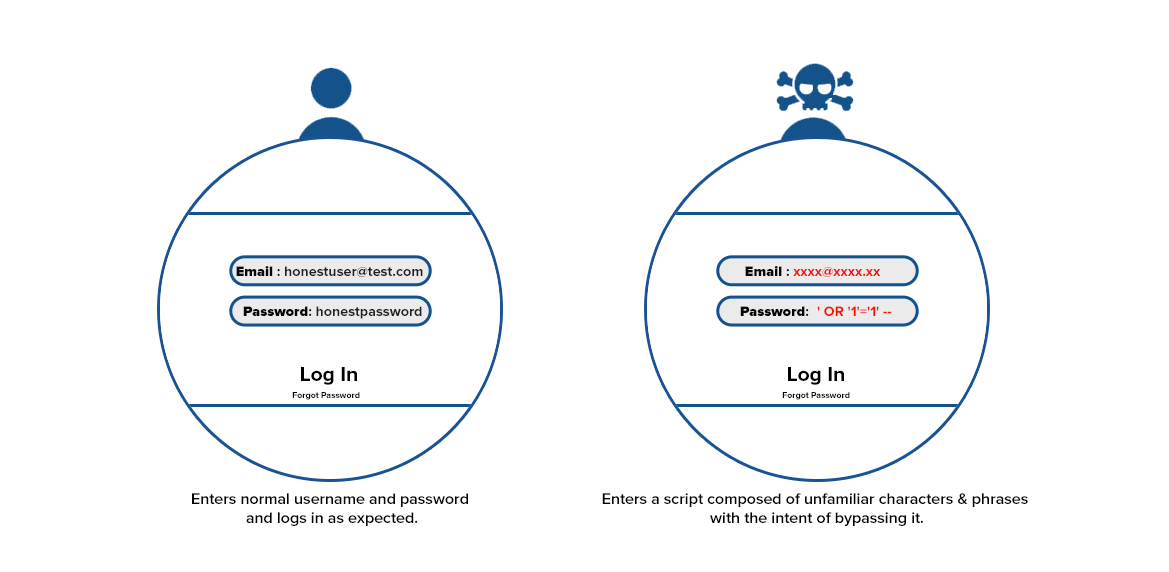
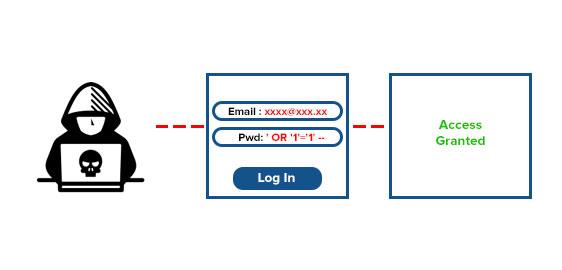
Injection flaws
A coordinated effort by the software development community to produce more robust and reliable applications will prevent attackers and allow users and stakeholders to feel confident that they are protected from exploitation.
Injection flaws
Injection Flaws Types
- SQL injection
- OS Command injection
- LDAP injection and
- XML injection
Injection Flaws Types
- SQL injection
- OS Command injection
- LDAP injection and
- XML injection
SQL Injection
SQL Injection
SQL Injection Mitigation Strategies
SQL Injection Mitigation Strategies
Client side input sanitization and validation should only be considered a convenience for the end user, improving their user experience.Just because the browser’s user interface doesn’t allow the user to manipulate an input, it doesn’t mean that it can’t be tampered with. Server side sanitization and input validation ensures data supplied by the user does not contain characters like single or double quotes that could modify an SQL query and return data not originally intended in the application’s design. For instance, in PHP, you can use the mysql_real_escape_string() to escape characters that might change the nature of the SQL command.
OS Command Injection
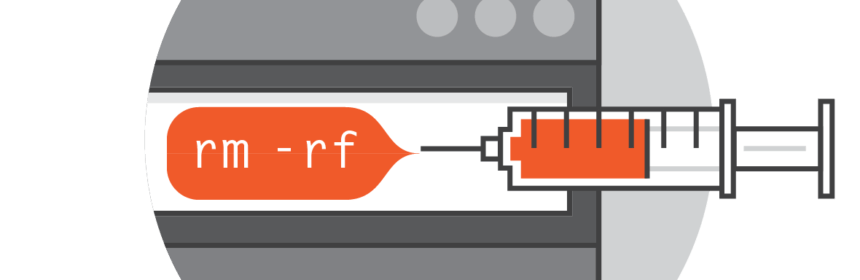
OS Command Injection Occurs when command string is generated dynamically using input supplied by the user.When the software allows the execution of Operation System (OS) level commands using the supplied user input without sanitization or validation, it is said to be susceptible to OS Command injection
OS Command Injection

The two main types of OS Command injection are as follows
- The software accepts arguments from the user to execute a single fixed program command. In such cases, the injection is contained only to the command that is allowed to execute and the attacker can change the input but not the command itself. Here, the programming error is that the programmer assumes that the input supplied by users to be part of the arguments in the command to be executed will be trustworthy as intended, and not malicious
- The software accepts arguments from the user which specifies what program command they would like the system to execute. This is a lot more serious than the previous case, because now the attacker can chain multiple commands and do some serious damage to the system by executing their own commands that the system supports. Here, the programming error is that the programmer assumes that the command itself will not be accessible to untrusted users.
system(“rm $file”);
- Avoid system calls where possible
- Avoid user input of any kind inside them unless it is absolutely necessary and deactivate that function in your language's configuration file if you don't need it.
- Build a whitelist of possible inputs and check its format
The two main types of OS Command injection are as follows
- The software accepts arguments from the user to execute a single fixed program command. In such cases, the injection is contained only to the command that is allowed to execute and the attacker can change the input but not the command itself. Here, the programming error is that the programmer assumes that the input supplied by users to be part of the arguments in the command to be executed will be trustworthy as intended, and not malicious
- The software accepts arguments from the user which specifies what program command they would like the system to execute. This is a lot more serious than the previous case, because now the attacker can chain multiple commands and do some serious damage to the system by executing their own commands that the system supports. Here, the programming error is that the programmer assumes that the command itself will not be accessible to untrusted users.
%20 decodes to a space and %3B decodes to a ; and the command that is executed will be /bin/ls -l listing the contents of the program’s working directory.
system(“rm $file”);
- Avoid system calls where possible
- Avoid user input of any kind inside them unless it is absolutely necessary and deactivate that function in your language's configuration file if you don't need it.
- Build a whitelist of possible inputs and check its format
LDAP Injection
How to prevent LDAP injection attacks?
- Safe LDAP Configuration – This involves the safeguarding of sensitive information and data in the LDAP directory, especially while dealing with permissions on user objects. This is all the more important when the directory is used by the web/mobile application for a single logging-on process.
- Advanced input validation – All user-end input must be sanitized thoroughly. It should be free of suspicious characters and strings that can be malicious.
-
Output regulation – Limits and restrictions should also be placed on the amount of data/information returned by the LDAP servers to the client
LDAP Injection
How to prevent LDAP injection attacks?
- Safe LDAP Configuration – This involves the safeguarding of sensitive information and data in the LDAP directory, especially while dealing with permissions on user objects. This is all the more important when the directory is used by the web/mobile application for a single logging-on process.
- Advanced input validation – All user-end input must be sanitized thoroughly. It should be free of suspicious characters and strings that can be malicious.
- Output regulation – Limits and restrictions should also be placed on the amount of data/information returned by the LDAP servers to the client
XML Injection
- XPATH injection
- XQuery injection
- In XPATH injection the XPath expression that is used to retrieve data from the XML data store is not validated or sanitized prior to processing and built dynamically using user supplied input. The structure of the query can thus be controlled by the user, and an attacker can take advantage of this weakness by injecting malformed XML expressions, allowing the attacker to perform malicious operations such as modifying and controlling logic flow,retrieving unauthorized data and/or circumventing authentication checks.
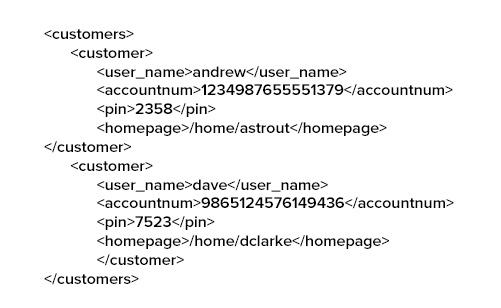
- XQuery injection works the same way as an XPath injection, except that the XQuery (not XPath) expression that is used to retrieve data from the XML data store is not validated or sanitized prior to processing and built dynamically using user supplied input. Consider the following XML document (accounts.xml) that stores the account information and pin numbers of customers and a snippet of Java code that uses XPath query to retrieve authentication information:
This will allow the user logging in as ‘andrew; to bypass authentication without supplying a valid PIN.
XML Injection
- XPATH injection
- XQuery injection
- In XPATH injection the XPath expression that is used to retrieve data from the XML data store is not validated or sanitized prior to processing and built dynamically using user supplied input. The structure of the query can thus be controlled by the user, and an attacker can take advantage of this weakness by injecting malformed XML expressions, allowing the attacker to perform malicious operations such as modifying and controlling logic flow,retrieving unauthorized data and/or circumventing authentication checks.
- XQuery injection works the same way as an XPath injection, except that the XQuery (not XPath) expression that is used to retrieve data from the XML data store is not validated or sanitized prior to processing and built dynamically using user supplied input. Consider the following XML document (accounts.xml) that stores the account information and pin numbers of customers and a snippet of Java code that uses XPath query to retrieve authentication information:
XPathExpression xPathExp = xpath.compile(“//customers/customer[user_ name/text()=’” + login.getUserName() + “’ and pin/text() = ‘” + login. getPIN() + “’]/homepage/text()”);
Document doc = DocumentBuilderFactory.newInstance(). newDocumentBuilder().parse(new File(“accounts.xml”));
String homepage = xPathExp.evaluate(doc);
Preventing XML Injection
The prevention of XML injection can be done by properly managing and sanitizing any user input before it is allowed to reach the main program code.The best method is to consider all the user input as unsafe and to properly monitor this input. Most types of the XML injection attacks can be prevented by simply removing all the single and double quotes from the user input. Though this method is very convenient but proper care needs to be taken.