Cybersecurity and privacy have become part of the most crucial factors for firms to consider in the modern digital world. With the increase in reliance on technology for storing and processing sensitive information, organizations now face risks of cyber threats including data breaches, denial of service, and credential compromise, among others. Likewise, privacy is becoming increasingly important as humans are now becoming more aware of their rights to control their personal information. This automatically has been making organizations aim to protect their customers’ data better, especially with the prevalence of data breaches, identity theft, and other privacy violations, where failure to properly protect can result in lawsuits, loss of customer trust, and damage to the organization’s reputation.
To address the pressing need for security and privacy, government agencies and volunteers collaborated to develop the Secure Control Framework (SCF) which encompasses different cybersecurity frameworks.
Let’s explore why SCF may be the ideal framework for integrating cybersecurity and privacy in an organization.
Cybersecurity and privacy have become part of the most crucial factors for firms to consider in the modern digital world. With the increase in reliance on technology for storing and processing sensitive information, organizations now face risks of cyber threats including data breaches, denial of service, and credential compromise, among others. Likewise, privacy is becoming increasingly important as humans are now becoming more aware of their rights to control their personal information. This automatically has been making organizations aim to protect their customers’ data better, especially with the prevalence of data breaches, identity theft, and other privacy violations, where failure to properly protect can result in lawsuits, loss of customer trust, and damage to the organization’s reputation.
To address the pressing need for security and privacy, government agencies and volunteers collaborated to develop the Secure Control Framework (SCF) which encompasses different cybersecurity frameworks.
Let’s explore why SCF may be the ideal framework for integrating cybersecurity and privacy in an organization.
What is The Secure Control Framework (SCF)?
The Secure Control Framework (SCF) is a comprehensive cybersecurity and privacy meta-framework (framework containing frameworks) that was developed by “volunteers” – mainly specialists within the cybersecurity profession, who focus on Governance, Risk, and Compliance (GRC) and the cybersecurity side of privacy. The SCF is designed to help organizations design, build and manage secure processes, maintain cybersecurity risks, and protect critical assets and data. It comprises a range of security and privacy standards, and industry-recognized best practices from the analysis of over 100 statutory, regulatory, and contractual frameworks.
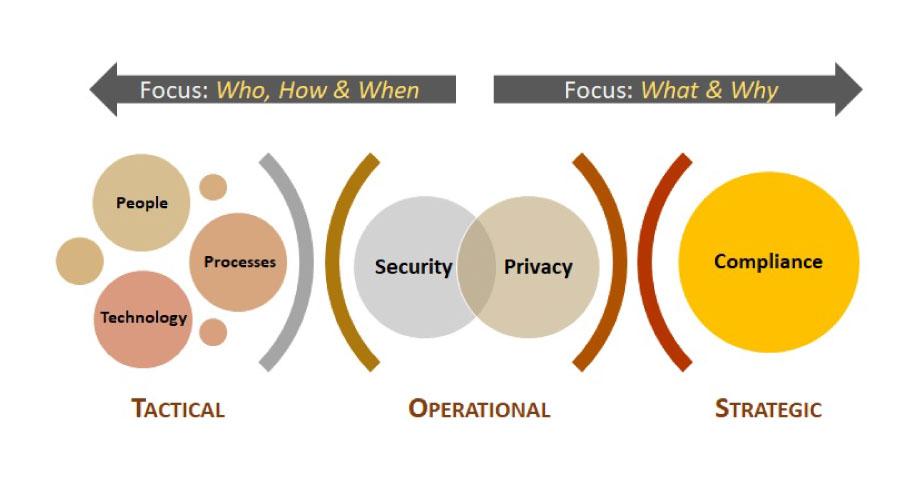
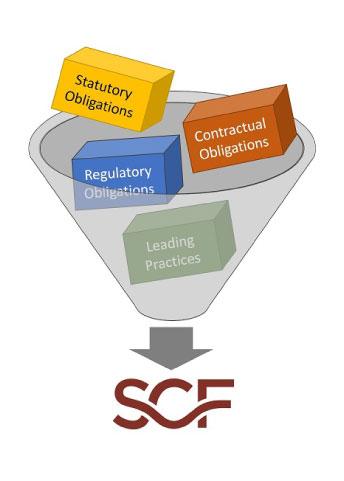
Image courtesy: Security Controls Framework
The SCF being a meta-framework, gives it an edge over singular cybersecurity frameworks – the comprehensiveness of SCF covers both cybersecurity and privacy, providing a holistic approach to the CIA triad, especially for organizations with more than 3 compliance needs. It includes a wide range of controls and guidelines, addressing everything from tactical, strategic, and operational levels. The SCF provides over 1,000 cybersecurity and privacy controls that are categorized into 33 domains, mapped across over 100 statutory, regulatory, and contractual frameworks.
- Security & Privacy Governance
- Artificial and Autonomous Technology
- Asset Management
- Business Continuity & Disaster Recovery
- Capacity & Performance Planning
- Change Management
- Cloud Security
- Compliance
- Configuration Management
- Continuous Monitoring
- Cryptographic Protections
- Data Classification & Handling
- Embedded Technology
- Endpoint Security
- Human Resources Security
- Identification & Authentication
- Incident Response
- Information Assurance
- Maintenance
- Mobile Device Management
- Network Security
- Physical & Environmental Security
- Privacy
- Project & Resource Management
- Risk Management
- Secure Engineering & Architecture
- Security Operations
- Security Awareness & Training
- Technology Development & Acquisition
- Third-Party Management
- Threat Management
- Vulnerability & Patch Management
- Web Security
The SCF believes that compliance with any security standard should come naturally as a by-product of implementing good security practices. Hence, it employs a secure-by-design concept containing 33 principles tailored toward successfully implementing a modern, generally accepted privacy and security program. These 79 principles are grouped into privacy by design, transparency, risk management, and 8 other domains.
The key components of the SCF include:
Integrated Controls Management (ICM) approach to Governance, Risk Management, and Compliance (GRC):
Integrated Cybersecurity Management (ICM) is a controls-centric approach that views controls as the central pivoting point for an organization’s cybersecurity and privacy operations. It proactively addresses the strategic, operational, and tactical nature of an organization’s cybersecurity and privacy program at the control level. ICM addresses internal controls and the broader concept of Supply Chain Risk Management (SCRM).
This component of the SCF focuses on understanding and clarifying the difference between being “compliant” and being “secure.” It is associated with eight principles that can guide its implementation:
- Establish Context
- Define Applicable Controls
- Assign Maturity-Based Criteria
- Publish Policies, Standards & Procedures
- Assign Stakeholder Accountability.
- Maintain Situational Awareness
- Manage Risk
- Evolve Processes
The SCF provides a detailed overview of each of these principles and how to use them to integrally manage governance, risk management, and compliance.
Security & Privacy Capability Maturity Model (SP-CMM):
The SP-CMM has three primary objectives that revolve around providing CISO/CPOs/CIOs with objective criteria, and setting expectations for a cybersecurity and privacy program. The first objective is to provide these individuals with objective criteria, which they can use to establish their expectations for a successful cybersecurity and privacy program. The second objective of the SP-CMM is to provide objective criteria for project teams to ensure that security practices are appropriately planned and budgeted for. Lastly, the third objective is to provide minimum criteria that can be used to evaluate third-party service provider controls to ensure that their controls meet the expected level of security and privacy.
SP-CMM has rates security and privacy programs on six levels:
- CMM 0 – Not Performed
- CMM 1 – Performed Informally
- CMM 2 – Planned & Tracked
- CMM 3 – Well-Defined
- CMM 4 – Quantitatively Controlled
- CMM 5 – Continuously Improving
Security and Privacy Risk Management Model (SP-RMM):
The SP-RMM component of SCF provides an effective methodology for identifying, assessing, reporting, and mitigating risk. It consists of 16 steps that cover the entire risk management process, from building a risk management program to ongoing risk management practices within an organization. The component is designed to be comprehensive and efficient, providing guidance for all aspects of risk management. By following the steps outlined in the SP-RMM, organizations can effectively manage risks and ensure the security and privacy of their data and systems.
What is The Secure Control Framework (SCF)?
The Secure Control Framework (SCF) is a comprehensive cybersecurity and privacy meta-framework (framework containing frameworks) that was developed by “volunteers” – mainly specialists within the cybersecurity profession, who focus on Governance, Risk, and Compliance (GRC) and the cybersecurity side of privacy. The SCF is designed to help organizations design, build and manage secure processes, maintain cybersecurity risks, and protect critical assets and data. It comprises a range of security and privacy standards, and industry-recognized best practices from the analysis of over 100 statutory, regulatory, and contractual frameworks.


Image courtesy: Security Controls Framework
The SCF being a meta-framework, gives it an edge over singular cybersecurity frameworks – the comprehensiveness of SCF covers both cybersecurity and privacy, providing a holistic approach to the CIA triad, especially for organizations with more than 3 compliance needs. It includes a wide range of controls and guidelines, addressing everything from tactical, strategic, and operational levels. The SCF provides over 1,000 cybersecurity and privacy controls that are categorized into 33 domains, mapped across over 100 statutory, regulatory, and contractual frameworks.
- Security & Privacy Governance
- Artificial and Autonomous Technology
- Asset Management
- Business Continuity & Disaster Recovery
- Capacity & Performance Planning
- Change Management
- Cloud Security
- Compliance
- Configuration Management
- Continuous Monitoring
- Cryptographic Protections
- Data Classification & Handling
- Embedded Technology
- Endpoint Security
- Human Resources Security
- Identification & Authentication
- Incident Response
- Information Assurance
- Maintenance
- Mobile Device Management
- Network Security
- Physical & Environmental Security
- Privacy
- Project & Resource Management
- Risk Management
- Secure Engineering & Architecture
- Security Operations
- Security Awareness & Training
- Technology Development & Acquisition
- Third-Party Management
- Threat Management
- Vulnerability & Patch Management
- Web Security
The SCF believes that compliance with any security standard should come naturally as a by-product of implementing good security practices. Hence, it employs a secure-by-design concept containing 33 principles tailored toward successfully implementing a modern, generally accepted privacy and security program. These 79 principles are grouped into privacy by design, transparency, risk management, and 8 other domains.
The key components of the SCF include:
Integrated Controls Management (ICM) approach to Governance, Risk Management, and Compliance (GRC):
Integrated Cybersecurity Management (ICM) is a controls-centric approach that views controls as the central pivoting point for an organization’s cybersecurity and privacy operations. It proactively addresses the strategic, operational, and tactical nature of an organization’s cybersecurity and privacy program at the control level. ICM addresses internal controls and the broader concept of Supply Chain Risk Management (SCRM).
This component of the SCF focuses on understanding and clarifying the difference between being “compliant” and being “secure.” It is associated with eight principles that can guide its implementation:
- Establish Context
- Define Applicable Controls
- Assign Maturity-Based Criteria
- Publish Policies, Standards & Procedures
- Assign Stakeholder Accountability.
- Maintain Situational Awareness
- Manage Risk
- Evolve Processes
The SCF provides a detailed overview of each of these principles and how to use them to integrally manage governance, risk management, and compliance.
Security & Privacy Capability Maturity Model (SP-CMM):
The SP-CMM has three primary objectives that revolve around providing CISO/CPOs/CIOs with objective criteria, and setting expectations for a cybersecurity and privacy program. The first objective is to provide these individuals with objective criteria, which they can use to establish their expectations for a successful cybersecurity and privacy program. The second objective of the SP-CMM is to provide objective criteria for project teams to ensure that security practices are appropriately planned and budgeted for. Lastly, the third objective is to provide minimum criteria that can be used to evaluate third-party service provider controls to ensure that their controls meet the expected level of security and privacy.
SP-CMM has rates security and privacy programs on six levels:
- CMM 0 – Not Performed
- CMM 1 – Performed Informally
- CMM 2 – Planned & Tracked
- CMM 3 – Well-Defined
- CMM 4 – Quantitatively Controlled
- CMM 5 – Continuously Improving
Security and Privacy Risk Management Model (SP-RMM):
The SP-RMM component of SCF provides an effective methodology for identifying, assessing, reporting, and mitigating risk. It consists of 16 steps that cover the entire risk management process, from building a risk management program to ongoing risk management practices within an organization. The component is designed to be comprehensive and efficient, providing guidance for all aspects of risk management. By following the steps outlined in the SP-RMM, organizations can effectively manage risks and ensure the security and privacy of their data and systems.
Benefits of Adopting SCF for Integrating Cybersecurity and Privacy
- A comprehensive approach to cybersecurity and privacy: The SCF offers a comprehensive approach to managing cybersecurity and privacy risks. The framework incorporates a range of security and privacy standards and best practices, making it an effective tool for managing cybersecurity risks and protecting critical assets and data. By adopting the SCF, organizations can ensure that they have a holistic approach to managing cybersecurity and privacy risks.
- Customizable framework: One of the key advantages of the SCF is its flexibility and customizability. The framework can be tailored to meet different organizations’ specific needs and requirements, regardless of industry. It offers a range of control categories, objectives, standards, and implementation levels, allowing organizations to choose the best controls that best meet their needs.
- Easy compliance with other frameworks: The SCF incorporates popular frameworks across all industries—thereby making it an easy link to achieve compliance with established security regulations even without paying attention to it.
- Established standards and best practices: The SCF is built upon established standards and best practices for cybersecurity and privacy, making it a reliable and effective framework for managing cybersecurity risks. The framework incorporates a range of standards, such as ISO 27001, NIST, and GDPR, ensuring that organizations adhere to established guidelines and best practices.
- Alignment with business goals: The SCF is designed to be aligned with business goals, ensuring that cybersecurity and privacy initiatives are integrated into the overall business strategy. By adopting the SCF, organizations can ensure that cybersecurity and privacy are not viewed as separate initiatives, but rather as integral components of their overall business strategy.
Get in touch with a DTS Solutions representative to get started on implementing a security and privacy-first cybersecurity program in your organization.
Benefits of Adopting SCF for Integrating Cybersecurity and Privacy
Organizations can gain a variety of advantages by implementing the Secure Control Framework, chief among them being compliance with various frameworks that place a security-first emphasis rather than a compliance-first one. Other benefits include:
- A comprehensive approach to cybersecurity and privacy: The SCF offers a comprehensive approach to managing cybersecurity and privacy risks. The framework incorporates a range of security and privacy standards and best practices, making it an effective tool for managing cybersecurity risks and protecting critical assets and data. By adopting the SCF, organizations can ensure that they have a holistic approach to managing cybersecurity and privacy risks.
- Customizable framework: One of the key advantages of the SCF is its flexibility and customizability. The framework can be tailored to meet different organizations’ specific needs and requirements, regardless of industry. It offers a range of control categories, objectives, standards, and implementation levels, allowing organizations to choose the best controls that best meet their needs.
- Easy compliance with other frameworks: The SCF incorporates popular frameworks across all industries—thereby making it an easy link to achieve compliance with established security regulations even without paying attention to it.
- Established standards and best practices: The SCF is built upon established standards and best practices for cybersecurity and privacy, making it a reliable and effective framework for managing cybersecurity risks. The framework incorporates a range of standards, such as ISO 27001, NIST, and GDPR, ensuring that organizations adhere to established guidelines and best practices.
- Alignment with business goals: The SCF is designed to be aligned with business goals, ensuring that cybersecurity and privacy initiatives are integrated into the overall business strategy. By adopting the SCF, organizations can ensure that cybersecurity and privacy are not viewed as separate initiatives, but rather as integral components of their overall business strategy.
Get in touch with a DTS Solutions representative to get started on implementing a security and privacy-first cybersecurity program in your organization.

