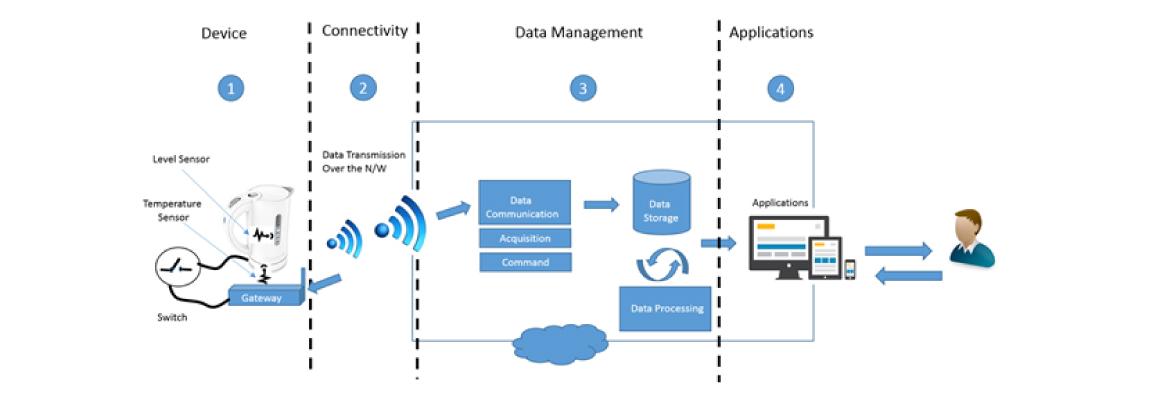
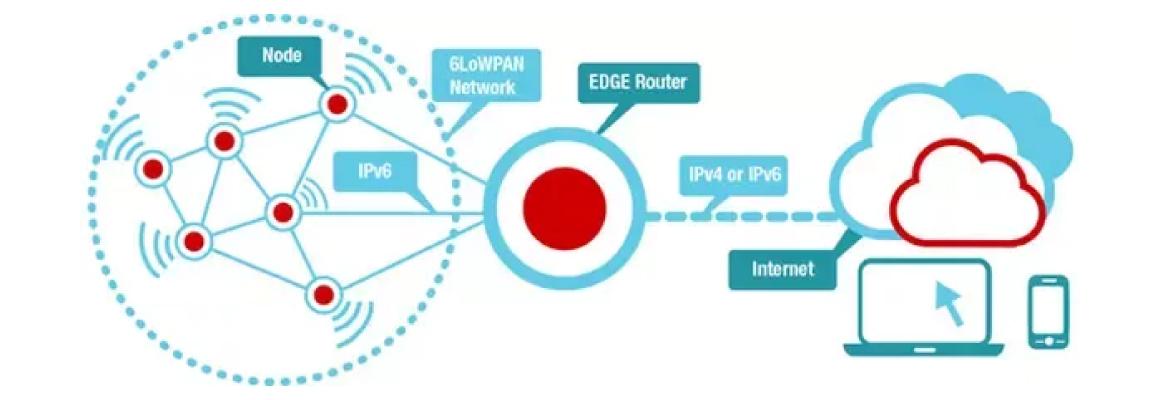
Organizations should employ a good risk assessment process from the development/design phase and apply the principle of least privilege coupled with firewalls, detection tools, and other security technologies to identify any anomalous behavior that results from their compromise and proactively fix the problem.
This brings a great number of new vulnerabilities in any organization’s infrastructure and generates a predominant attack surface, which the adversaries can utilize to obtain non authorized access and compromise these devices. IoT devices are purpose-built with a narrow set of functions, allowing organizations to gather and monitor flow data and baseline normal traffic patterns.
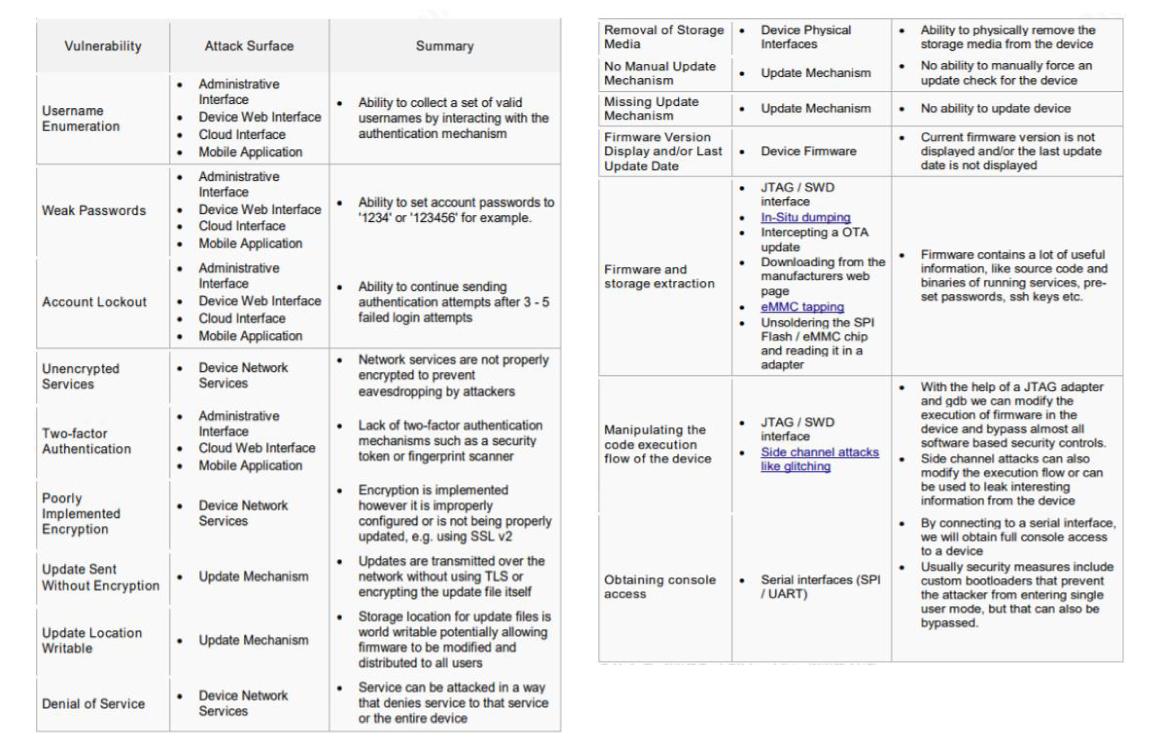
This provides awareness into some vulnerabilities and security issues the industry is facing. Organizations can further enumerate this ‘top vulnerabilities’ list into a fuller list of vulnerabilities and threats simply by mapping the attack surface and identifying recent attacks. The ‘Device Network Services’ and ‘Network Traffic’ categories of the OWASP IoT Attack Surface Areas list brings to light other types of attacks, specifically on IoT networking, that include routing attacks, Denial of Service (DoS) attacks, and Sybil attacks, among others.
Attack trees can also be used to create potential threats. Once the threats have been identified, an intrusion analyst can better understand what to implement and where.
IoT introduces additional complexity for security. Organizations are advised to monitor the data traffic to and from IoT devices in their network. Perimeter-based solutions are not adequate in today’s environment because users and apps can no longer be contained inside a company’s network, behind a clearly defined protective wall.
Most IoT devices will operate in a relatively static environment. The operations they perform, the amount of data they transmit and receive, and the other devices they communicate with, change infrequently. Significant changes in these basic behaviors are anomalies and may denote a cyber-attack.
Organizations must stop deploying IoT devices and appliances as trusted end systems. In the other hand, they should employ a good risk assessment process from the development/design phase and apply the principle of least privilege couple with firewalls, detection tools, and other security technologies to identify any anomalous behavior that results from their compromise and proactively fix the problem. During the operational phase, collecting and analysis of flow data is the most efficient and effective mechanism to reduce the security risks associated with deploying IoT devices.
Organizations should employ a good risk assessment process from the development/design phase and apply the principle of least privilege coupled with firewalls, detection tools, and other security technologies to identify any anomalous behavior that results from their compromise and proactively fix the problem.
This brings a great number of new vulnerabilities in any organization’s infrastructure and generates a predominant attack surface, which the adversaries can utilize to obtain non authorized access and compromise these devices. IoT devices are purpose-built with a narrow set of functions, allowing organizations to gather and monitor flow data and baseline normal traffic patterns.
This provides awareness into some vulnerabilities and security issues the industry is facing. Organizations can further enumerate this ‘top vulnerabilities’ list into a fuller list of vulnerabilities and threats simply by mapping the attack surface and identifying recent attacks. The ‘Device Network Services’ and ‘Network Traffic’ categories of the OWASP IoT Attack Surface Areas list brings to light other types of attacks, specifically on IoT networking, that include routing attacks, Denial of Service (DoS) attacks, and Sybil attacks, among others.
Attack trees can also be used to create potential threats. Once the threats have been identified, an intrusion analyst can better understand what to implement and where.
Organizations must stop deploying IoT devices and appliances as trusted end systems. In the other hand, they should employ a good risk assessment process from the development/design phase and apply the principle of least privilege couple with firewalls, detection tools, and other security technologies to identify any anomalous behavior that results from their compromise and proactively fix the problem. During the operational phase, collecting and analysis of flow data is the most efficient and effective mechanism to reduce the security risks associated with deploying IoT devices.