- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Data Encryption
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
One of the most effective ways to eliminate data loss or theft is to encrypt the data as it travels across the network. However, not all network encryption solutions are created equal.
Why Encryption ...?
Encryption doesn’t prevent hacking but it reduces the likelihood that the hacker will be able to read the data that is encrypted. In an encryption scheme, the message or information, referred to as plaintext, is encrypted using an encryption algorithm, turning it into an unreadable ciphertext.This is usually done with the use of an encryption key, which specifies how the message is to be encoded. Any adversary that can see the ciphertext should not be able to determine anything about the original message. An authorized party, however, is able to decode the ciphertext using a decryption algorithm, that usually requires a secret decryption key, that adversaries do not have access to. For technical reasons, an encryption scheme usually needs a key-generation algorithm to randomly produce keys. By encrypting data and information you ensure ‘confidentiality’ of the data transmission from one location to another; by adding ‘integrity’ and ‘authenticity’ you can maintain information triage by ensuring data is not tampered with whilst in transit whilst ensuring the data is coming from a legitimate source.
Why Encryption ...?
Encryption doesn’t prevent hacking but it reduces the likelihood that the hacker will be able to read the data that is encrypted. In an encryption scheme, the message or information, referred to as plaintext, is encrypted using an encryption algorithm, turning it into an unreadable ciphertext.This is usually done with the use of an encryption key, which specifies how the message is to be encoded. Any adversary that can see the ciphertext should not be able to determine anything about the original message. An authorized party, however, is able to decode the ciphertext using a decryption algorithm, that usually requires a secret decryption key, that adversaries do not have access to. For technical reasons, an encryption scheme usually needs a key-generation algorithm to randomly produce keys. By encrypting data and information you ensure ‘confidentiality’ of the data transmission from one location to another; by adding ‘integrity’ and ‘authenticity’ you can maintain information triage by ensuring data is not tampered with whilst in transit whilst ensuring the data is coming from a legitimate source.
Data and Network Encryption with Certes Networks
- Multi-Layer Data Center Security
- Government Solutions
- MPLS Encryption
- Multi-Carrier WAN Encryption
- PCI Compliance
- Regulatory Compliance
- SCADA & Smart Grid Security
- Secure LAN Extension
- Secure Zone Architecture
-
Video & VoIP Encryption
Data and Network Encryption with Certes Networks
- Multi-Layer Data Center Security
- Government Solutions
- MPLS Encryption
- Multi-Carrier WAN Encryption
- PCI Compliance
- Regulatory Compliance
- SCADA & Smart Grid Security
- Secure LAN Extension
- Secure Zone Architecture
-
Video & VoIP Encryption
Multi-Layer Data Center Security
Data Center security has become one of the highest network priorities as data thieves and crime rings seek to penetrate perimeter defenses through increasingly complex attack vectors with alarming success and devastating effects. The security imperative puts CIO’s in the difficult position of having to secure Data Center traffic while at the same time meeting the ever-increasing performance requirements of high-speed applications and synchronous replication. Certes Networks helps CIO’s meet both the security and performance requirements of modern data centers with solutions that provide standards-based encryption and per-frame/packet authentication without impacting application performance, availability or network services. Armed with the industry’s only multi-layer 10 Gigabit Encryptors and Certes TrustNet Manager™, security administrators can achieve the highest level of data center security over any network with line-rate performance up to 10Gbps – without the use of IPSec tunnels!
Multi-Layer Data Center Security
Certes Networks recognizes that being cloud ready is a requirement for any data center technology. Our groundbreaking policy and key management solution, TrustNet Manager, is based on advanced group encryption technology that can extend polices and keys into both private and public clouds as if they were a secure extension of your data center LAN. Not only does this capability allows cloud users to control their own policies and keys, it allows organizations to maintain tight control of security regardless of where they are in their adoption of cloud services and technologies.
Multi-Layer Data Center Security
Data Center security has become one of the highest network priorities as data thieves and crime rings seek to penetrate perimeter defenses through increasingly complex attack vectors with alarming success and devastating effects. The security imperative puts CIO’s in the difficult position of having to secure Data Center traffic while at the same time meeting the ever-increasing performance requirements of high-speed applications and synchronous replication. Certes Networks helps CIO’s meet both the security and performance requirements of modern data centers with solutions that provide standards-based encryption and per-frame/packet authentication without impacting application performance, availability or network services. Armed with the industry’s only multi-layer 10 Gigabit Encryptors and Certes TrustNet Manager™, security administrators can achieve the highest level of data center security over any network with line-rate performance up to 10Gbps – without the use of IPSec tunnels!
Multi-Layer Data Center Security
Certes Networks recognizes that being cloud ready is a requirement for any data center technology. Our groundbreaking policy and key management solution, TrustNet Manager, is based on advanced group encryption technology that can extend polices and keys into both private and public clouds as if they were a secure extension of your data center LAN. Not only does this capability allows cloud users to control their own policies and keys, it allows organizations to maintain tight control of security regardless of where they are in their adoption of cloud services and technologies.
Network Encryption Overview
- Manageability - The ease and simplicity with which the solution is installed, deployed and managed
- Transparency - The degree to which the solution affects network operations and applications
- Flexibility - The solution's compatibility with various combinations of topologies, protocols and applications
Comprehensive protection must excel in all three categories. Many solutions are strong in one area, but weak in others, compromising their overall effectiveness. Only Certes Networks provides you with the manageability, transparency and flexibility needed for complete data protection.
Network Encryption Made Easy
Our solutions combine Certes TrustNet Manager™, a powerful web-based management platform that simplifies security management while preserving network performance and functionality with our Variable Speed Encryptors (VSEs); standards-based, wire-speed encryption appliances. Together, they give you the highest level of data protection at the lowest total cost. TrustNet gives you the power to encrypt your network data wherever, however and whenever you want, without changes or disruptions to your network, your infrastructure, or your operations.
Network Encryption Overview
- Manageability - The ease and simplicity with which the solution is installed, deployed and managed
- Transparency - The degree to which the solution affects network operations and applications
- Flexibility - The solution's compatibility with various combinations of topologies, protocols and applications
Comprehensive protection must excel in all three categories. Many solutions are strong in one area, but weak in others, compromising their overall effectiveness. Only Certes Networks provides you with the manageability, transparency and flexibility needed for complete data protection.
Network Encryption Made Easy
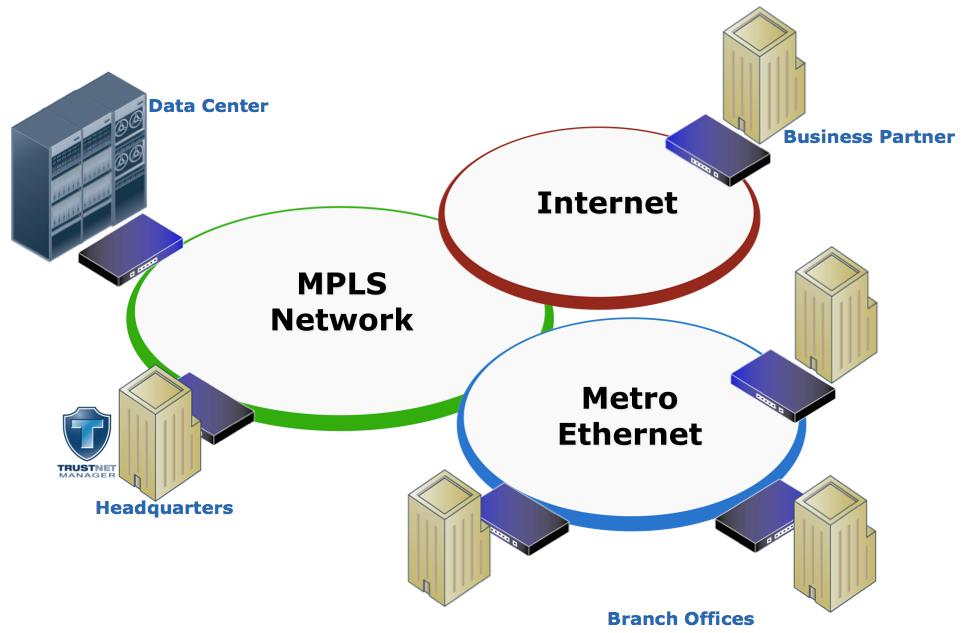
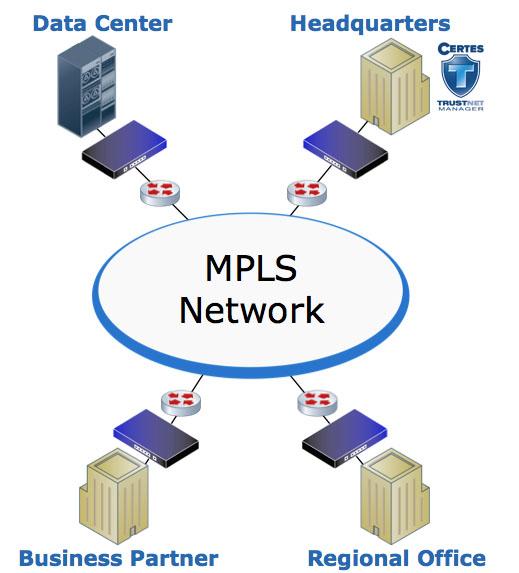
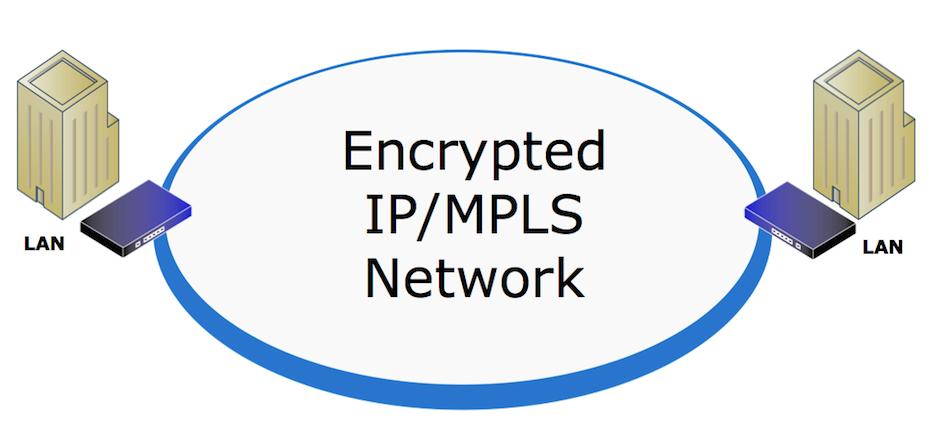
MPLS Encryption - Virtual Privacy vs. Actual Security
While many people believe MPLS and other “virtually private” WAN technologies are secure, the fact is that MPLS and most other WAN technologies offer no inherent data protection, data integrity or protection from mis-configurations. Certes Networks allows you to secure your data over MPLS or other “virtually private” networks without impacting application performance or network services. Our MPLS encryption solutions, powered by Certes TrustNet Manager™, allow organizations to protect their sensitive data without changing the underlying infrastructure, application flows or network services. Our Layer 4 encryption capability even allows you to maintain Netflow/Jflow, and Class of Service (CoS) based routing while encrypting and authenticating data on an on-going basis. TrustNet Manager is a web-based security management platform that simplifies security management while preserving network performance and functionality. This powerful suite of security management applications gives you the ability to secure your MPLS network, achieve regulatory compliance, and reduce the cost of deploying, managing and maintaining the encrypted network. TrustNet Manager makes it possible to secure the MPLS network without losing any of the performance or services that make MPLS the WAN technology of choice for many organizations. This is security without compromise.
MPLS Encryption - Virtual Privacy vs. Actual Security
While many people believe MPLS and other “virtually private” WAN technologies are secure, the fact is that MPLS and most other WAN technologies offer no inherent data protection, data integrity or protection from mis-configurations. Certes Networks allows you to secure your data over MPLS or other “virtually private” networks without impacting application performance or network services. Our MPLS encryption solutions, powered by Certes TrustNet Manager™, allow organizations to protect their sensitive data without changing the underlying infrastructure, application flows or network services. Our Layer 4 encryption capability even allows you to maintain Netflow/Jflow, and Class of Service (CoS) based routing while encrypting and authenticating data on an on-going basis. TrustNet Manager is a web-based security management platform that simplifies security management while preserving network performance and functionality. This powerful suite of security management applications gives you the ability to secure your MPLS network, achieve regulatory compliance, and reduce the cost of deploying, managing and maintaining the encrypted network. TrustNet Manager makes it possible to secure the MPLS network without losing any of the performance or services that make MPLS the WAN technology of choice for many organizations. This is security without compromise.
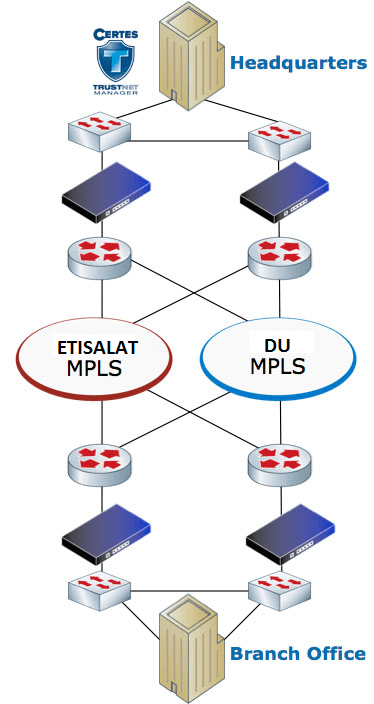
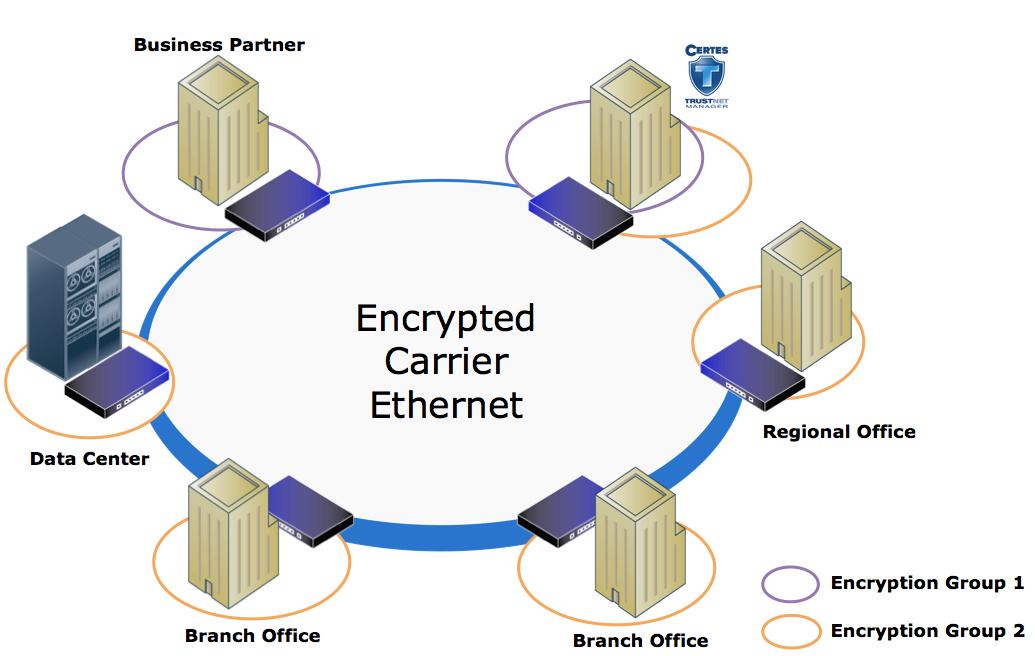
Multi-Carrier WAN Encryption
The solution can also be offered as a managed security service from one of your service providers, without coordination between providers. No other WAN encryption solution offers you this flexibility.
Multi-Carrier WAN Encryption
Certes Networks provides the only solutions that allow you to encrypt multi-carrier networks with a single, provider-neutral network encryption solution. Our solutions provide AES 256 payload encryption and persistent authentication over any combination of networks without impacting availability or service level agreements.
The solution can also be offered as a managed security service from one of your service providers, without coordination between providers. No other WAN encryption solution offers you this flexibility.
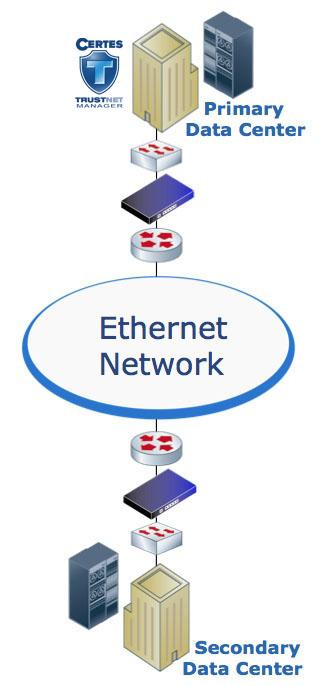
Ethernet Encryption Made Easy
Ethernet networks offer many cost and performance advantages over other networking technologies, but as a shared infrastructure technology, Ethernet has no inherent security. Using Ethernet can save you money, but it exposes your company and customer data to the threat of unauthorized monitoring or theft. Many organizations have recognized the need to proactively protect their data transmissions over Ethernet links, while others find themselves bound by increasing regulatory requirements for data security. The Certes Networks Ethernet Encryption solution mitigates the risk of data loss or theft while maintaining all the benefits of an Ethernet infrastructure. Our Ethernet encryption solutions are powered by Certes TrustNet Manager™, a powerful web-based management platform that simplifies security management while preserving network performance and functionality. TrustNet can be deployed quickly and easily in any Ethernet environment, including point-to-point, point-to-multipoint and multipoint-to-multipoint networks. With encryption speeds ranging from 3Mbps to 10Gbps, our Ethernet Encryption solutions ensure data integrity without affecting the user experience or network performance. TrustNet is highly scalable, quick to install and easy to manage. Unlike many other Layer 2 encryption solutions, TrustNet provides authentication for every Layer 2 frame. Authentication is a critical component of data security as encrypted streams that are not authenticated are vulnerable to modifications and disruptions. If your Layer 2 traffic is important enough to be encrypted, it should also be authenticated.
Ethernet Encryption Made Easy
Ethernet networks offer many cost and performance advantages over other networking technologies, but as a shared infrastructure technology, Ethernet has no inherent security. Using Ethernet can save you money, but it exposes your company and customer data to the threat of unauthorized monitoring or theft. Many organizations have recognized the need to proactively protect their data transmissions over Ethernet links, while others find themselves bound by increasing regulatory requirements for data security. The Certes Networks Ethernet Encryption solution mitigates the risk of data loss or theft while maintaining all the benefits of an Ethernet infrastructure. Our Ethernet encryption solutions are powered by Certes TrustNet Manager™, a powerful web-based management platform that simplifies security management while preserving network performance and functionality. TrustNet can be deployed quickly and easily in any Ethernet environment, including point-to-point, point-to-multipoint and multipoint-to-multipoint networks. With encryption speeds ranging from 3Mbps to 10Gbps, our Ethernet Encryption solutions ensure data integrity without affecting the user experience or network performance. TrustNet is highly scalable, quick to install and easy to manage. Unlike many other Layer 2 encryption solutions, TrustNet provides authentication for every Layer 2 frame. Authentication is a critical component of data security as encrypted streams that are not authenticated are vulnerable to modifications and disruptions. If your Layer 2 traffic is important enough to be encrypted, it should also be authenticated.
Ethernet Encryption: Multipoint-to-Multipoint and Point-to-Multipoint
- Group endpoints together for ease of configuration and scalability
- Encrypt based on VLAN IDs to create secure communities of interest
- Secure multicast application traffic
Our solutions combine TrustNet Manager with our standards-based, wire-speed encryption appliances. Together, they give you the highest level of data protection at the lowest total cost.
Ethernet Encryption: Multipoint-to-Multipoint and Point-to-Multipoint
- Group endpoints together for ease of configuration and scalability
- Encrypt based on VLAN IDs to create secure communities of interest
- Secure multicast application traffic
Our solutions combine TrustNet Manager with our standards-based, wire-speed encryption appliances. Together, they give you the highest level of data protection at the lowest total cost.
Ethernet Encryption: Point-to-Point
- Manageability - The ease and simplicity with which the solution is installed, deployed and managed
- Transparency - The degree to which the solution affects network operations and applications
- Flexibility - The solution's compatibility with various combinations of topologies, protocols and applications
Certes Networks’ Ethernet encryption solutions allow you to protect your data while maintaining your existing network and application performance.
Ethernet Encryption: Point-to-Point
- Quick to install and easy to manage - Installs quickly and is ready to use in minutes
- Transparent to your network - No architecture changes or router upgrades needed
- Wire-speed - Provides full duplex wire-speed encryption
- Low Latency - Will not disrupt any latency sensitive applications
Certes Networks’ Ethernet encryption solutions allow you to protect your data while maintaining your existing network and application performance.
See also:
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.