Managing who has access to what within your organization has become increasingly complex. With employees, contractors, partners, and automated systems all requiring varying levels of access to corporate resources, the risks of mismanaged identities have never been higher. Organizations face daily challenges in balancing operational efficiency with robust security controls. This is where Identity Access Governance (IAG) becomes essential.
What Is Identity Access Governance?
Identity Access Governance represents a comprehensive approach to managing and overseeing digital identities and their associated access rights across an organization. It encompasses the policies, processes, and technologies that ensure users have appropriate permissions aligned with their roles while maintaining compliance with regulatory requirements.
IAG provides visibility into who can access which systems and data, establishes controls around access provisioning and revocation, and generates audit trails that demonstrate compliance. For organizations handling sensitive information or operating in regulated industries, implementing a robust Identity and Access Governance framework becomes critical for maintaining both security and operational integrity.
The Core Components of Identity Access Governance
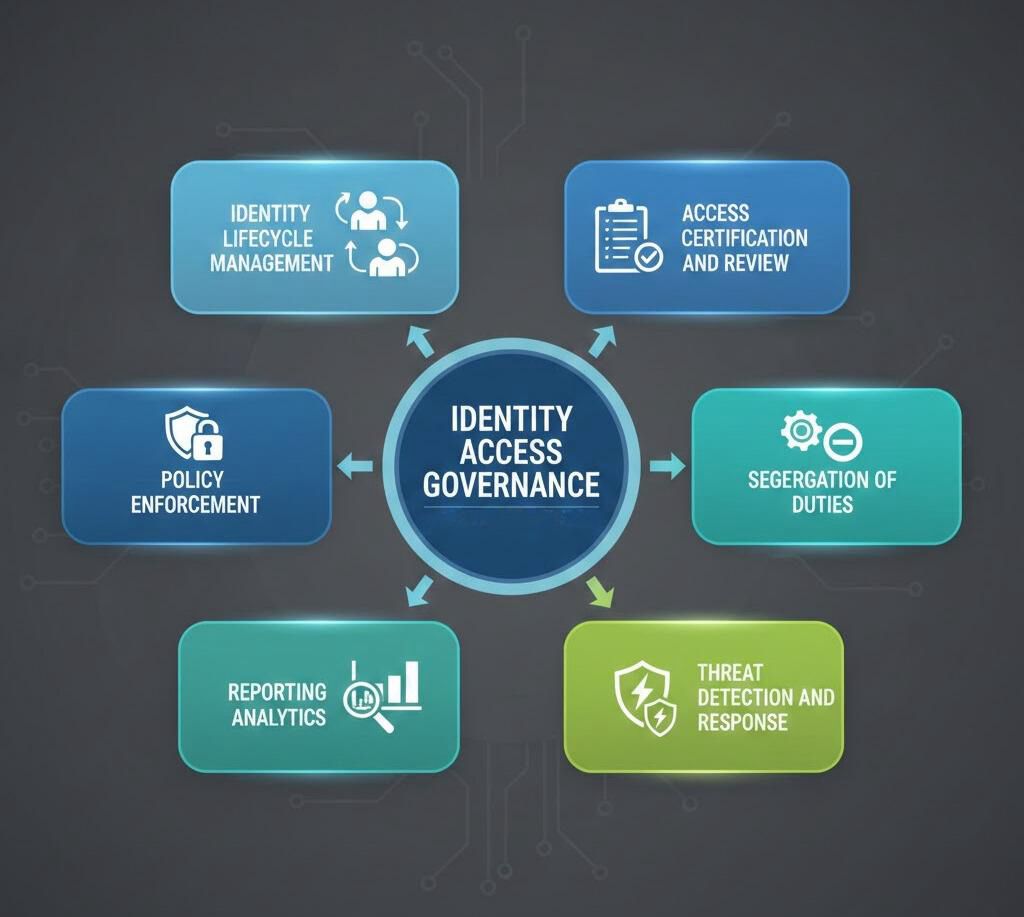
Understanding IAG requires breaking down its fundamental elements:
Identity Lifecycle Management handles the complete journey of user accounts from creation through modification to eventual deactivation. When employees join, change roles, or leave the organization, IAG systems automatically adjust their access rights accordingly. This automation reduces the risk of orphaned accounts or lingering permissions that create security vulnerabilities.
Access Certification and Review involves periodic verification that users maintain only the access they need. Managers and system owners regularly review and validate permissions, identifying excessive privileges or unauthorized access patterns. These reviews form a crucial defense layer against privilege creep and insider threats.
Policy Enforcement ensures consistent application of access control rules across all systems and applications. Organizations define policies based on roles, responsibilities, regulatory requirements, and risk tolerance. IAG platforms then enforce these policies automatically, reducing manual errors and inconsistencies.
Segregation of Duties prevents conflicts of interest by ensuring no single individual holds permissions that could enable fraud or abuse. For example, someone who can approve financial transactions shouldn’t also have the ability to initiate them. IAG systems actively monitor and flag violations of segregation rules.
Reporting and Analytics generate insights into access patterns, compliance status, and potential security risks. Organizations can track metrics like certification completion rates, high-risk access combinations, and policy violations to continually improve their governance posture.
Why Organizations Need Identity Access Governance
The business case for IAG extends beyond simple security concerns. Modern organizations face multiple pressures that make governance essential.
Regulatory Compliance Requirements: Industries such as healthcare, finance, and government operate under strict regulations regarding data access and privacy. Standards like HIPAA, GDPR, PCI DSS, and SOC 2 mandate specific controls around identity management. IAG provides the framework and evidence needed to demonstrate compliance during audits. Organizations can efficiently build GRC programs that align with these regulatory demands.
Reducing Security Breach Risks: According to recent research, 83% of data breaches involve internal actors. Many of these incidents stem from excessive permissions or compromised credentials. IAG limits the potential damage from both malicious insiders and compromised accounts by ensuring users only access what they legitimately need. Regular access reviews help identify and remove unnecessary privileges before they can be exploited.
Managing Complex Hybrid Environments: Organizations today operate across on-premises infrastructure, multiple cloud platforms, and countless SaaS applications. Each environment may have its own identity management approach, creating silos that reduce visibility. IAG provides unified governance across this fragmented infrastructure, enabling consistent policy enforcement regardless of where resources reside.
Operational Efficiency: Manual access provisioning creates bottlenecks that frustrate users and burden IT teams. Employees waiting for access permissions lose productivity, while IT staff spend countless hours processing routine requests. IAG automates routine tasks like granting standard access based on roles, freeing IT teams for higher-value work while accelerating onboarding.
Identity Access Governance vs Identity and Access Management
Many organizations confuse IAG with Identity and Access Management (IAM), though they serve complementary purposes. IAM focuses on the technical mechanisms of authentication and authorization, verifying who users are and granting them access to resources. Think of IAM as the engine that executes access decisions.
IAG operates at a higher level, providing oversight and control over IAM systems. It answers questions like: “Does this user still need this access?” “Are we complying with our segregation of duties policies?” “Can we prove our access controls meet regulatory requirements?” While IAM handles the tactical execution, IAG provides strategic governance.
For instance, when an employee joins your organization, IAM systems authenticate them and provision their initial access. IAG ensures those access rights align with company policies, tracks changes over time, periodically reviews the appropriateness of those rights, and maintains records for compliance purposes. Both layers work together to create a comprehensive identity security program.
Implementing Effective Identity Access Governance
Successfully deploying IAG requires careful planning and execution across several key areas:
Assessment and Planning: Begin by thoroughly understanding your current state. Document existing identity management processes, catalog all applications and systems requiring governance, identify regulatory requirements and business policies, and assess risks associated with current access practices. This foundation helps prioritize improvements and set realistic implementation timelines.
Establishing Clear Policies: Define specific, enforceable policies around access management. These should cover role definitions and associated permissions, approval workflows for access requests, frequency and scope of access reviews, segregation of duties requirements, and procedures for handling policy violations. Policies must balance security requirements with operational practicality to ensure actual adoption.
Technology Selection and Integration: Choose IAG platforms that integrate with your existing infrastructure. The solution should connect to all critical identity sources and target systems, support your organization’s scale and complexity, provide automation capabilities to reduce manual effort, and offer reporting and analytics tailored to your compliance needs. Organizations should carefully evaluate whether solutions can manage the full digital identity lifecycle across their specific environment.
Automation and Workflow Design: Leverage automation to improve efficiency and consistency. Automate routine tasks like role-based provisioning, access request routing and approval, periodic access reviews and certifications, and policy violation detection and alerting. Well-designed workflows ensure the right people make access decisions at the right time with the right information.
Continuous Monitoring and Improvement: IAG is not a one-time project but an ongoing program. Regularly monitor key metrics like access review completion rates, average time to provision or revoke access, number and types of policy violations, and compliance audit findings. Use these insights to refine policies, improve processes, and enhance automation.
Best Practices for Identity Access Governance
Organizations that excel at IAG typically follow several common practices:
Adopt a Risk-Based Approach: Not all access requires the same level of governance. Focus intensive controls on high-risk areas like privileged accounts, sensitive data access, and production systems. Apply lighter-touch governance to low-risk scenarios to maintain operational efficiency.
Engage Business Stakeholders: IAG cannot succeed as a purely IT-driven initiative. Engage business leaders and process owners who understand operational requirements and can validate access needs. Their input ensures governance policies align with actual business processes rather than creating obstacles.
Start Small and Scale: Rather than attempting to govern everything simultaneously, begin with high-priority systems or user populations. Prove value through initial successes, then gradually expand scope. This approach builds organizational buy-in and allows you to refine processes before enterprise-wide rollout.
Integrate with Zero Trust Principles: Modern security architectures embrace zero trust, which assumes no implicit trust and continuously validates access. IAG naturally supports this model by regularly reviewing and validating access rights rather than granting permanent permissions. Consider how IAG fits within your broader zero trust implementation.
Provide Self-Service Capabilities: Empower users to request access, view their current permissions, and track request status through self-service portals. This improves user experience while reducing IT workload. Automated workflows can handle routine requests without manual intervention.
Maintain Clear Audit Trails: Document all access-related decisions, changes, and reviews. These records prove essential during compliance audits and security investigations. Ensure audit logs capture who made decisions, when they occurred, and the justification provided.
The Future of Identity Access Governance
IAG continues to advance with emerging technologies and changing security requirements. Artificial intelligence and machine learning increasingly augment governance processes by detecting anomalous access patterns, predicting which access reviews require closer scrutiny, and recommending optimal role definitions based on actual usage patterns.
Cloud-native architectures demand governance models that work seamlessly across distributed environments. Organizations require unified visibility and control whether users access resources through traditional networks or modern cloud platforms. The rise of machine identities, service accounts, and API keys adds complexity that governance programs must address.
Integration with broader security ecosystems enables IAG platforms to consume risk signals from threat detection tools, endpoint security solutions, and security information and event management systems. This context enriches access decisions and helps prioritize governance activities based on real-time risk.
Managing who has access to what within your organization has become increasingly complex. With employees, contractors, partners, and automated systems all requiring varying levels of access to corporate resources, the risks of mismanaged identities have never been higher. Organizations face daily challenges in balancing operational efficiency with robust security controls. This is where Identity Access Governance (IAG) becomes essential.
What Is Identity Access Governance?
Identity Access Governance represents a comprehensive approach to managing and overseeing digital identities and their associated access rights across an organization. It encompasses the policies, processes, and technologies that ensure users have appropriate permissions aligned with their roles while maintaining compliance with regulatory requirements.
IAG provides visibility into who can access which systems and data, establishes controls around access provisioning and revocation, and generates audit trails that demonstrate compliance. For organizations dealing with sensitive information or operating in regulated industries, implementing a robust Identity Access Governance framework becomes critical for maintaining both security and operational integrity.
The Core Components of Identity Access Governance

Understanding IAG requires breaking down its fundamental elements:
Identity Lifecycle Management handles the complete journey of user accounts from creation through modification to eventual deactivation. When employees join, change roles, or leave the organization, IAG systems automatically adjust their access rights accordingly. This automation reduces the risk of orphaned accounts or lingering permissions that create security vulnerabilities.
Access Certification and Review involves periodic verification that users maintain only the access they need. Managers and system owners regularly review and validate permissions, identifying excessive privileges or unauthorized access patterns. These reviews form a crucial defense layer against privilege creep and insider threats.
Policy Enforcement ensures consistent application of access control rules across all systems and applications. Organizations define policies based on roles, responsibilities, regulatory requirements, and risk tolerance. IAG platforms then enforce these policies automatically, reducing manual errors and inconsistencies.
Segregation of Duties prevents conflicts of interest by ensuring no single individual holds permissions that could enable fraud or abuse. For example, someone who can approve financial transactions shouldn’t also have the ability to initiate them. IAG systems actively monitor and flag violations of segregation rules.
Reporting and Analytics generate insights into access patterns, compliance status, and potential security risks. Organizations can track metrics like certification completion rates, high-risk access combinations, and policy violations to continually improve their governance posture.
Why Organizations Need Identity Access Governance
The business case for IAG extends beyond simple security concerns. Modern organizations face multiple pressures that make governance essential.
Regulatory Compliance Requirements: Industries such as healthcare, finance, and government operate under strict regulations regarding data access and privacy. Standards like HIPAA, GDPR, PCI DSS, and SOC 2 mandate specific controls around identity management. IAG provides the framework and evidence needed to demonstrate compliance during audits. Organizations can efficiently build GRC programs that align with these regulatory demands.
Reducing Security Breach Risks: According to recent research, 83% of data breaches involve internal actors. Many of these incidents stem from excessive permissions or compromised credentials. IAG limits the potential damage from both malicious insiders and compromised accounts by ensuring users only access what they legitimately need. Regular access reviews help identify and remove unnecessary privileges before they can be exploited.
Managing Complex Hybrid Environments: Organizations today operate across on-premises infrastructure, multiple cloud platforms, and countless SaaS applications. Each environment may have its own identity management approach, creating silos that reduce visibility. IAG provides unified governance across this fragmented infrastructure, enabling consistent policy enforcement regardless of where resources reside.
Operational Efficiency: Manual access provisioning creates bottlenecks that frustrate users and burden IT teams. Employees waiting for access permissions lose productivity, while IT staff spend countless hours processing routine requests. IAG automates routine tasks like granting standard access based on roles, freeing IT teams for higher-value work while accelerating onboarding.
Identity Access Governance vs Identity and Access Management
Many organizations confuse Identity and Access Management (IAM) with IAG, although they serve complementary purposes. IAM focuses on the technical mechanisms of authentication and authorization, verifying who users are and granting them access to resources. Think of IAM as the engine that executes access decisions.
IAG operates at a higher level, providing oversight and control over IAM systems. It answers questions like: “Does this user still need this access?” “Are we complying with our segregation of duties policies?” “Can we prove our access controls meet regulatory requirements?” While IAM handles the tactical execution, IAG provides strategic governance.
For instance, when an employee joins your organization, IAM systems authenticate them and provision their initial access. IAG ensures those access rights align with company policies, tracks changes over time, periodically reviews the appropriateness of those rights, and maintains records for compliance purposes. Both layers work together to create a comprehensive identity security program.
Implementing Effective Identity Access Governance
Successfully deploying IAG requires careful planning and execution across several key areas:
Assessment and Planning: Begin by thoroughly understanding your current state. Document existing identity management processes, catalog all applications and systems requiring governance, identify regulatory requirements and business policies, and assess risks associated with current access practices. This foundation helps prioritize improvements and set realistic implementation timelines.
Establishing Clear Policies: Define specific, enforceable policies around access management. These should cover role definitions and associated permissions, approval workflows for access requests, frequency and scope of access reviews, segregation of duties requirements, and procedures for handling policy violations. Policies must balance security requirements with operational practicality to ensure actual adoption.
Technology Selection and Integration: Choose IAG platforms that integrate with your existing infrastructure. The solution should connect to all critical identity sources and target systems, support your organization’s scale and complexity, provide automation capabilities to reduce manual effort, and offer reporting and analytics tailored to your compliance needs. Organizations should carefully evaluate whether solutions can manage the full digital identity lifecycle across their specific environment.
Automation and Workflow Design: Leverage automation to improve efficiency and consistency. Automate routine tasks like role-based provisioning, access request routing and approval, periodic access reviews and certifications, and policy violation detection and alerting. Well-designed workflows ensure the right people make access decisions at the right time with the right information.
Continuous Monitoring and Improvement: IAG is not a one-time project but an ongoing program. Regularly monitor key metrics like access review completion rates, average time to provision or revoke access, number and types of policy violations, and compliance audit findings. Use these insights to refine policies, improve processes, and enhance automation.
Best Practices for Identity Access Governance
Organizations that excel at IAG typically follow several common practices:
Adopt a Risk-Based Approach: Not all access requires the same level of governance. Focus intensive controls on high-risk areas like privileged accounts, sensitive data access, and production systems. Apply lighter-touch governance to low-risk scenarios to maintain operational efficiency.
Engage Business Stakeholders: IAG cannot succeed as a purely IT-driven initiative. Engage business leaders and process owners who understand operational requirements and can validate access needs. Their input ensures governance policies align with actual business processes rather than creating obstacles.
Start Small and Scale: Rather than attempting to govern everything simultaneously, begin with high-priority systems or user populations. Prove value through initial successes, then gradually expand scope. This approach builds organizational buy-in and allows you to refine processes before enterprise-wide rollout.
Integrate with Zero Trust Principles: Modern security architectures embrace zero trust, which assumes no implicit trust and continuously validates access. IAG naturally supports this model by regularly reviewing and validating access rights rather than granting permanent permissions. Consider how IAG fits within your broader zero trust implementation.
Provide Self-Service Capabilities: Empower users to request access, view their current permissions, and track request status through self-service portals. This improves user experience while reducing IT workload. Automated workflows can handle routine requests without manual intervention.
Maintain Clear Audit Trails: Document all access-related decisions, changes, and reviews. These records prove essential during compliance audits and security investigations. Ensure audit logs capture who made decisions, when they occurred, and the justification provided.
The Future of Identity Access Governance
IAG continues to advance with emerging technologies and changing security requirements. Artificial intelligence and machine learning increasingly augment governance processes by detecting anomalous access patterns, predicting which access reviews require closer scrutiny, and recommending optimal role definitions based on actual usage patterns.
Cloud-native architectures demand governance models that work seamlessly across distributed environments. Organizations require unified visibility and control whether users access resources through traditional networks or modern cloud platforms. The rise of machine identities, service accounts, and API keys adds complexity that governance programs must address.
Integration with broader security ecosystems enables IAG platforms to consume risk signals from threat detection tools, endpoint security solutions, and security information and event management systems. This context enriches access decisions and helps prioritize governance activities based on real-time risk.
Taking Action on Identity Access Governance
For organizations beginning their IAG journey, start by conducting a thorough assessment of your current identity management practices. Identify gaps in visibility, control, and compliance, then prioritize improvements based on risk and business impact. Engage stakeholders across IT, security, compliance, and business units to ensure governance policies serve organizational needs.
Invest in identity access governance capabilities that align with your technical environment and business requirements. Whether building on existing IAM infrastructure or deploying new platforms, ensure solutions provide the automation, integration, and reporting capabilities your organization needs to succeed.
Identity Access Governance represents a critical capability for modern organizations facing increasing security threats, complex technical environments, and stringent compliance requirements. By implementing comprehensive IAG practices, organizations gain visibility into access rights, reduce security risks, streamline operations, and demonstrate compliance with confidence. The investment in proper governance pays dividends through improved security posture, operational efficiency, and regulatory readiness.
Taking Action on Identity Access Governance
For organizations beginning their IAG journey, start by conducting a thorough assessment of your current identity management practices. Identify gaps in visibility, control, and compliance, then prioritize improvements based on risk and business impact. Engage stakeholders across IT, security, compliance, and business units to ensure governance policies serve organizational needs.
Invest in identity access governance capabilities that align with your technical environment and business requirements. Whether building on existing IAM infrastructure or deploying new platforms, ensure solutions provide the automation, integration, and reporting capabilities your organization needs to succeed.
Identity Access Governance represents a critical capability for modern organizations facing increasing security threats, complex technical environments, and stringent compliance requirements. By implementing comprehensive IAG practices, organizations gain visibility into access rights, reduce security risks, streamline operations, and demonstrate compliance with confidence. The investment in proper governance pays dividends through improved security posture, operational efficiency, and regulatory readiness.
See also:



