Tests, evaluations, and assessments are routine processes in an established cybersecurity program. Evaluating and assessing the security of a system gives cybersecurity professionals insights into the efficiency of their cybersecurity efforts. It also helps them identify what areas of their cybersecurity program need to be improved on. Penetration testing, red team assessment, and vulnerability assessment are some of the most common types of security assessment – likewise, compromise assessment.
In this blog, you’ll learn about compromise assessment and the benefits it holds for the success of your cybersecurity program.
Tests, evaluations, and assessments are routine processes in an established cybersecurity program. Evaluating and assessing the security of a system gives cybersecurity professionals insights into the efficiency of their cybersecurity efforts. It also helps them identify what areas of their cybersecurity program need to be improved on. Penetration testing, red team assessment, and vulnerability assessment are some of the most common types of security assessment – likewise, compromise assessment.
In this blog, you’ll learn about compromise assessment and the benefits it holds for the success of your cybersecurity program.

What is Compromise Assessment?
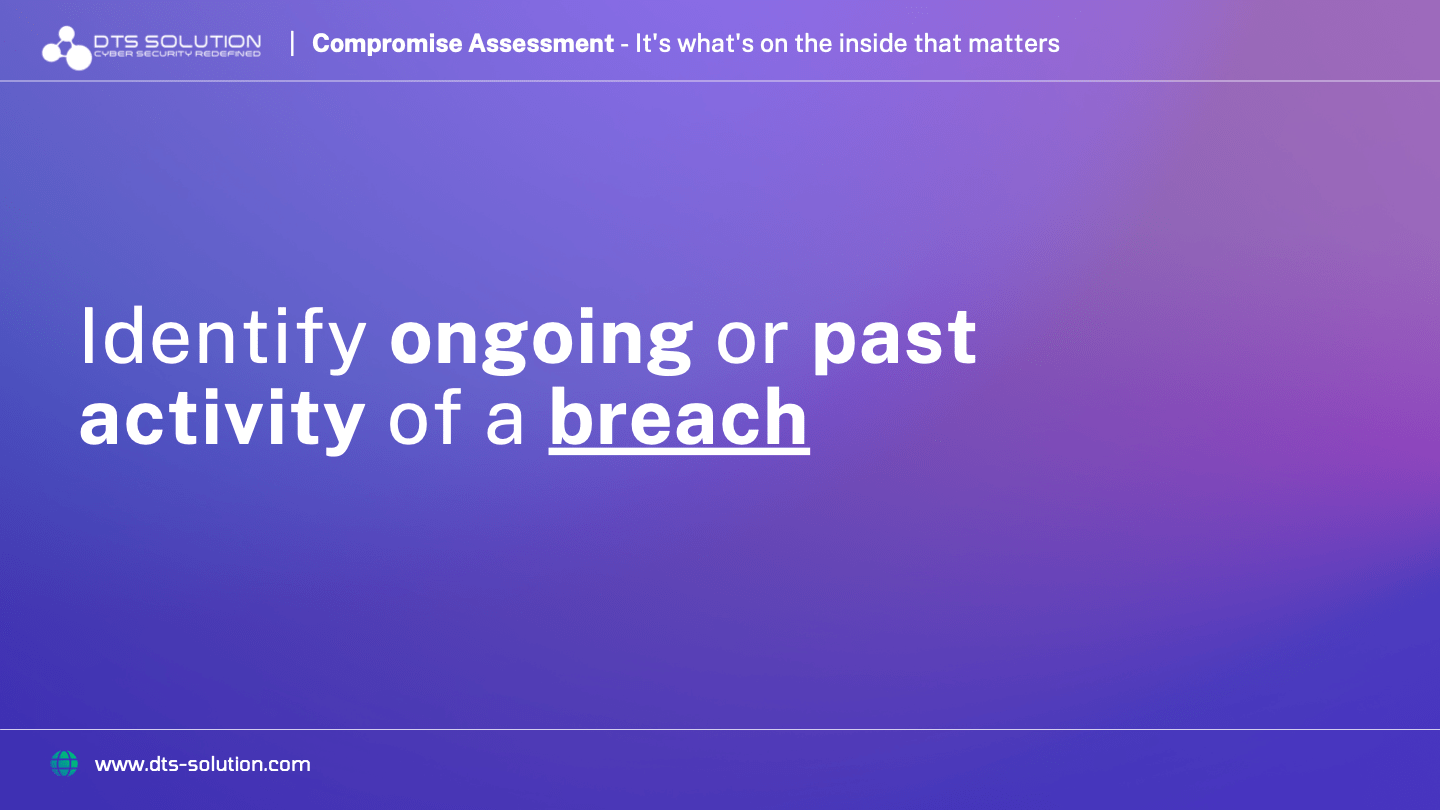
A compromise assessment is a procedure used to find evidence of recent or ongoing attacks in each environment. Compromise assessments are in-depth investigations carried out by skilled teams using cutting-edge tools to delve deeper into their environment to find current or historical attacker activity, as well as existing weaknesses in controls and procedures.
Contrary to legacy practices, compromise assessments are now quicker, more accurate, thorough, and affordable, and have even more functionality and feature thanks to advancements in machine learning and automation technology. Compromise assessments extend beyond vulnerability assessments as they increasingly consider analyses of user behavior in search of anomalies, such as a user logging in from multiple countries in a short amount of time.
To find evidence of attacker activity during compromise assessment, security experts scan an organization’s endpoints (on-premises and cloud deployments), watch network traffic in key locations, examine incoming and outgoing emails, and examine logs from other security devices.
Indicators of compromise (IoCs) and any lingering relics from previous compromises are also searched for in compromise assessments.
What is Compromise Assessment?
A compromise assessment is a procedure used to find evidence of recent or ongoing attacks in each environment. Compromise assessments are in-depth investigations carried out by skilled teams using cutting-edge tools to delve deeper into their environment to find current or historical attacker activity, as well as existing weaknesses in controls and procedures.
Contrary to legacy practices, compromise assessments are now quicker, more accurate, thorough, and affordable, and have even more functionality and feature thanks to advancements in machine learning and automation technology. Compromise assessments extend beyond vulnerability assessments as they increasingly consider analyses of user behavior in search of anomalies, such as a user logging in from multiple countries in a short amount of time.
To find evidence of attacker activity during compromise assessment, security experts scan an organization’s endpoints (on-premises and cloud deployments), watch network traffic in key locations, examine incoming and outgoing emails, and examine logs from other security devices.
Indicators of compromise (IoCs) and any lingering relics from previous compromises are also searched for in compromise assessments.
“How do we know if we have not been breached?” is a common question asked by stakeholders. A conclusive answer can only be given with an in-depth compromise assessment.
Why Perform Compromise Assessment
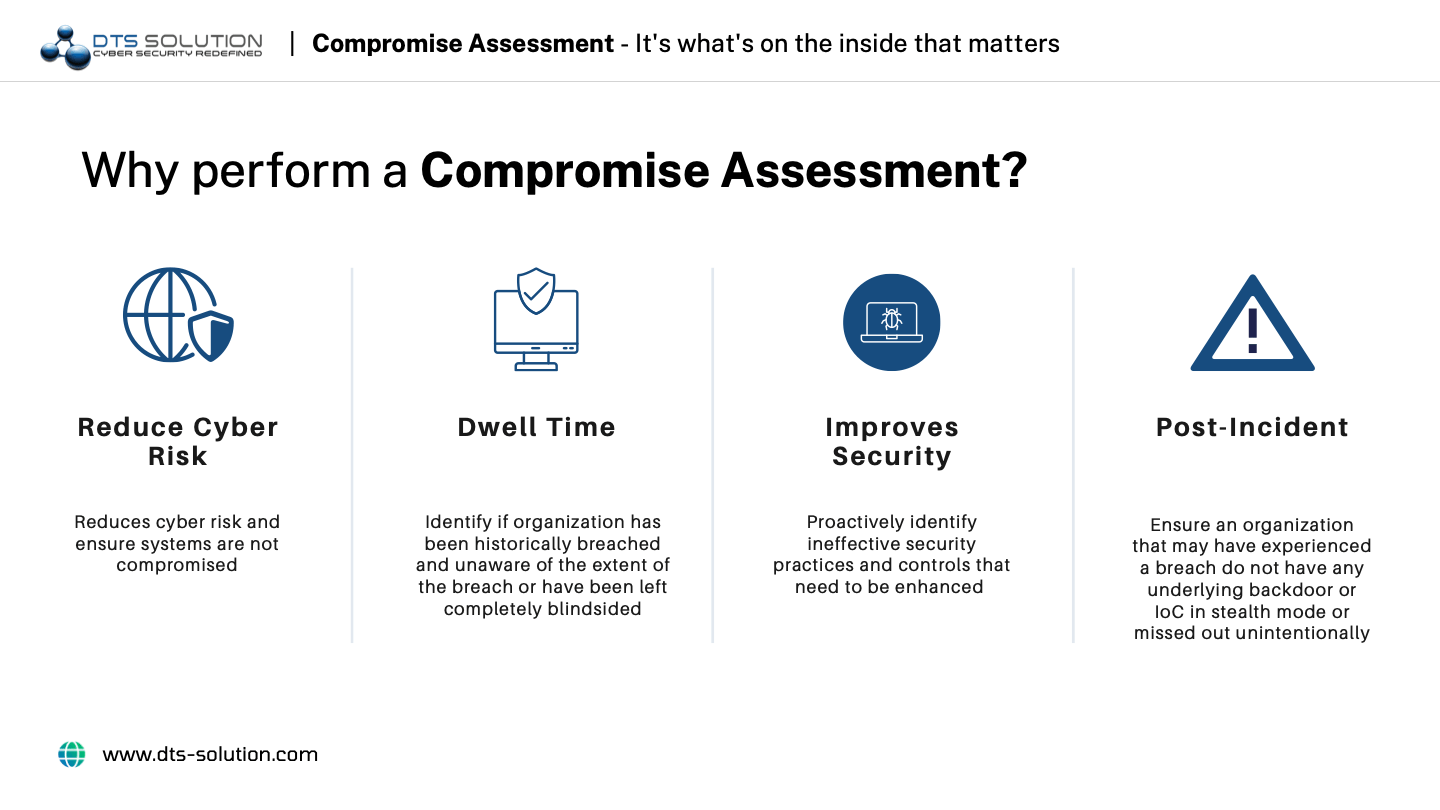
A compromise assessment’s objective is to find evidence of potential threats by identifying indicators of compromise and providing convincing data to support them. For instance, network applications may be sending traffic to an insecure, obfuscated server while using more bandwidth than usual to send and receive it.
Keyloggers or malware designed to steal credentials may be running on mobile and web applications on the organization’s infrastructure, which could compromise networks from within. The goal of a compromise assessment, in this case, is to report the anomalies, and provide credible evidence to back up the claims.
Other objectives of a compromise assessment include:
- Recognizing past intrusion
- Identify an ongoing breach
- Evaluating risk profile for cyber insurance
- Merger / acquisition and infrastructure integration
- Provide analysis to help effectively handle future incidents.
“How do we know if we have not been breached?” is a common question asked by stakeholders. A conclusive answer can only be given with an in-depth compromise assessment.
Why Perform Compromise Assessment?
A compromise assessment’s objective is to find evidence of potential threats by identifying indicators of compromise and providing convincing data to support them. For instance, network applications may be sending traffic to an insecure, obfuscated server while using more bandwidth than usual to send and receive it.
Keyloggers or malware designed to steal credentials may be running on mobile and web applications on the organization’s infrastructure, which could compromise networks from within. The goal of a compromise assessment, in this case, is to report the anomalies, and provide credible evidence to back up the claims.
Other objectives of a compromise assessment include:
- Recognizing past intrusion
- Identify an ongoing breach
- Evaluating risk profile for cyber insurance
- Merger / acquisition and infrastructure integration
- Provide analysis to help effectively handle future incidents.

Benefits of Compromise Assessment
Performing compromise assessments offers many benefits to the cybersecurity posture of an organization. These benefits include the following.
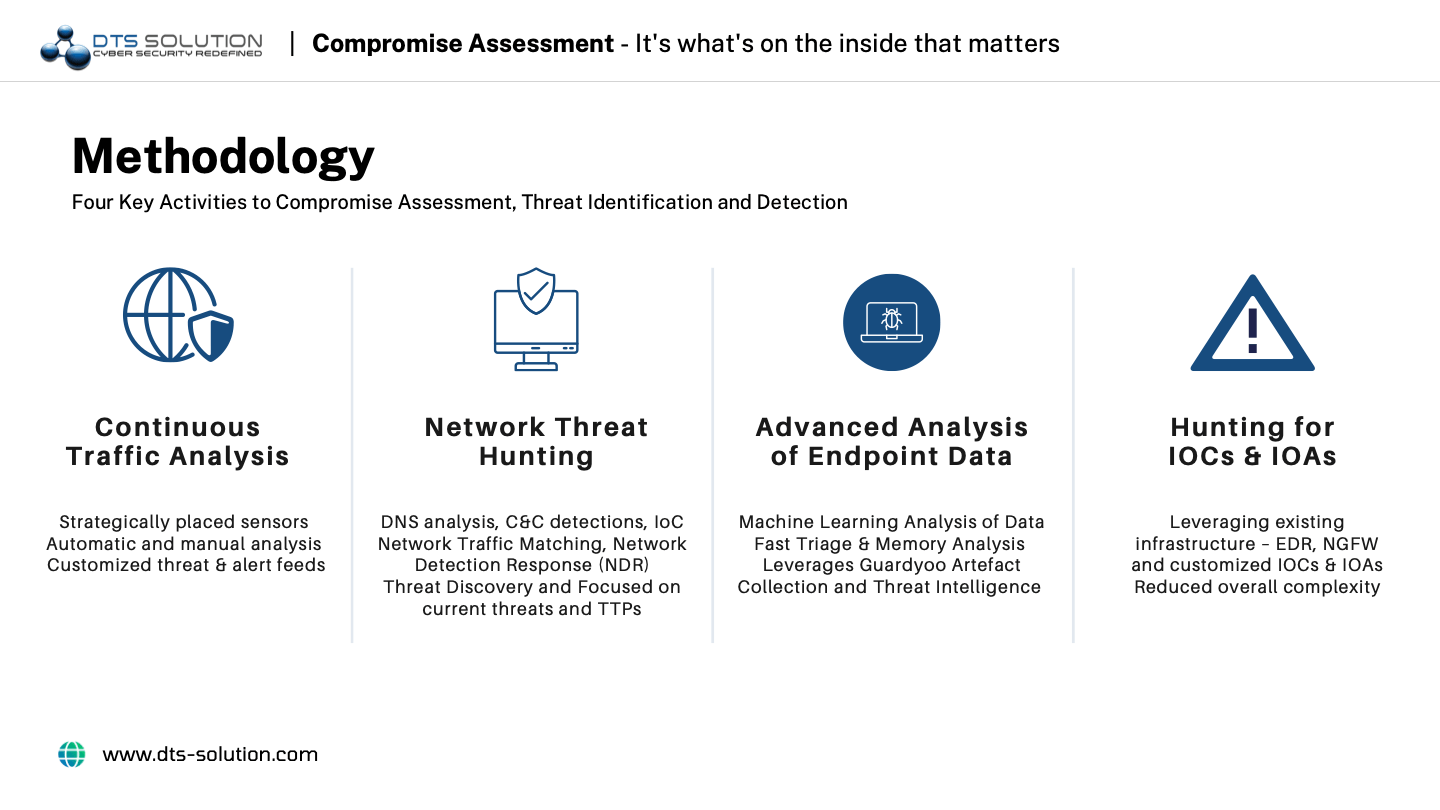
- Improved System Visibility
A compromise assessment’s context and comprehensiveness enable organizations to determine whether threat actors are present or whether they have been breached. This helps organizations understand their system better while understanding the scope of a security breach, assessing how long it might take to restore service, and identifying potential collateral damage. - Improved Security Posture
Proactive identification of ineffective security practices, such as configuration errors and policy conflicts that can leave gaps and put organizations at risk, improves security posture and makes room for the modification of existing policies. A compromise assessment will reveal these flaws and point you in the right direction for fixing them. - Improve Speed in Discovering Threats and Responding to them
The speed with which a vulnerability is discovered can mean the difference between downtime and one that is avoided. Compromise assessments enable security professionals to detect vulnerabilities on time, thereby enabling them to fix the vulnerabilities, and avert potential security breaches.
Other benefits of a compromise assessment include.
- It reduces organization’s risk and attack surface.
- It helps to establish a comprehensive cybersecurity guideline.
- It helps to reduce breaches and control eventual incidents.
Benefits of Compromise Assessment
- Improved System Visibility
A compromise assessment’s context and comprehensiveness enable organizations to determine whether threat actors are present or whether they have been breached. This helps organizations understand their system better while understanding the scope of a security breach, assessing how long it might take to restore service, and identifying potential collateral damage. - Improved Security Posture
Proactive identification of ineffective security practices, such as configuration errors and policy conflicts that can leave gaps and put organizations at risk, improves security posture and makes room for the modification of existing policies. A compromise assessment will reveal these flaws and point you in the right direction for fixing them. - Improve Speed in Discovering Threats and Responding to them
The speed with which a vulnerability is discovered can mean the difference between downtime and one that is avoided. Compromise assessments enable security professionals to detect vulnerabilities on time, thereby enabling them to fix the vulnerabilities, and avert potential security breaches.
- It reduces organization’s risk and attack surface.
- It helps to establish a comprehensive cybersecurity guideline.
- It helps to reduce breaches and control eventual incidents.

Steps Involved in Compromise Assessment
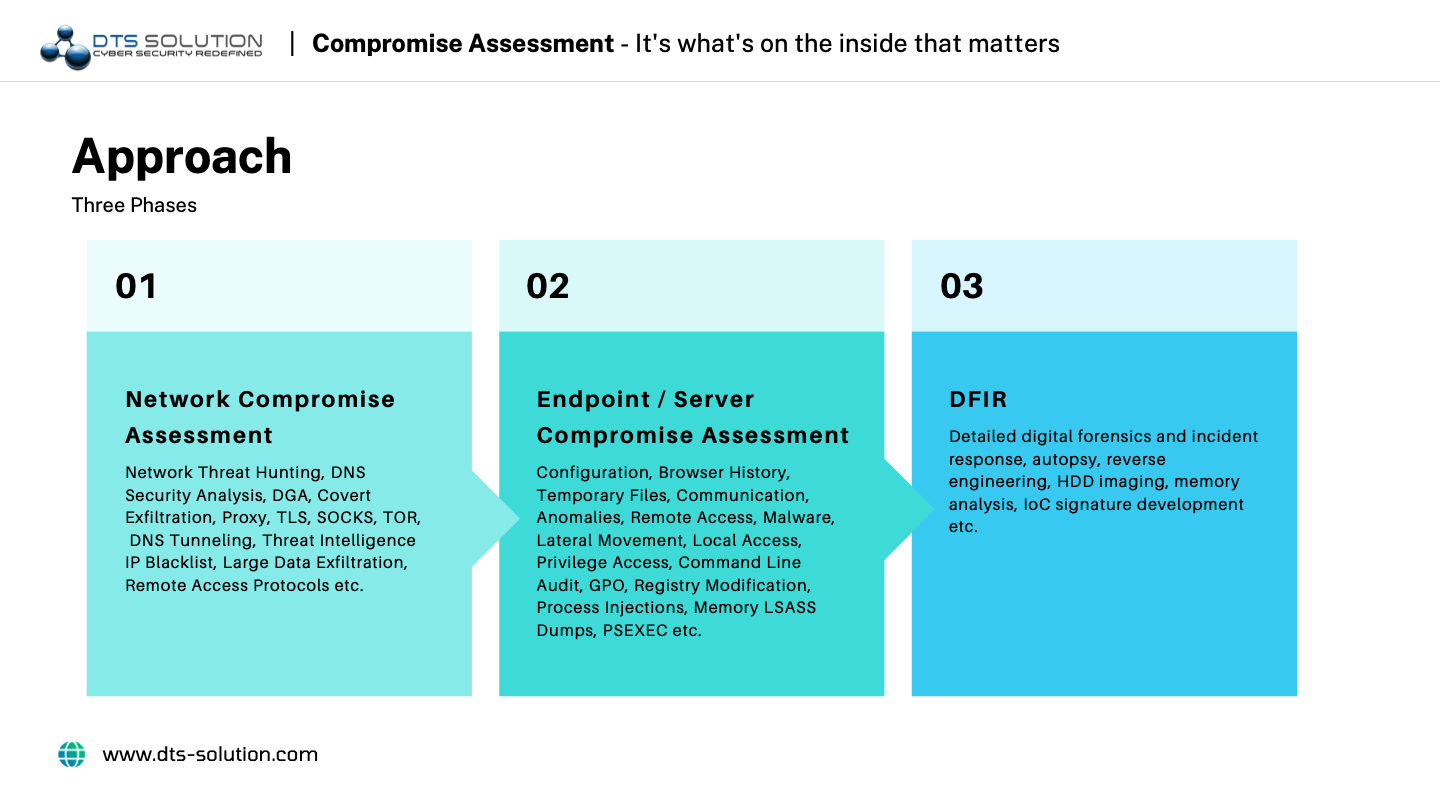
Compromise assessment is basically a four-phase exercise that assesses, analyzes, and provides guidelines for an improved security posture. The steps involved in a compromise assessment are:
1. Assess
The compromise assessment process starts with gathering forensic data and looking for signs of past compromises or potential compromises in the system. This assessment includes scanning all system entities like API endpoints, network traffic, and logs.
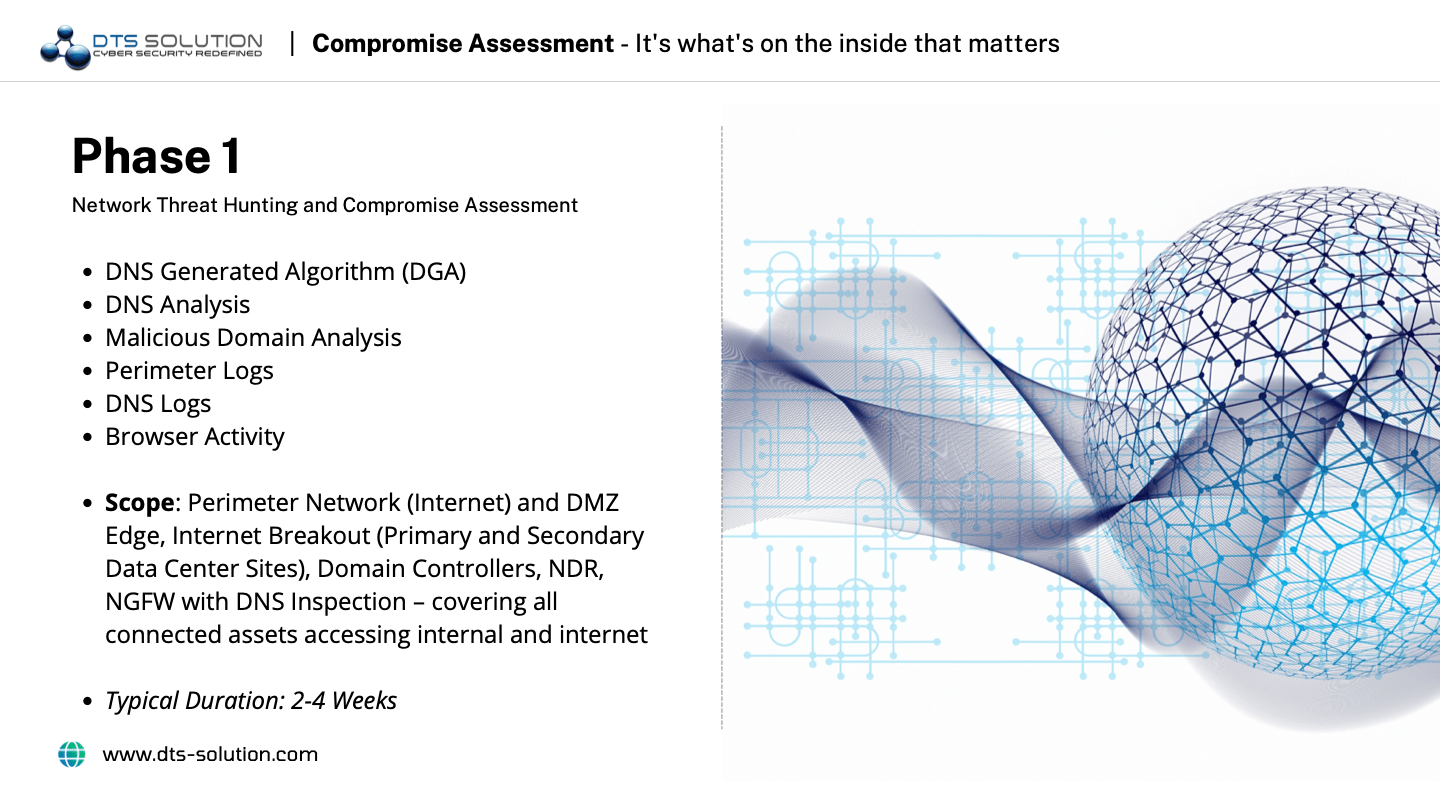
2. Analyze
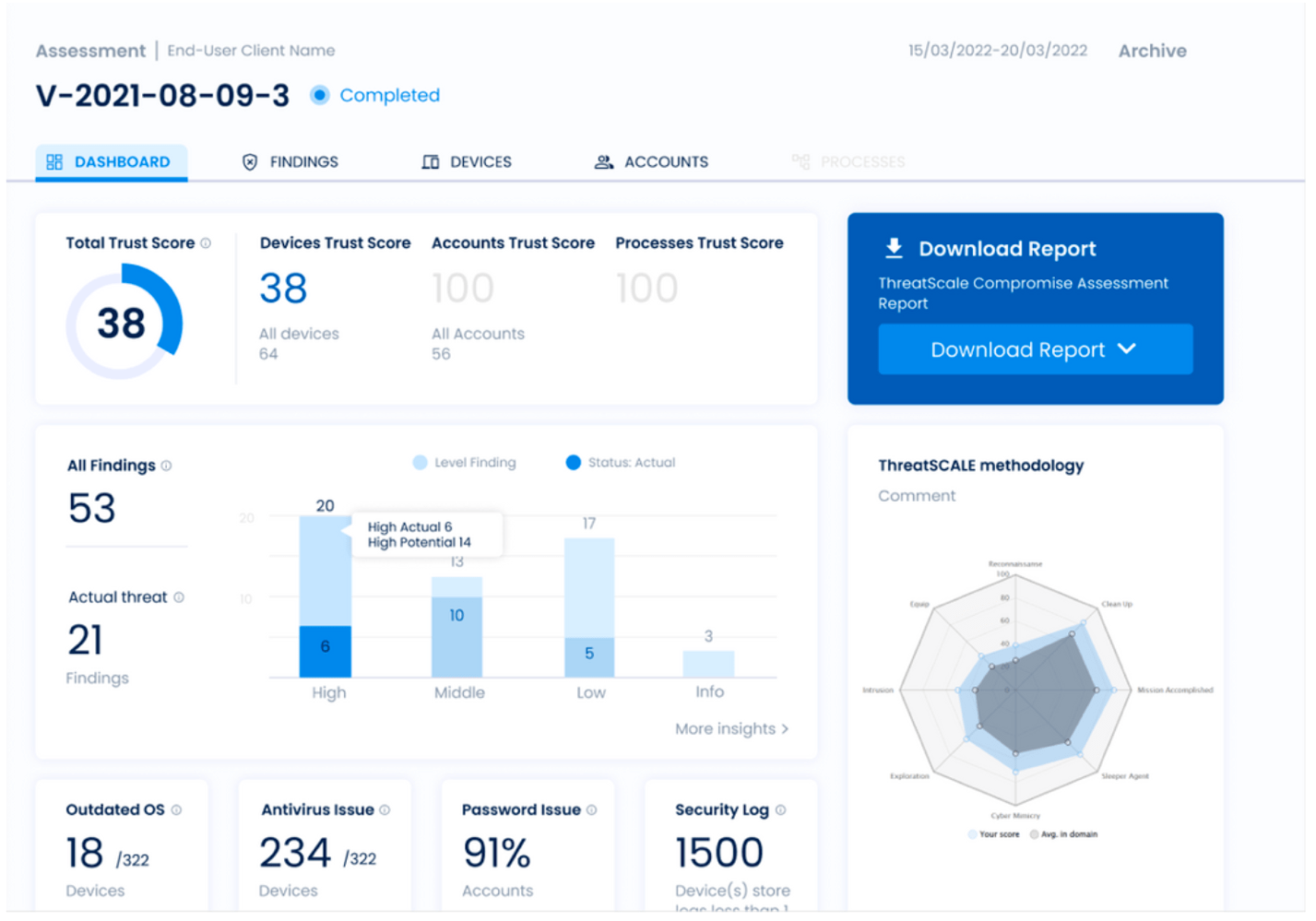
The collected data from the first time is used to answer the question of whether there has been a compromise or not. If yes, the compromise assessment team will validate the perceived compromise and then proceed with an analysis of the attack. Answering questions like, “When did the attack happen?”, “Where did it originate from?”, “Who is behind the attack?”, “Why are they targeting our organization?”, “What is the goal of the attack?”, and “How was the attack executed?”. These and many other related questions are asked and answered at this stage of the assessment.
By providing answers to these questions, the team will be able to decide what actions to take next and how to proceed.
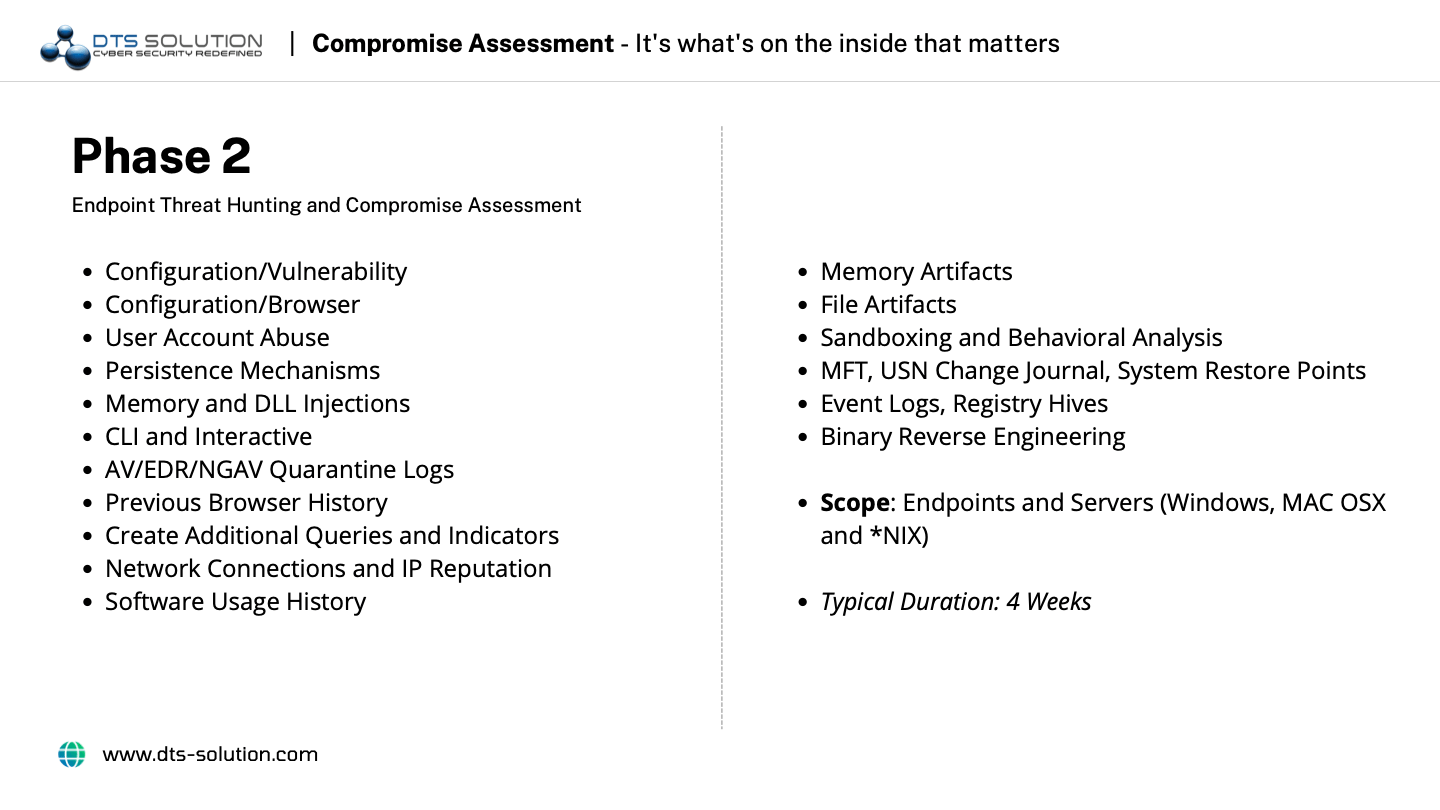
3. Assist
Data from previous processes and answers to numerous questions will only lead to more threat discoveries and questions to be answered. In this step, the compromise analysts can respond to and remediate discovered threats using their findings and answers.
4. Advise
When the organization understands how to improve its in-house response capabilities and overall security posture to prevent or address future incidents, the compromise assessment is complete. The compromise assessments team will report their findings and advise the organization on how to make the most of the assessment to strengthen its security posture.
Steps Involved in Compromise Assessment

Compromise assessment is basically a four-phase exercise that assesses, analyzes, and provides guidelines for an improved security posture. The steps involved in a compromise assessment are:
1. Assess
The compromise assessment process starts with gathering forensic data and looking for signs of past compromises or potential compromises in the system. This assessment includes scanning all system entities like API endpoints, network traffic, and logs.


2. Analyze
The collected data from the first time is used to answer the question of whether there has been a compromise or not. If yes, the compromise assessment team will validate the perceived compromise and then proceed with an analysis of the attack. Answering questions like, “When did the attack happen?”, “Where did it originate from?”, “Who is behind the attack?”, “Why are they targeting our organization?”, “What is the goal of the attack?”, and “How was the attack executed?”. These and many other related questions are asked and answered at this stage of the assessment.
By providing answers to these questions, the team will be able to decide what actions to take next and how to proceed.

3. Assist
Data from previous processes and answers to numerous questions will only lead to more threat discoveries and questions to be answered. In this step, the compromise analysts can respond to and remediate discovered threats using their findings and answers.
4. Advise
When the organization understands how to improve its in-house response capabilities and overall security posture to prevent or address future incidents, the compromise assessment is complete. The compromise assessments team will report their findings and advise the organization on how to make the most of the assessment to strengthen its security posture.
Final Words
In a traditional setting, any breach is cause for concern—but this should not be the case. It is preferable to know what has occurred and how many assets have been impacted before chaos ensues.
Final Words
Cybersecurity compromise or risk assessments can be performed by in-house cybersecurity personnel or contracted to a third-party consultant. It usually entails scanning and testing the strength and activity of networks, servers, applications, and endpoints, as well as penetration testing. The most important thing to remember is that a cybersecurity assessment should not be underestimated.
In a traditional setting, any breach is cause for concern—but this should not be the case. It is preferable to know what has occurred and how many assets have been impacted before chaos ensues.
See also: