Android App to Remote Shell
This was an android application I was testing for a friend. I started off by setting up my android pentesting environment. This involves an android device and my kali. I generally use genymotion which is an android emulator in order to test android applications. In order to use a MITM tool like burp or zap, change the network setting on the virtual device. I usually startup my kali VM and put burp to listen on all interfaces on a particular port number instead of localhost which is the default setting. On the android virtual device, give the ip address of the VM and the port, Now you have your MITM proxy set up.
Android App to Remote Shell
This was an android application I was testing for a friend. I started off by setting up my android pentesting environment. This involves an android device and my kali. I generally use genymotion which is an android emulator in order to test android applications. In order to use a MITM tool like burp or zap, change the network setting on the virtual device. I usually startup my kali VM and put burp to listen on all interfaces on a particular port number instead of localhost which is the default setting. On the android virtual device, give the ip address of the VM and the port, Now you have your MITM proxy set up.
I tested the usual parameters such as the OTP mechanism, SQLi in the login page, repeatability of the OTP. The usual web application vulns such as CSRF and XSS was out of scope in this scenario because this application was never going to be accessible on the browser.
The pentest went as usual, with a few low risk vulns like server disclosure, few cases of un intended default pages from the framework used still lying around but nothing serious that would make my day.
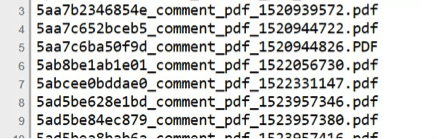
Soon I saw the file upload functionality ☺ ☺ ☺ ☺. I started by trying to upload a legitimate pdf file. In the response, I saw that the server was returning the internal file path to where the file is being stored. I immediately opened up my browser and put in the path with a trailing slash “/”.and we have directory listing. I was also able to see all the uploads that everyone made.
The pentest went as usual, with a few low risk vulns like server disclosure, few cases of un intended default pages from the framework used still lying around but nothing serious that would make my day.
Soon I saw the file upload functionality ☺ ☺ ☺ ☺. I started by trying to upload a legitimate pdf file. In the response, I saw that the server was returning the internal file path to where the file is being stored. I immediately opened up my browser and put in the path with a trailing slash “/”.and we have directory listing. I was also able to see all the uploads that everyone made.
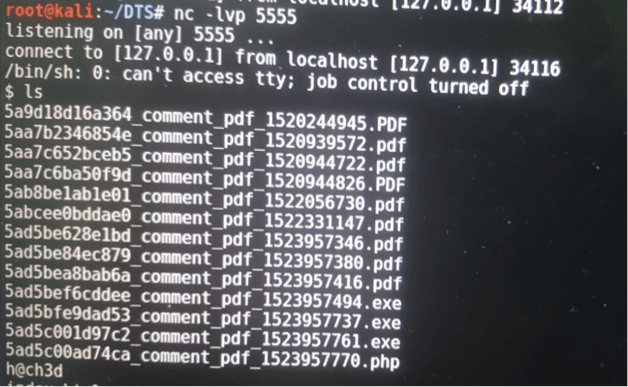
Next I tried to upload my webshell via the android virtual device. No luck!! The client side scripts kept me from uploading anything fun. I used burp to capture my request copied the php webshell script pasted it in the body of the POST request and changed the extension to php. Now two things here – I was able to upload a php webshell and I have access to the uploaded files. When we have these two together we have code execution on the server ☺ ☺ ☺ ☺ ☺.
Next I tried to upload my webshell via the android virtual device. No luck!! The client side scripts kept me from uploading anything fun. I used burp to capture my request copied the php webshell script pasted it in the body of the POST request and changed the extension to php. Now two things here – I was able to upload a php webshell and I have access to the uploaded files. When we have these two together we have code execution on the server 



 .
.




 .
.
Now I wasn’t satisfied with this. Lets try to get a shell access. But how do I get a tcp reverse shell without port forwarding. In comes ngrok to the rescue. Ngrok takes care of forwarding tcp connections from their server to a local port of our choosing. After starting ngrok on you machine open another window and use netcat and listen to the particular port on localhost. Now use a simple python reverse shell script from pentest monkey and put the url given to you when you run ngrok on your system.
Happy Hacking ☺ ☺ ☺ ☺
Now I wasn’t satisfied with this. Lets try to get a shell access. But how do I get a tcp reverse shell without port forwarding. In comes ngrok to the rescue. Ngrok takes care of forwarding tcp connections from their server to a local port of our choosing. After starting ngrok on you machine open another window and use netcat and listen to the particular port on localhost. Now use a simple python reverse shell script from pentest monkey and put the url given to you when you run ngrok on your system.
Happy Hacking 


See also: