Introducing the Threat Hunting Maturity Model
The human domain is complex and unpredictable, and as a result the logic behind certain behaviors are also complex. The problem that many detection systems try to resolve is the automated detection of these complex behavior actions. Some of the actions are obvious (i.e. ports scan), but others are less detectable, particularly when is coming from the internal network such as valid credentials used for wrong purposes.
To make the issue a little more difficult, not all analysts use the same techniques or methods to achieve their goals. For example, a nation state actor could have a set of known techniques tactics and procedures (TTPs) that could potentially be detected. If the TTPs changed, what new course of actions would the analyst take? Or even more frustrating, what if an insider was operating in the grounds of a company policy to steal data? The detection line grows and might even be non-existent in the case of an insider leaking information until the damage is done.
One of the fastest and effective means to detect who the adversaries are, is via threat modeling. In the most rudimentary example, a simple survey polling the current IR team can bring a solid list of potential, or known adversaries. This tacit knowledge is powerful because it is the shared body of knowledge that has been learned over many years. Often it is the assumed knowledge, or information that did not make it into a formal document.
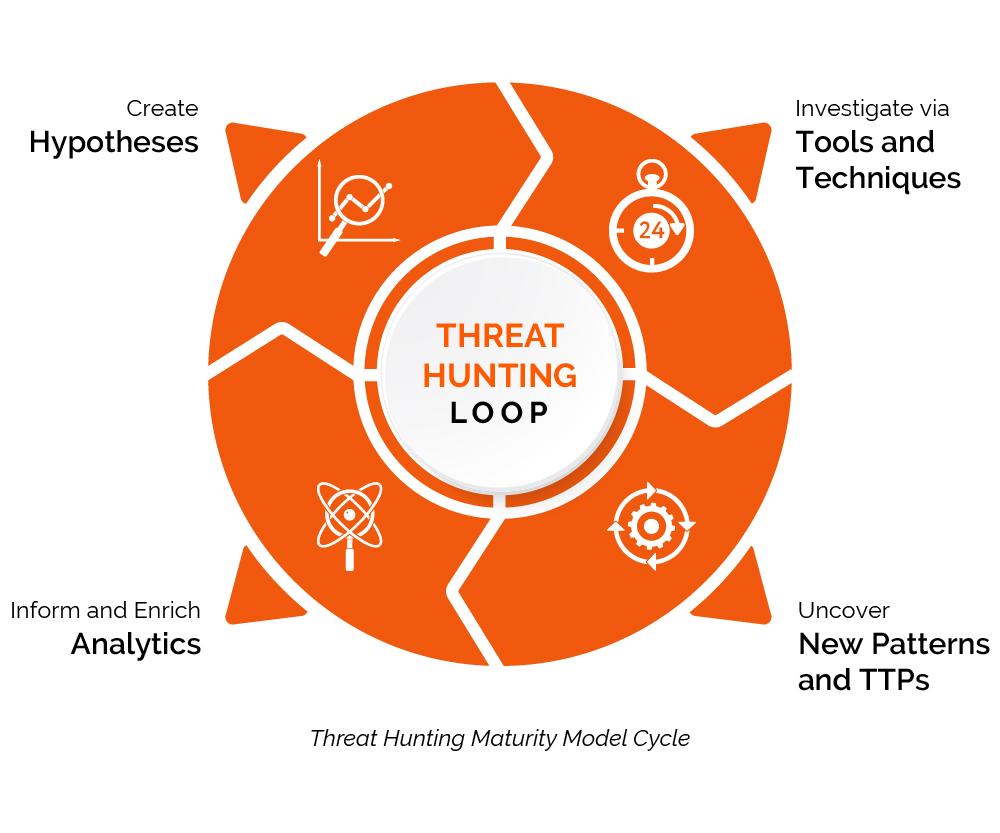
Introducing the Threat Hunting Maturity Model. This model is very similar to the Capabilities Maturity Model Integration (CMMI) which is a generic process model improvement.
To read more about threat hunting maturity cycle, please click here.
Introducing the Threat Hunting Maturity Model

The human domain is complex and unpredictable, and as a result the logic behind certain behaviors are also complex. The problem that many detection systems try to resolve is the automated detection of these complex behavior actions. Some of the actions are obvious (i.e. ports scan), but others are less detectable, particularly when is coming from the internal network such as valid credentials used for wrong purposes.
To make the issue a little more difficult, not all analysts use the same techniques or methods to achieve their goals. For example, a nation state actor could have a set of known techniques tactics and procedures (TTPs) that could potentially be detected. If the TTPs changed, what new course of actions would the analyst take? Or even more frustrating, what if an insider was operating in the grounds of a company policy to steal data? The detection line grows and might even be non-existent in the case of an insider leaking information until the damage is done.
One of the fastest and effective means to detect who the adversaries are, is via threat modeling. In the most rudimentary example, a simple survey polling the current IR team can bring a solid list of potential, or known adversaries. This tacit knowledge is powerful because it is the shared body of knowledge that has been learned over many years. Often it is the assumed knowledge, or information that did not make it into a formal document.
Introducing the Threat Hunting Maturity Model. This model is very similar to the Capabilities Maturity Model Integration (CMMI) which is a generic process model improvement.
To read more about threat hunting maturity cycle, please click here.
See also: