With advanced malware targeting ATM machines on the rise the importance to protect ATM machines is greater than ever before. Automated Teller Machines (ATM) are no longer just affected by the physical attempt of emptying the money safe. Now logical attacks on ATMs are slowly being recognized as an emerging threat by the security industry and law enforcement agencies. ATM malware had been detected by various researchers for a few years now and we have already seen incidents of their successful use; most recently in Taiwan and Japan. Where coordinated cyber criminals used evasive malware in conjunction with a “connected device” likely a smartphone, to instruct the ATM to release the cash. The targeted ATMs are produced by the Wincor Nixdorf, the company admitted that some of its ATM in Taiwan were hacked as part of a “premeditated attack.”
Investigators have discovered three different strains of malware on the hacked ATMs, of course, the banks in the country are starting to improve the cyber security of their machines in order to prevent similar attacks. Such attacks are a global cyber security challenge and is now a common landscape. If you recall similar incidents took place in Y2013 where 36,000 transactions over 26 countries that included banks in the GCC and Middle East back where the target or coordinated cyber criminals who lured $45M from the ATM machines.
With advanced malware targeting ATM machines on the rise the importance to protect ATM machines is greater than ever before. Automated Teller Machines (ATM) are no longer just affected by the physical attempt of emptying the money safe. Now logical attacks on ATMs are slowly being recognized as an emerging threat by the security industry and law enforcement agencies. ATM malware had been detected by various researchers for a few years now and we have already seen incidents of their successful use; most recently in Taiwan and Japan. Where coordinated cyber criminals used evasive malware in conjunction with a “connected device” likely a smartphone, to instruct the ATM to release the cash. The targeted ATMs are produced by the Wincor Nixdorf, the company admitted that some of its ATM in Taiwan were hacked as part of a “premeditated attack.”
Investigators have discovered three different strains of malware on the hacked ATMs, of course, the banks in the country are starting to improve the cyber security of their machines in order to prevent similar attacks. Such attacks are a global cyber security challenge and is now a common landscape. If you recall similar incidents took place in Y2013 where 36,000 transactions over 26 countries that included banks in the GCC and Middle East back where the target or coordinated cyber criminals who lured $45M from the ATM machines.
What brought about the advent of ATM malware?
Trend Micro and Europol’s European Cybercrime Center (EC3) worked together to examine the evolving cyber threat targeting ATMs. Their research indicates that there are many factors that facilitated the shift toward the use of a hacking toolkit to target ATMs, alongside more traditional attack vectors.
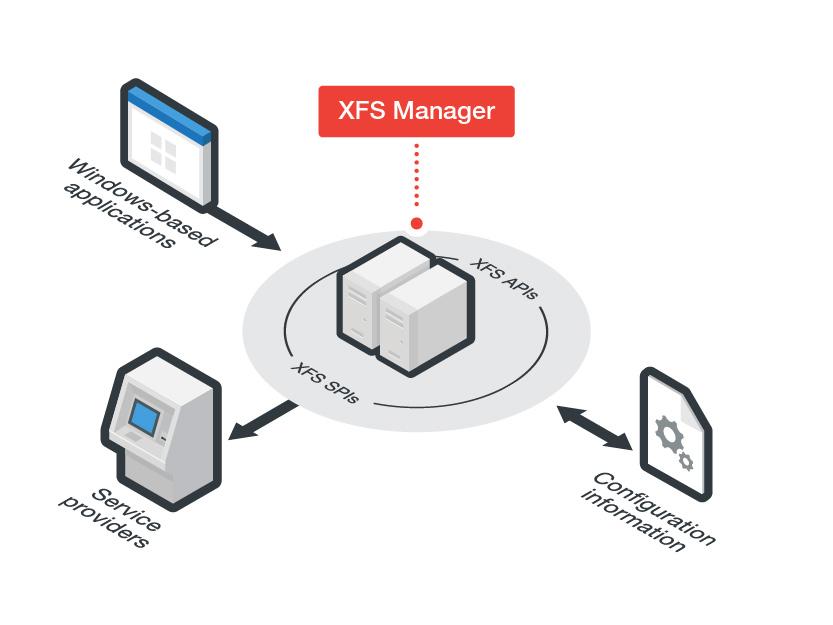
One major factor is the use of an outdated operating system (OS) such as Windows XP that cannot receive security patches anymore. Another reason can be found in the increasing sophistication of criminals and their realization that the digital way is less risky and that it allows them to move around more stealthily. Another significant factor is the ATM vendors’ decision to employ middleware that provide Application Programming Interfaces (APIs) to communicate with the machine’s peripheral devices (such as PIN pad, cash dispenser etc.) – regardless of the model. This middleware is known as the eXtensions for Financial Services (XFS) middleware. In simple terms, if we think of a modern ATM as a MS Windows PC with a money box attached to it that’s controlled through software, it is easy to see how it becomes an attractive target for any malware writer.
What brought about the advent of ATM malware?
Trend Micro and Europol’s European Cybercrime Center (EC3) worked together to examine the evolving cyber threat targeting ATMs. Their research indicates that there are many factors that facilitated the shift toward the use of a hacking toolkit to target ATMs, alongside more traditional attack vectors.
One major factor is the use of an outdated operating system (OS) such as Windows XP that cannot receive security patches anymore. Another reason can be found in the increasing sophistication of criminals and their realization that the digital way is less risky and that it allows them to move around more stealthily. Another significant factor is the ATM vendors’ decision to employ middleware that provide Application Programming Interfaces (APIs) to communicate with the machine’s peripheral devices (such as PIN pad, cash dispenser etc.) – regardless of the model. This middleware is known as the eXtensions for Financial Services (XFS) middleware. In simple terms, if we think of a modern ATM as a MS Windows PC with a money box attached to it that’s controlled through software, it is easy to see how it becomes an attractive target for any malware writer.
The main ATM malware families in existence
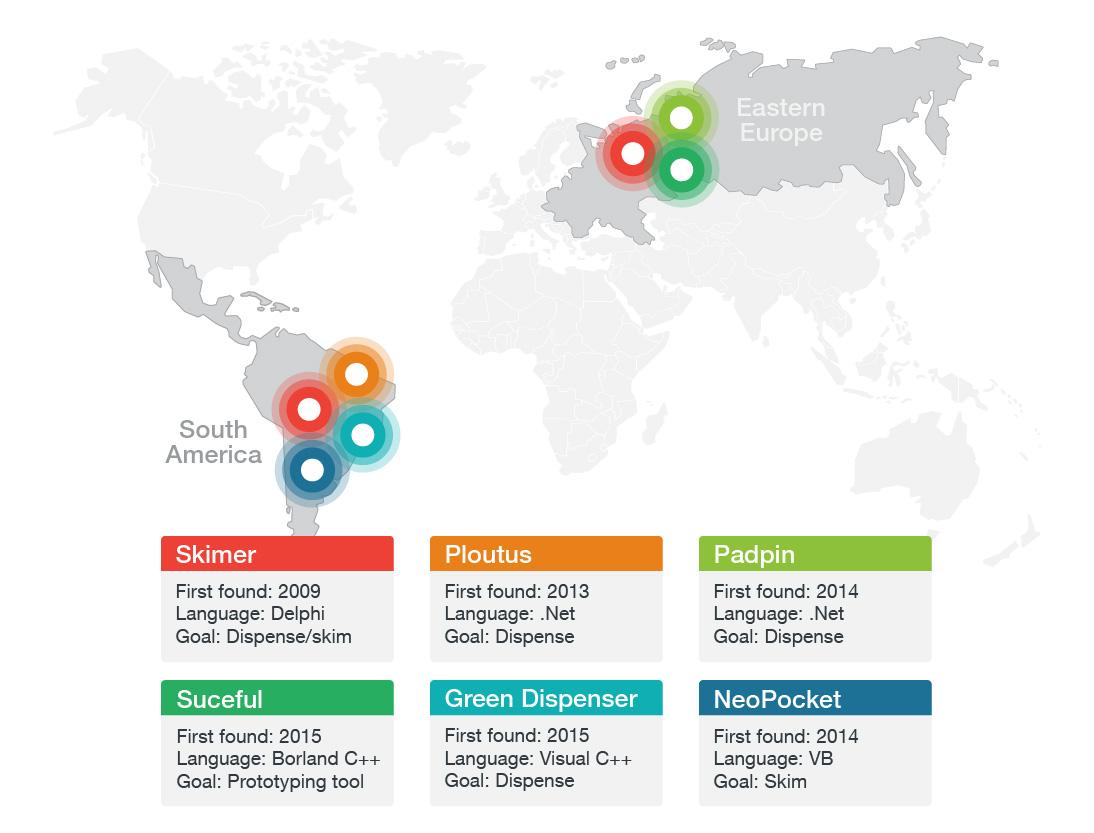
The collaborative research from Trend Micro and Europol’s European Cybercrime Center (EC3) also looked at the main malware types in circulation at the moment. The map above reveals an interesting pattern in terms of origin of the code. A lack of security measures implemented by commercial banks in Latin America and Eastern Europe, has opened the door for criminals to victimize ATMs in these regions. Though very slowly, we are also witnessing the export of these techniques into other regions. Although we have not yet seen ATM malware being traded in the underground, this is an anticipated development expected in the not-so-distant future.
Each of the malware families listed above has a particular functional set-up that can be distinguished by two main characteristics: 1) the ATM manufacturer type, and 2) the specific malware capabilities – whether it is used for skimming the machine for user input such as card numbers and PIN codes, or for actually dispensing cash. What the malware have in common is that it is typically installed manually via USB or the CD-drive.
These findings are based on an investigation that Trend Micro and Europol’s European Cybercrime Center (EC3) have worked on together in order to examine the current state of ATM malware. The result is a comprehensive document highlighting the evolving cyber threat targeting ATMs including an analysis of the new methods used and corresponding key defensive approaches for the organizations concerned to protect their businesses and customers. This joint report is another example of the successful collaboration between law enforcement and industry in fighting cybercrime.
The main ATM malware families in existence
The collaborative research from Trend Micro and Europol’s European Cybercrime Center (EC3) also looked at the main malware types in circulation at the moment. The map above reveals an interesting pattern in terms of origin of the code. A lack of security measures implemented by commercial banks in Latin America and Eastern Europe, has opened the door for criminals to victimize ATMs in these regions. Though very slowly, we are also witnessing the export of these techniques into other regions. Although we have not yet seen ATM malware being traded in the underground, this is an anticipated development expected in the not-so-distant future.
Each of the malware families listed above has a particular functional set-up that can be distinguished by two main characteristics: 1) the ATM manufacturer type, and 2) the specific malware capabilities – whether it is used for skimming the machine for user input such as card numbers and PIN codes, or for actually dispensing cash. What the malware have in common is that it is typically installed manually via USB or the CD-drive.
These findings are based on an investigation that Trend Micro and Europol’s European Cybercrime Center (EC3) have worked on together in order to examine the current state of ATM malware. The result is a comprehensive document highlighting the evolving cyber threat targeting ATMs including an analysis of the new methods used and corresponding key defensive approaches for the organizations concerned to protect their businesses and customers. This joint report is another example of the successful collaboration between law enforcement and industry in fighting cybercrime.
See also: