOs and CISOs a clear view of risks and policy violations arising from network changes. Such changes include the addition of new devices, modifications in remote access, changes resulting from IT consolidations, and infrastructure updates.
IPsonar Overview
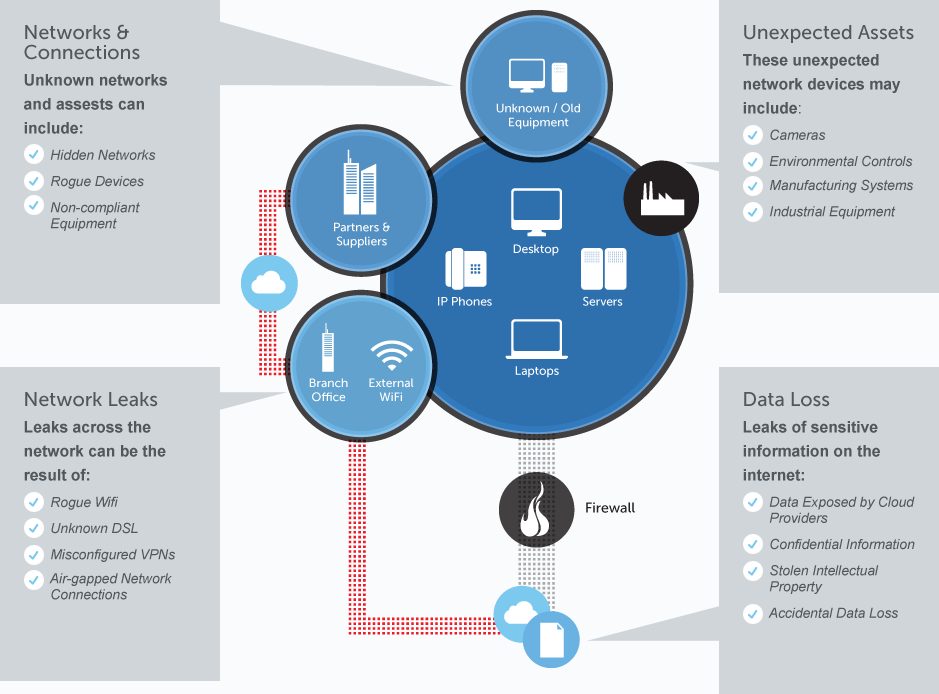
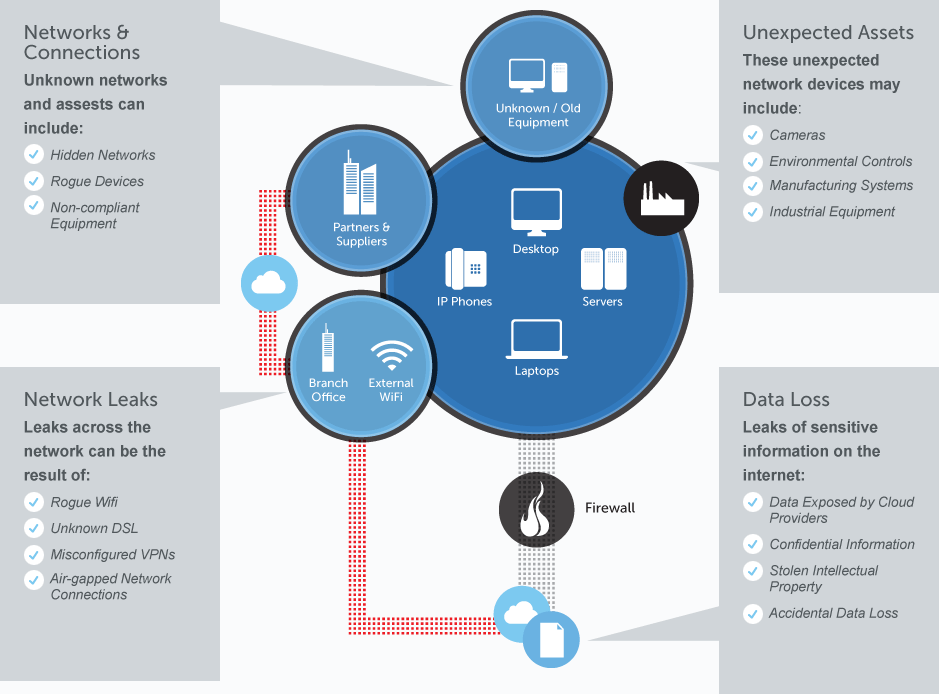
- Network Discovery – Identifies all network address spaces, routing devices and connectivity flows across the network (including “stealth” assets, i.e. hidden devices that do not respond to queries) utilizing advanced multi-protocol discovery technology, and creates a comprehensive route-based topology that identifies a network’s true perimeter. Host Toplogy Visualization / Layer 2: New, optional product module supports layer 2 topology mapping, stealthy device identification, guest network and extranet security, VLAN compliance and Virtual Machine identification.
- Host Discovery – Detects all known and previously unknown network devices by conducting a census of IP addresses across protocols. Flags devices unrecognized by official network inventories for remediation.
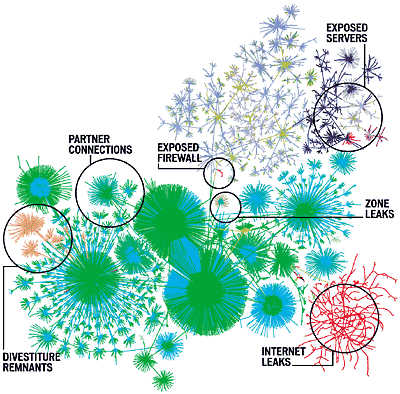
- Leak Discovery – Reveals unauthorized connections between a network and another network, sub-net, or the Internet, and determines whether access is outbound, inbound or both. Leak discovery highlights unknown connections into other organizations (e.g., legacy divestiture connectivity) or to the Internet.
- Device Discovery – Identifies web services, wireless access points and IP applications active on hosts and devices – including those not owned by the client or its employees – pinpointing resources for which tested ports are active. Additionally, Layer 2 discovery matches a device’s unique MAC address with its assigned IP address, providing crucial information for asset management and diagnostics.
IPsonar’s credential-less and agent-less approach minimizes disruption to operations and scales to handle the largest networks. IPsonar is lightweight and safe for use on large networks even during production hours, operating essentially at the level of network “noise” and using only properly formed packets to elicit benign responses. Intuitive reports and color-coded maps generated by IPsonar present micro- and macro-level views of findings. The Lumeta Network Index summarizes scan information from IPsonar in a powerful executive scorecard.
Lumeta IPsonar® is the only product on the market that:
- Provides visibility into every IP asset, host, node, and connection on the network;
- Reports on network “leaks” – unknown, unrestricted pathways into and/or out of an organizations network – that represent policy violations and security threats;
- Provides a comprehensive view of the entire routed infrastructure;
- Measures risk from a network perspective;
- Finds wireless access points that are connected to the wired network, and tests for inbound or outbound “leaks”;
- Provides information extensible to security risk management and network management solutions; and
-
Is lightweight, fast and safe for the world’s largest high-assurance IP networks.
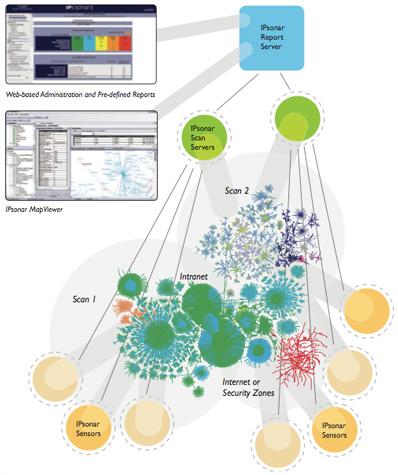
IPsonar Architecture and Delivery Options
IPsonar is delivered as a network appliance, in both 1U Rack Mountable and Laptop formfactors. Lumeta’s IPsonar requires no installation or disruption to operations, and is extremely fast to deploy and scan a network – no matter how far-flung or numerous the resources are. IPsonar is made to handle large data sets as easily as it does small data sets. Thus, IPsonar is a true enterprise application, able to work efficiently in both large and small deployments. IPsonar’s three-tiered architecture is proven at the world’s most complex networks and has been used to scan the entire Internet:
- Sensors. Accurate, complete network scanning is achieved through the use of network entry points called Sensors. These entry points are portable, providing flexibility to address even the most fast-changing networks.
- Scan Servers. These resources are positioned at appropriate points in the network to assure that business applications and even the lowest-speed network links are unaffected by IPsonar network traffic. Multiple scans can be run simultaneously.
- Report Servers. Functioning as the data repository, Report Servers separate report generation from scanning to further reduce IPsonar’s operational footprint. A single remote Report Server can support multiple Scan Servers.
IPsonar
IPsonar Overview
Lumeta IPsonar® is the industry’s only network discovery product which discovers every asset on a network, including assets not currently under management and maps the connectivity between assets and networks to help with issues like Mergers & Acquisitions, IT Compliance, Cybersecurity, Critical Infrastructure Protection, Data Leak Prevention, and Large-scale Network Transformations and Roll-outs.
- Network Discovery – Identifies all network address spaces, routing devices and connectivity flows across the network (including “stealth” assets, i.e. hidden devices that do not respond to queries) utilizing advanced multi-protocol discovery technology, and creates a comprehensive route-based topology that identifies a network’s true perimeter. Host Toplogy Visualization / Layer 2: New, optional product module supports layer 2 topology mapping, stealthy device identification, guest network and extranet security, VLAN compliance and Virtual Machine identification.
- Host Discovery – Detects all known and previously unknown network devices by conducting a census of IP addresses across protocols. Flags devices unrecognized by official network inventories for remediation.
- Leak Discovery – Reveals unauthorized connections between a network and another network, sub-net, or the Internet, and determines whether access is outbound, inbound or both. Leak discovery highlights unknown connections into other organizations (e.g., legacy divestiture connectivity) or to the Internet.
- Device Discovery – Identifies web services, wireless access points and IP applications active on hosts and devices – including those not owned by the client or its employees – pinpointing resources for which tested ports are active. Additionally, Layer 2 discovery matches a device’s unique MAC address with its assigned IP address, providing crucial information for asset management and diagnostics.
IPsonar’s credential-less and agent-less approach minimizes disruption to operations and scales to handle the largest networks. IPsonar is lightweight and safe for use on large networks even during production hours, operating essentially at the level of network “noise” and using only properly formed packets to elicit benign responses. Intuitive reports and color-coded maps generated by IPsonar present micro- and macro-level views of findings. The Lumeta Network Index summarizes scan information from IPsonar in a powerful executive scorecard.
Lumeta IPsonar® is the only product on the market that:
- Provides visibility into every IP asset, host, node, and connection on the network;
- Reports on network “leaks” – unknown, unrestricted pathways into and/or out of an organizations network – that represent policy violations and security threats;
- Provides a comprehensive view of the entire routed infrastructure;
- Measures risk from a network perspective;
- Finds wireless access points that are connected to the wired network, and tests for inbound or outbound “leaks”;
- Provides information extensible to security risk management and network management solutions; and
- Is lightweight, fast and safe for the world’s largest high-assurance IP networks.
IPsonar Architecture and Delivery Options
- Sensors. Accurate, complete network scanning is achieved through the use of network entry points called Sensors. These entry points are portable, providing flexibility to address even the most fast-changing networks.
- Scan Servers. These resources are positioned at appropriate points in the network to assure that business applications and even the lowest-speed network links are unaffected by IPsonar network traffic. Multiple scans can be run simultaneously.
- Report Servers. Functioning as the data repository, Report Servers separate report generation from scanning to further reduce IPsonar’s operational footprint. A single remote Report Server can support multiple Scan Servers.
What is Network Discovery?
As enterprises seek to automate facets of IT security policy enforcement, knowing what’s on the network and ensuring that only devices which are known, managed, and clean are allowed to connect are critical parts of any security plan. The first step in implementing an integrated network security architecture is to assess and document the entire infrastructure including all resources, devices, and connections. The information gleaned from this type of assessment is information on which the majority of security tools will rely.
Why Active Network Discovery?
Active network discovery remains an important component of continuous monitoring well beyond the baselining process. Active network discovery provides the mean to scan IP ranges continuously and be empowered with a solution that will dynamically “learn” more about the environment, eliminating the inherent gap between the perceived network and the actual one. The simple idea being that: you can’t secure what you can’t manage, and you can’t manage what you don’t know about.
What is Network Discovery?
Why Active Network Discovery?
Identifying your Assets through Device Discovery ...
IPsonar and Exonar Toolkit provide the ability to quickly discover, locate and fingerprint unknown and unusual assets on your network, even carrying out some basic vulnerability checks such as which ports are open, allowing customers to quickly secure these devices.
Identifying your Assets through Device Discovery ...
Identifying Network Leaks using IPSonar.......
IPsonar’s patented network leak detection reveals unauthorised connections between the enterprise and another network, between segregated subnets, as well as unwanted connectivity between the network and the Internet, determining whether connectivity is outbound, inbound or both. IPsonar’s network leak detection capabilities are unparalleled in the industry, with the unique ability to find unknown connections into other organisations, such as legacy partner connections or divestiture connectivity.
Identifying Network Leaks using IPSonar.......
IPsonar’s patented network leak detection reveals unauthorised connections between the enterprise and another network, between segregated subnets, as well as unwanted connectivity between the network and the Internet, determining whether connectivity is outbound, inbound or both. IPsonar’s network leak detection capabilities are unparalleled in the industry, with the unique ability to find unknown connections into other organisations, such as legacy partner connections or divestiture connectivity.
Discover, Identify and Secure
We discover, identify and secure the ‘unknowns’ within your IT infrastructure through a comprehensive use of IPSonar technology that discovers networks and devices that are known and unknown. At DTS Solution, our network and device discovery and identification methods and the ability of ensuring adequate security measures are applied to your environment to counteract high risk domains is centered around the following framework.
Discover, Identify and Secure
We discover, identify and secure the ‘unknowns’ within your IT infrastructure through a comprehensive use of IPSonar technology that discovers networks and devices that are known and unknown. At DTS Solution, our network and device discovery and identification methods and the ability of ensuring adequate security measures are applied to your environment to counteract high risk domains is centered around the following framework.
See also:
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
+971 4 3383365
[email protected]
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.