Cybersecurity teams in various organizations have continuously adapted and innovated to defend against rapidly changing cyber threats. The world of cybersecurity is constantly evolving, with new security assessment methods appearing on a regular basis.
Red and Blue teaming has been the assessment concept that has been around for a while.
- Red Teaming: Red teams are offensive security professionals who are experts in attacking systems and breaking into defenses. Red teams simulate attacks against blue teams to test the effectiveness of the network’s security. They utilize all the available techniques (discussed below) to find weaknesses in people, processes, and technology to gain unauthorized access to assets. As a result of these simulated attacks, red teams make recommendations and plans on how to strengthen an organization’s security posture.
- Blue Teaming: Blue teams are defensive security professionals who are in charge of upholding defenses against all cyber-attacks and threats. A blue team is a group of security personnel who are skilled in defense, have an insider’s perspective on the organization, and put defense systems in place to protect the organization against cyberattacks. They are the polar opposite of red teams—although both teams are structured and expected to work together.
While both of these teams are expected to collaborate to make the organization’s cyber entities resilient, the reality of most organizations is quite different.
In many organizations, the in-house security team acts as the blue team, while an external ethical hacker is brought in occasionally to perform vulnerability scanning and penetration testing. Oftentimes, there is no direct exchange of information between the external hacker and the in-house blue team. Consequently, there is no efficient exchange of information that would allow the blue team to create new security controls and further enhance and implement the existing ones for maximum efficiency.
Another scenario is of blue and red teams formed by groups of in-house security experts with no established information-sharing channel. Such scenarios like this undermine the use of red and blue teaming.
To combat this loophole in communication and fully harness the benefits of red and blue teaming, the cybersecurity community birthed purple teaming.
Building Control Effectiveness Through Purple Teaming
Cybersecurity teams in various organizations have continuously adapted and innovated to defend against rapidly changing cyber threats. The world of cybersecurity is constantly evolving, with new security assessment methods appearing on a regular basis.
Red and Blue teaming has been the assessment concept that has been around for a while.
- Red Teaming: Red teams are offensive security professionals who are experts in attacking systems and breaking into defenses. Red teams simulate attacks against blue teams to test the effectiveness of the network’s security. They utilize all the available techniques (discussed below) to find weaknesses in people, processes, and technology to gain unauthorized access to assets. As a result of these simulated attacks, red teams make recommendations and plans on how to strengthen an organization’s security posture.
- Blue Teaming: Blue teams are defensive security professionals who are in charge of upholding defenses against all cyber-attacks and threats. A blue team is a group of security personnel who are skilled in defense, have an insider’s perspective on the organization, and put defense systems in place to protect the organization against cyberattacks. They are the polar opposite of red teams—although both teams are structured and expected to work together.
While both of these teams are expected to collaborate to make the organization’s cyber entities resilient, the reality of most organizations is quite different.
In many organizations, the in-house security team acts as the blue team, while an external ethical hacker is brought in occasionally to perform vulnerability scanning and penetration testing. Oftentimes, there is no direct exchange of information between the external hacker and the in-house blue team. Consequently, there is no efficient exchange of information that would allow the blue team to create new security controls and further enhance and implement the existing ones for maximum efficiency.
Another scenario is of blue and red teams formed by groups of in-house security experts with no established information-sharing channel. Such scenarios like this undermine the use of red and blue teaming.
To combat this loophole in communication and fully harness the benefits of red and blue teaming, the cybersecurity community birthed purple teaming.

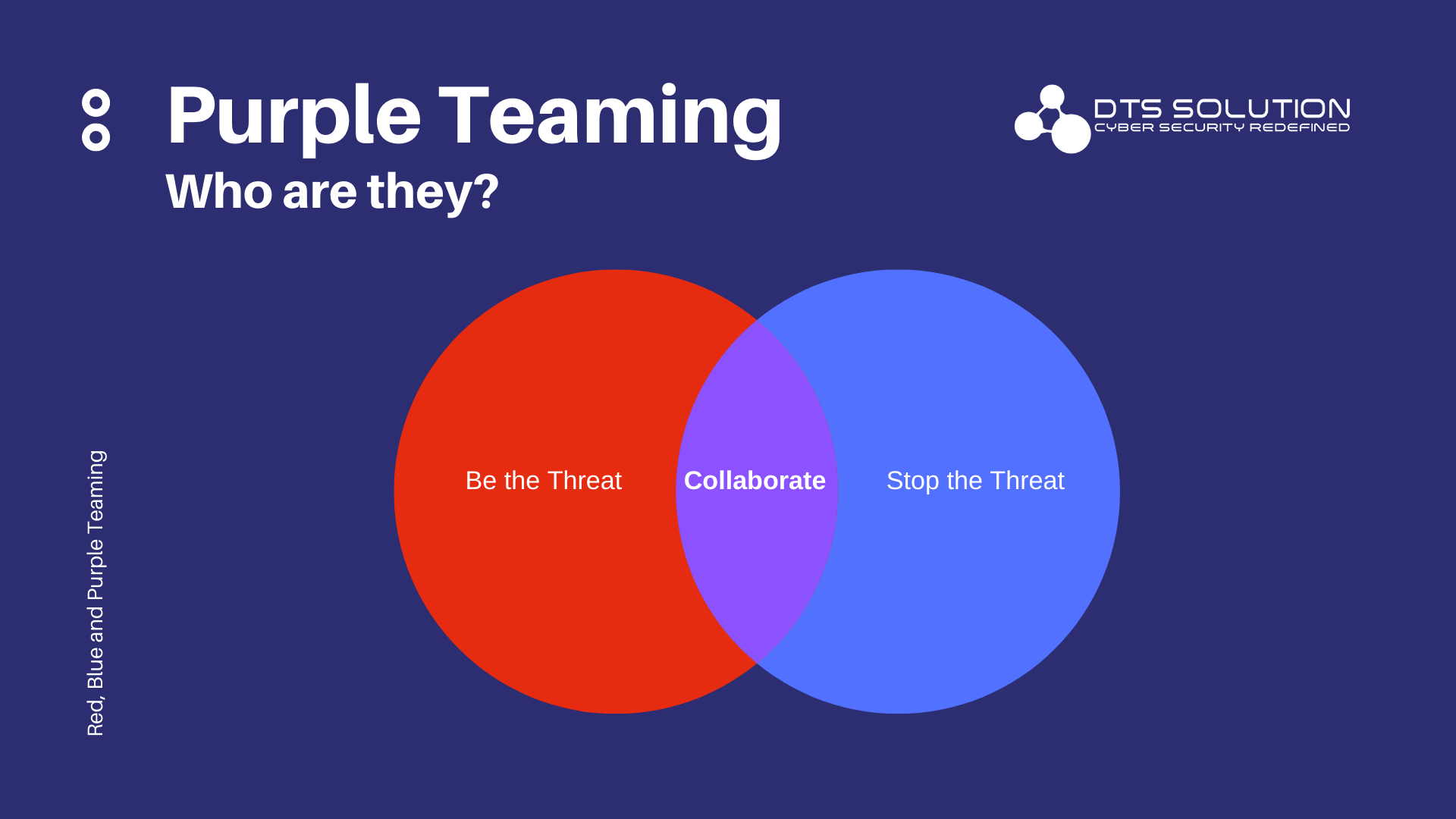
What is Purple Teaming?
Purple teaming is a security strategy in which red and blue teams collaborate closely to maximize cyber capabilities through feedback and a knowledge-sharing loop. By realistically recreating typical attack scenarios and supporting the development of novel strategies meant to avoid and identify new threats; purple teaming can assist security teams in enhancing the effectiveness of vulnerability detection, threat hunting, and system monitoring. By merging defense and attack in purple team activities, you can develop and implement effective security controls than by isolating both tasks.
There is growing acknowledgment that Red Teams and Blue Teams should collaborate to form a purple team. This team isn’t necessarily a new “specialized team,” but rather a fusion of existing red team and blue team members. It could be viewed as a team that involves both red and blue, rather than a distinct team in itself. Because there’s still a need to assume offensive/defensive roles, even while working collaboratively.
What is Purple Teaming?
Purple teaming is a security strategy in which red and blue teams collaborate closely to maximize cyber capabilities through feedback and a knowledge-sharing loop. By realistically recreating typical attack scenarios and supporting the development of novel strategies meant to avoid and identify new threats; purple teaming can assist security teams in enhancing the effectiveness of vulnerability detection, threat hunting, and system monitoring. By merging defense and attack in purple team activities, you can develop and implement effective security controls than by isolating both tasks.
There is growing acknowledgment that Red Teams and Blue Teams should collaborate to form a purple team. This team isn’t necessarily a new “specialized team,” but rather a fusion of existing red team and blue team members. It could be viewed as a team that involves both red and blue, rather than a distinct team in itself. Because there’s still a need to assume offensive/defensive roles, even while working collaboratively.

Benefits of Purple Teaming
1. Improved Cybersecurity Culture
Arguably the most crucial benefit of purple teaming is strong, consistent communication between offensive and defense, as well as a steady flow of information and symbiotic activity. It is critical to encourage communication and collaboration among team members in order to ensure continuous improvement of the organization’s cybersecurity culture. And purple teaming is designed to promote that.
2. Improved Vulnerability Detection
Sometimes a breach occurs with the attacker bypassing all defenses and the blue team is unaware of it, due to the sophistication of the attacker’s strategies or attack routes. Purple teaming prevents this from happening. Working with red and blue teams entails regular knowledge transfer and recreating real-life attack scenarios. As a result, the red team will improve the organization’s vulnerability management process, while the blue team will design stronger incident response programs and vulnerability detection methods by putting themselves in the shoes of attackers.
3. Improved Insights
By effectively modeling typical attack scenarios and supporting the development of novel strategies meant to avoid and identify new threats, purple teaming can assist security teams in enhancing the effectiveness of vulnerability detection, threat hunting, and system monitoring.
4. Improved Security Posture
The end goal and most essential benefit of purple is a better and improved security posture. Purple teaming exponentially increases an organization’s chances of repelling and surviving a hostile cyber attack, thanks to smooth communication, routine security audits, novel defense strategies, threat hunting, vulnerability management, and the development of stronger security infrastructure and policies, all made possible by purple teaming.
Benefits of Purple Teaming
The following are some of the ways an organization can benefit from implementing the purple teaming security assessment practice.
1. Improved Cybersecurity Culture
Arguably the most crucial benefit of purple teaming is strong, consistent communication between offensive and defense, as well as a steady flow of information and symbiotic activity. It is critical to encourage communication and collaboration among team members in order to ensure continuous improvement of the organization’s cybersecurity culture. And purple teaming is designed to promote that.
2. Improved Vulnerability Detection
Sometimes a breach occurs with the attacker bypassing all defenses and the blue team is unaware of it, due to the sophistication of the attacker’s strategies or attack routes. Purple teaming prevents this from happening. Working with red and blue teams entails regular knowledge transfer and recreating real-life attack scenarios. As a result, the red team will improve the organization’s vulnerability management process, while the blue team will design stronger incident response programs and vulnerability detection methods by putting themselves in the shoes of attackers.
3. Improved Insights
By effectively modeling typical attack scenarios and supporting the development of novel strategies meant to avoid and identify new threats, purple teaming can assist security teams in enhancing the effectiveness of vulnerability detection, threat hunting, and system monitoring.
4. Improved Security Posture
The end goal and most essential benefit of purple is a better and improved security posture. Purple teaming exponentially increases an organization’s chances of repelling and surviving a hostile cyber attack, thanks to smooth communication, routine security audits, novel defense strategies, threat hunting, vulnerability management, and the development of stronger security infrastructure and policies, all made possible by purple teaming.

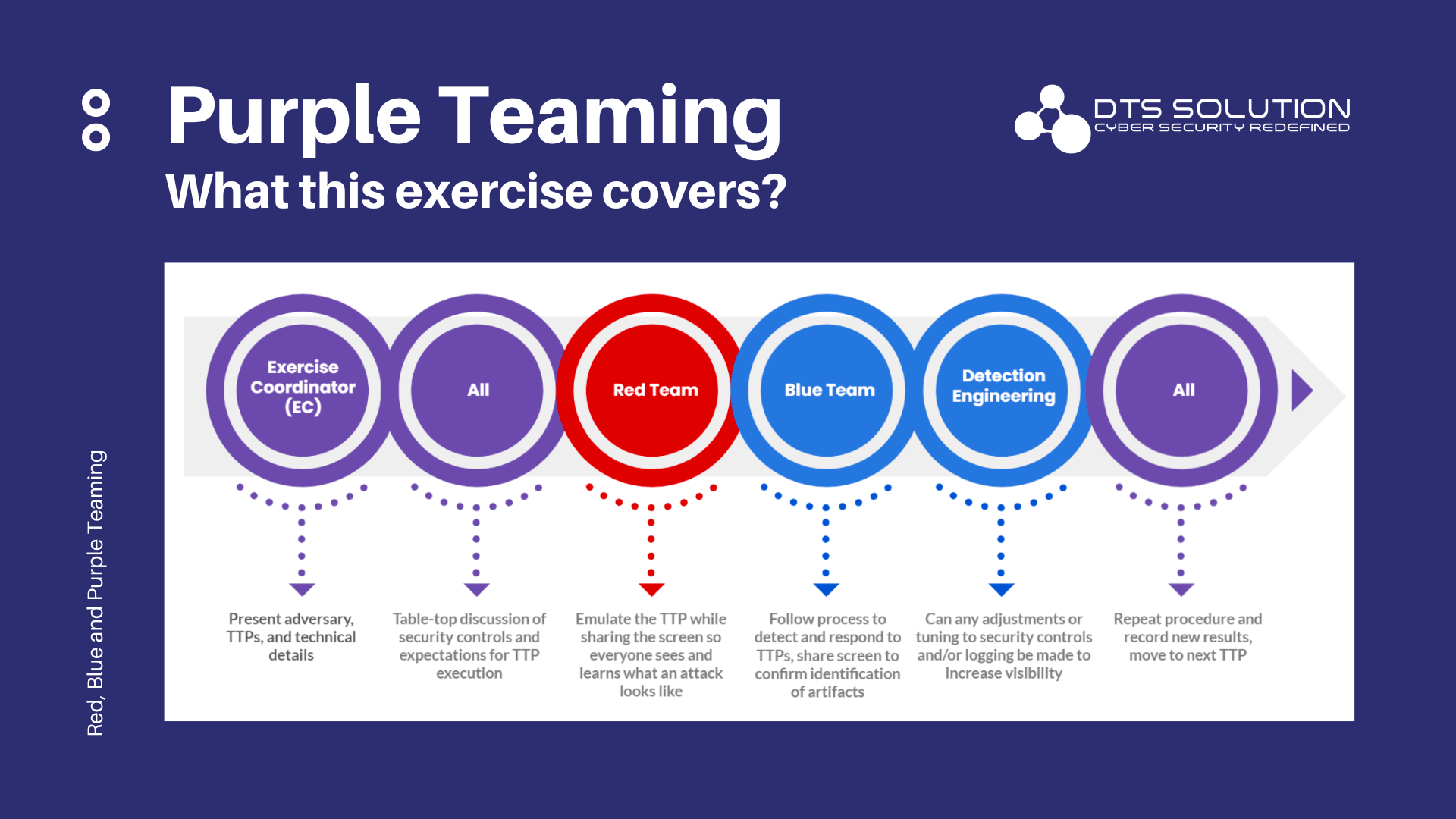
Purple Teaming and Effective Controls
When the attack and defense teams of an organization’s cybersecurity department are working separately, there are often difficulties in testing security controls that require the expertise of the other team. This creates a loophole in the implementation of such security controls, making it difficult to adapt to the organization’s cybersecurity realities and leading to the inefficiency of such controls.
This problem is solved by the red team collaborating with the blue team in a purple team activity. When an extra control is added, the same behavior can be simulated again and again until the control adequately blocks or detects it. Regular purple team activities allow you to retest your present controls to ensure they are still functioning properly. Combining the two functions in these purple team exercises also helps with the resource issue because the blue team does not need to master the skills and instead takes the time to reproduce assault behaviors. This thereby makes the implementation of new and existing security controls more efficient.
Purple Teaming and Effective Controls
When the attack and defense teams of an organization’s cybersecurity department are working separately, there are often difficulties in testing security controls that require the expertise of the other team. This creates a loophole in the implementation of such security controls, making it difficult to adapt to the organization’s cybersecurity realities and leading to the inefficiency of such controls.
This problem is solved by the red team collaborating with the blue team in a purple team activity. When an extra control is added, the same behavior can be simulated again and again until the control adequately blocks or detects it. Regular purple team activities allow you to retest your present controls to ensure they are still functioning properly. Combining the two functions in these purple team exercises also helps with the resource issue because the blue team does not need to master the skills and instead takes the time to reproduce assault behaviors. This thereby makes the implementation of new and existing security controls more efficient.

Conclusion
Purple teaming is a tried-and-true method that guarantees cooperative cybersecurity in both small and large organizations. By making the offensive and defensive teams work closely together, organizations can adequately assess their security posture, propose security controls, test, and efficiently implement these controls for the utmost safety of the organization’s cyber entities.
Conclusion
See also: