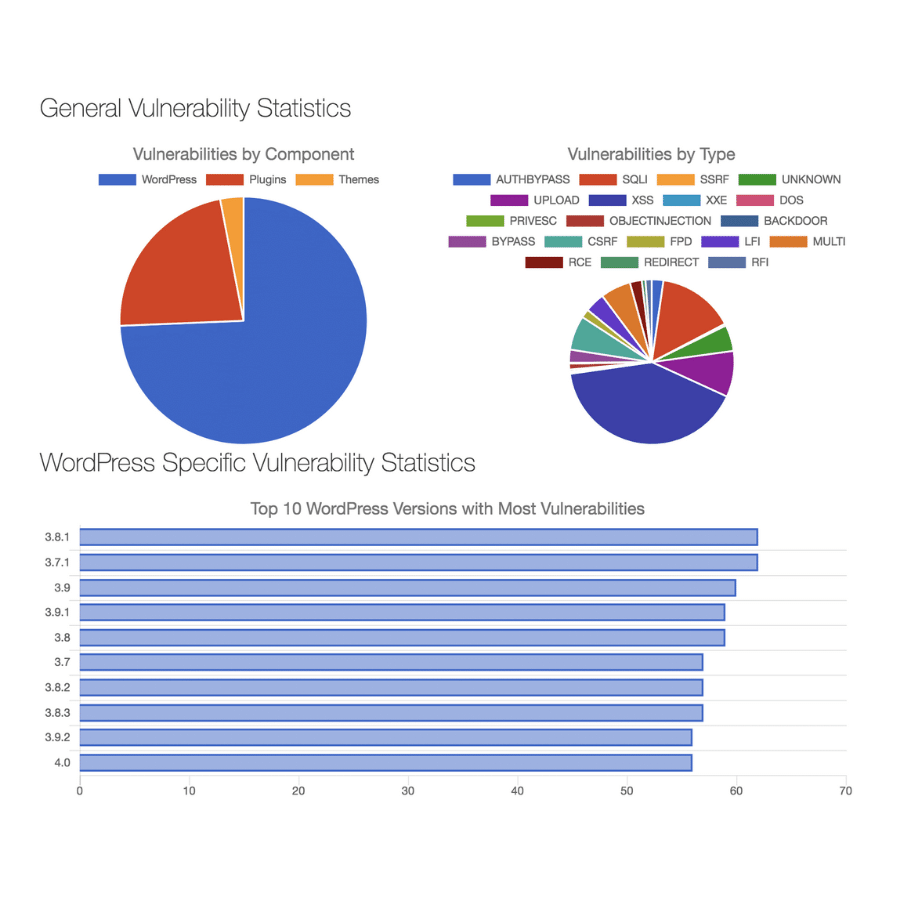
Millions of websites are powered by WordPress, one of the most popular open-source CMS tools. Although WordPress makes it simple for anybody to create a website fast, there is a lot of discussion about its many security issues.
Hundreds of thousands of WordPress sites and eCommerce sites get hacked yearly. Vulnerabilities in the latest WordPress core software exist and are a way for hackers to gain access. Although rare, the most prevalent form of compromise are entirely preventable issues, like not keeping plugins updated or using insecure passwords.
Security impacts all users of the website’s ecosystem. There’s no one specific topic, target, or audience when it comes to website security. WordPress, the most CMS used, is also most attacked by malicious actors.
It has been reported that over 90 billion malicious login attempts from over 57 million different IP addresses were made against WordPress at a rate of 2,800 cyberattacks per second. By far, the most common attack vector targeting WordPress sites involved malicious login attempts. Credential stuffing attacks exploiting stolen credential lists, dictionary attacks, and classic brute-force attacks were among the other approaches.
Millions of websites are powered by WordPress, one of the most popular open-source CMS tools. Although WordPress makes it simple for anybody to create a website fast, there is a lot of discussion about its many security issues.
Hundreds of thousands of WordPress sites and eCommerce sites get hacked yearly. Vulnerabilities in the latest WordPress core software exist and are a way for hackers to gain access. Although rare, the most prevalent form of compromise are entirely preventable issues, like not keeping plugins updated or using insecure passwords.
Security impacts all users of the website’s ecosystem. There’s no one specific topic, target, or audience when it comes to website security. WordPress, the most CMS used, is also most attacked by malicious actors.
It has been reported that over 90 billion malicious login attempts from over 57 million different IP addresses were made against WordPress at a rate of 2,800 cyberattacks per second. By far, the most common attack vector targeting WordPress sites involved malicious login attempts. Credential stuffing attacks exploiting stolen credential lists, dictionary attacks, and classic brute-force attacks were among the other approaches.
What are the common API Attacks?
- Outdated Core Software, Plugins, and Themes
- Unauthorized logins
- Weak Passwords and Lack of MFA
- SQL Injection
- Cross-Site Scripting
- Denial of Service Attack
- Malware
- File Inclusion Exploits
A critical remote code vulnerability in the Elementor plugin was patched on April 12th by a significant security update. This vulnerability (v5.0.4) allows authorized users, including subscribers, to upload and execute arbitrary PHP code on a vulnerable website. The severity of this vulnerability, CVE-2022-1329, is very high. Elementor has more than 5 million active installations as of this date; you can imagine the impact on vulnerable websites which are not patched promptly.
WordPress Common Security Issues
- Outdated Core Software, Plugins, and Themes
- Unauthorized logins
- Weak Passwords and Lack of MFA
- SQL Injection
- Cross-Site Scripting
- Denial of Service Attack
- Malware
- File Inclusion Exploits
Weak Passwords
One of the most severe security issues you may easily prevent is using a weak password. Your WordPress admin password should be strong and contain various letters, symbols, and numbers. Furthermore, your password should be unique to your WordPress site and not be used anywhere else. Remember, if you are getting your website developed by a 3rd-party, you need to enforce the same conditions onto them – don’t be left in the dark.
Hackers used software known as bots to attack login pages, attempting several combinations of usernames and passwords to gain access to a website. Bots may often try hundreds of combinations every minute, breaking through using dictionary keywords and widely used passwords.
If they succeed, the hacker will have complete access to your website.
Outdated Core Software, Plugins, and Themes
Outdated Core Software, plugins, themes, and other components make most WordPress sites vulnerable to cyberattacks. Security researchers say over 50% of infected WordPress websites were outdated.
WordPress release updates every three months so far. These updates contain patches to fix bugs and security vulnerabilities in the system. For instance, newer WordPress versions fix many significant vulnerabilities, including cross-site scripting (XSS) vulnerabilities in the block editor. Therefore, in addition to increasing security, upgrading your core files may also assist your site’s efficiency, performance, and compatibility.
Poorly implemented, insecure or outdated plugins and themes are a common way to exploit WP websites. Developers write plugins and themes. Developers can have mistakes in writing the code, leading to vulnerability and easily exploited by attackers.
Malware
WordPress malware can alter how users experience your website. Hackers can infect legitimate website files with malware, add malicious code to existing files to steal information, or take complete control with remote code execution using web shells.
Some malware like backdoors are not easy to detect; preventing them is the only solution. Usually, malware requires an entry point from where it is accessible to the hacker.
WordPress is not vulnerable to all malware attacks, even though thousands of different attack methods exist on the internet. The four most common malware attacks on WordPress are.
• Backdoors
• Drive-by Downloads
• Cryptomining
• Malvertising Hacks
Malware can be prevented by making the environment difficult to access. Blocking suspicious IPs, two-factor authentication, and limited admin access can also help prevent malware.
SQL Injections
WordPress sites are vulnerable to this type of attack since databases are involved in storing content. SQL injections are widely used by attackers in visitor-facing submission forms such as contact forms, payment fields, and lead forms. When hackers fill out these forms, they’re looking to take advantage of missing input validation, sending code that will execute and invoke commands to the database.
During a SQL injection, a hacker has direct access to and modification of your website’s database. Attackers may use SQL to create new accounts on your site, add illegal links and content, and leak, change, and delete data. An attacker may be able to establish a new admin-level user account via SQL injection, which may subsequently be exploited to log in and get full access to your WordPress website. SQL injections can also enter new information into your database, such as links to malicious or spam websites.
Weak Passwords
One of the most severe security issues you may easily prevent is using a weak password. Your WordPress admin password should be strong and contain various letters, symbols, and numbers. Furthermore, your password should be unique to your WordPress site and not be used anywhere else. Remember, if you are getting your website developed by a 3rd-party, you need to enforce the same conditions onto them – don’t be left in the dark.
Hackers used software known as bots to attack login pages, attempting several combinations of usernames and passwords to gain access to a website. Bots may often try hundreds of combinations every minute, breaking through using dictionary keywords and widely used passwords.
If they succeed, the hacker will have complete access to your website.
Outdated Core Software, Plugins, and Themes
Outdated Core Software, plugins, themes, and other components make most WordPress sites vulnerable to cyberattacks. Security researchers say over 50% of infected WordPress websites were outdated.
WordPress release updates every three months so far. These updates contain patches to fix bugs and security vulnerabilities in the system. For instance, newer WordPress versions fix many significant vulnerabilities, including cross-site scripting (XSS) vulnerabilities in the block editor. Therefore, in addition to increasing security, upgrading your core files may also assist your site’s efficiency, performance, and compatibility.
Poorly implemented, insecure or outdated plugins and themes are a common way to exploit WP websites. Developers write plugins and themes. Developers can have mistakes in writing the code, leading to vulnerability and easily exploited by attackers.
Malware
WordPress malware can alter how users experience your website. Hackers can infect legitimate website files with malware, add malicious code to existing files to steal information, or take complete control with remote code execution using web shells.
Some malware like backdoors are not easy to detect; preventing them is the only solution. Usually, malware requires an entry point from where it is accessible to the hacker.
WordPress is not vulnerable to all malware attacks, even though thousands of different attack methods exist on the internet. The four most common malware attacks on WordPress are.
- Backdoors
- Drive-by Downloads
- Cryptomining
- Malvertising Hacks
Malware can be prevented by making the environment difficult to access. Blocking suspicious IPs, two-factor authentication, and limited admin access can also help prevent malware.
SQL Injections
WordPress sites are vulnerable to this type of attack since databases are involved in storing content. SQL injections are widely used by attackers in visitor-facing submission forms such as contact forms, payment fields, and lead forms. When hackers fill out these forms, they’re looking to take advantage of missing input validation, sending code that will execute and invoke commands to the database.
During a SQL injection, a hacker has direct access to and modification of your website’s database. Attackers may use SQL to create new accounts on your site, add illegal links and content, and leak, change, and delete data. An attacker may be able to establish a new admin-level user account via SQL injection, which may subsequently be exploited to log in and get full access to your WordPress website. SQL injections can also enter new information into your database, such as links to malicious or spam websites.
Cross-Site Scripting (XSS)
Cross-Site Scripting is also the most common vulnerability in WordPress. More than 50% of the vulnerabilities disclosed in WP sites were related to Cross-Site Scripting. Cross-Site Scripting (XSS) occurs when an attacker inserts malicious code into the website’s backend code. In that attacker’s attempt to plant code that executes in your files, XSS attacks are comparable to database injections; XSS primarily targets web page functionality. Once they have access to your front-end display, hackers may attempt to damage visitors by disclosing a disguised link to a malfunctioning website or showing a fake contact form to collect user information.
Cross-Site Scripting (XSS)
Cross-Site Scripting is also the most common vulnerability in WordPress. More than 50% of the vulnerabilities disclosed in WP sites were related to Cross-Site Scripting. Cross-Site Scripting (XSS) occurs when an attacker inserts malicious code into the website’s backend code. In that attacker’s attempt to plant code that executes in your files, XSS attacks are comparable to database injections; XSS primarily targets web page functionality. Once they have access to your front-end display, hackers may attempt to damage visitors by disclosing a disguised link to a malfunctioning website or showing a fake contact form to collect user information.
Best Practices to Protect Your WordPress Site
Installing Security Plugins
A robust security plugins, such as Malcare, Wordfence Security, Defender, and Sucuri, are some of the best defenses to your WordPress against hackers.
A WordPress security plugin should include a malware scanner and cleanup functionality. It should ideally have a firewall, brute-force protection, bot protection, and activity log monitoring.
Most WP security scanners alert the admin if they find any vulnerability in the system. Wordfence is a comprehensive and full-featured security plugin for WordPress. It allows users to automate and manage the security of their website thoroughly. With Wordfence, you can scan your WordPress website for vulnerabilities and receive email alerts if any risks surface. This security plugin supports advanced login security measures and can automatically ban IPs based on suspicious activities.
Enabling Two Factor Authentication
Two-factor authentication protects your WordPress login by adding an extra layer of security. To login, you must enter a time-sensitive code from another device, such as your smartphone by integrating with Google Authenticator or another OTP platform, in addition to your password.
Two-factor authentication is one of the simplest ways to secure your WordPress login and almost eliminates the possibility of successful brute-force attacks. WP site can be secure by enabling plugins like WP 2FA or Google Authenticator.
Use Strong Password
Strong passwords can help maintain the WP site integrity and prevent major password guessing and brute-force attacks. If the attacker guesses your user or admin credentials, the attacker will have the privilege to do authorized tasks. Always use a strong password or a password manager plugin for WordPress like WPassword. Strong password policies keep your website safe and enable users to have secure passwords.
WordPress Activity Logs and Records
Maintaining a WordPress activity record is another easily recommended practice for security with WordPress. This enables you to keep track of essentially anything that occurs on your website, from failed login attempts to modifications in files. Plugins like WPActivity log can keep a record of everything on our website, monitor user productivity, and identify malicious activities on WordPress Site.
Implementing WordPress Firewall
Web Application Firewalls (WAFs) known as WordPress firewalls, are specifically designed to protect WordPress sites from malicious attacks. They employ known signatures, which are lists of known attacks; when the payload of an HTTP request matches a signature, the request is malicious. A WordPress firewall works similarly to malware detection software in identifying harmful requests.
WordPress Version Disclosure
WordPress reveals its version by default in various settings like many other online apps. Although version disclosure isn’t strictly a security vulnerability, the information is tremendously helpful to an attacker when preparing an attack. Disabling WordPress’s version disclosure features might make a cyberattack a bit more challenging. A lot of version information is leaked by WordPress which can help bypass different parameters to exploit the site.
Mishandling the Errors
Error reporting is another aspect that is frequently disregarded. A theme or plugin that isn’t functioning correctly may provide an error message. When troubleshooting, this is undoubtedly useful; mostly these errors contain the Server Path. If a hacker has access to these error messages, they will be able to view your whole server path and will follow the route to install a malicious virus or back door into our website. Although error reporting might be helpful, it is safest to disable them.
WordPress Backup and Snapshot
A critical feature of any WordPress security approach should be a backup method. Create a backup schedule and confirm that you’re sending backups securely off-site to a remote WordPress backup location. If you need to restore your site from a fresh backup, ensure that your backup plan includes a recovery component.
Limit Login Attempts
WordPress, by default, permits users to attempt to log in as many times as they want. This makes brute-force attacks on your WordPress website possible. Hackers test various login combinations to crack passwords. Limiting the number of unsuccessful login attempts a person may make can quickly address this. WordPress Plugins like Login LockDown records every unsuccessful login attempt is timestamped and given its IP address. The login feature is turned off for all requests coming from a certain IP range if more than a particular number of tries are discovered in a short amount of time from that IP range. By doing this, brute force password discovery is minimized.
Disabling WordPress XML-RPC
WordPress XML-RPC is an API that enables data transfer between your WordPress website and other systems. Xmplrpc.php is responsible for allowing the pingbacks and trackbacks in addition to data transfer. These are the alerts you get when a blog or other website linking to yours links to another one. By sending a lot of pingbacks, hackers can perform DDoS attacks on xmlrpc.php and take down your website, or as you can say, make it unavailable to visitors. Xmplrpc.php delivers the authentication data with each request. It makes it simpler to push a lot of data all at once. However, the capacity to transfer a lot of data at once indicates that even hackers could get into a lot of passwords. You have two options for disabling the XML-RPC function on your WordPress website: manually or with a plugin. Because adopting a plugin is quicker, easier, and risk-free, we advise doing that. Making changes to your WordPress files is always dangerous when using the manual method.
Best Practices to Protect Your WordPress Site
Installing Security Plugins
A robust security plugins, such as Malcare, Wordfence Security, Defender, and Sucuri, are some of the best defenses to your WordPress against hackers.
A WordPress security plugin should include a malware scanner and cleanup functionality. It should ideally have a firewall, brute-force protection, bot protection, and activity log monitoring.
Most WP security scanners alert the admin if they find any vulnerability in the system. Wordfence is a comprehensive and full-featured security plugin for WordPress. It allows users to automate and manage the security of their website thoroughly. With Wordfence, you can scan your WordPress website for vulnerabilities and receive email alerts if any risks surface. This security plugin supports advanced login security measures and can automatically ban IPs based on suspicious activities.
Enabling Two Factor Authentication
Two-factor authentication protects your WordPress login by adding an extra layer of security. To login, you must enter a time-sensitive code from another device, such as your smartphone by integrating with Google Authenticator or another OTP platform, in addition to your password.
Two-factor authentication is one of the simplest ways to secure your WordPress login and almost eliminates the possibility of successful brute-force attacks. WP site can be secure by enabling plugins like WP 2FA or Google Authenticator. https://www.yubico.com/pk/store/
Use Strong Password
Strong passwords can help maintain the WP site integrity and prevent major password guessing and brute-force attacks. If the attacker guesses your user or admin credentials, the attacker will have the privilege to do authorized tasks. Always use a strong password or a password manager plugin for WordPress like WPassword. Strong password policies keep your website safe and enable users to have secure passwords.
WordPress Activity Logs and Records
Maintaining a WordPress activity record is another easily recommended practice for security with WordPress. This enables you to keep track of essentially anything that occurs on your website, from failed login attempts to modifications in files. Plugins like WPActivity log can keep a record of everything on our website, monitor user productivity, and identify malicious activities on WordPress Site.
Implementing WordPress Firewall
Web Application Firewalls (WAFs) known as WordPress firewalls, are specifically designed to protect WordPress sites from malicious attacks. They employ known signatures, which are lists of known attacks; when the payload of an HTTP request matches a signature, the request is malicious. A WordPress firewall works similarly to malware detection software in identifying harmful requests.
WordPress Version Disclosure
WordPress reveals its version by default in various settings like many other online apps. Although version disclosure isn’t strictly a security vulnerability, the information is tremendously helpful to an attacker when preparing an attack. Disabling WordPress’s version disclosure features might make a cyberattack a bit more challenging. A lot of version information is leaked by WordPress which can help bypass different parameters to exploit the site.
Mishandling the Errors
Error reporting is another aspect that is frequently disregarded. A theme or plugin that isn’t functioning correctly may provide an error message. When troubleshooting, this is undoubtedly useful; mostly these errors contain the Server Path. If a hacker has access to these error messages, they will be able to view your whole server path and will follow the route to install a malicious virus or back door into our website. Although error reporting might be helpful, it is safest to disable them.
WordPress Backup and Snapshot
A critical feature of any WordPress security approach should be a backup method. Create a backup schedule and confirm that you’re sending backups securely off-site to a remote WordPress backup location. If you need to restore your site from a fresh backup, ensure that your backup plan includes a recovery component.
Limit Login Attempts
WordPress, by default, permits users to attempt to log in as many times as they want. This makes brute-force attacks on your WordPress website possible. Hackers test various login combinations to crack passwords. Limiting the number of unsuccessful login attempts a person may make can quickly address this. WordPress Plugins like Login LockDown records every unsuccessful login attempt is timestamped and given its IP address. The login feature is turned off for all requests coming from a certain IP range if more than a particular number of tries are discovered in a short amount of time from that IP range. By doing this, brute force password discovery is minimized.
Disabling WordPress XML-RPC
WordPress XML-RPC is an API that enables data transfer between your WordPress website and other systems. Xmplrpc.php is responsible for allowing the pingbacks and trackbacks in addition to data transfer. These are the alerts you get when a blog or other website linking to yours links to another one. By sending a lot of pingbacks, hackers can perform DDoS attacks on xmlrpc.php and take down your website, or as you can say, make it unavailable to visitors. Xmplrpc.php delivers the authentication data with each request. It makes it simpler to push a lot of data all at once. However, the capacity to transfer a lot of data at once indicates that even hackers could get into a lot of passwords. You have two options for disabling the XML-RPC function on your WordPress website: manually or with a plugin. Because adopting a plugin is quicker, easier, and risk-free, we advise doing that. Making changes to your WordPress files is always dangerous when using the manual method.
See also: