- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Rogue Access Point Detection
False negative occurs when the wireless intrusion prevention system fails to detect an access point actually connected to the secure network as wired rogue. False negatives result in security holes.
To prevent the installation of rogue access points, organizations can install wireless intrusion prevention systems to monitor the radio spectrum for unauthorized access points. Presence of a large number of wireless access points can be sensed in airspace of a typical enterprise facility. These include managed access points in the secure network plus access points in the neighborhood. A wireless intrusion prevention system facilitates the job of auditing these access points on a continuous basis to learn whether there are any rogue access points among them.
To prevent the installation of rogue access points, organizations can install wireless intrusion prevention systems to monitor the radio spectrum for unauthorized access points. Presence of a large number of wireless access points can be sensed in airspace of a typical enterprise facility. These include managed access points in the secure network plus access points in the neighborhood. A wireless intrusion prevention system facilitates the job of auditing these access points on a continuous basis to learn whether there are any rogue access points among them.
Wireless Intrusion Prevention Systems (WIPS)...
- whether or not the access point is in the managed access point list
- whether or not it is connected to the secure network
The first of the above two conditions is easy to test – compare wireless MAC address (also called as BSSID) of the access point against the managed access point BSSID list. However, automated testing of the second condition can become challenging in the light of following factors: a) Need to cover different types of access point devices such as bridging, NAT (router), unencrypted wireless links, encrypted wireless links, different types of relations between wired and wireless MAC addresses of access points, and soft access points, b) necessity to determine access point connectivity with acceptable response time in large networks, and c) requirement to avoid both false positives and negatives which are described below.
Wireless Intrusion Prevention Systems (WIPS)...
- whether or not the access point is in the managed access point list
- whether or not it is connected to the secure network
The first of the above two conditions is easy to test – compare wireless MAC address (also called as BSSID) of the access point against the managed access point BSSID list. However, automated testing of the second condition can become challenging in the light of following factors: a) Need to cover different types of access point devices such as bridging, NAT (router), unencrypted wireless links, encrypted wireless links, different types of relations between wired and wireless MAC addresses of access points, and soft access points, b) necessity to determine access point connectivity with acceptable response time in large networks, and c) requirement to avoid both false positives and negatives which are described below.
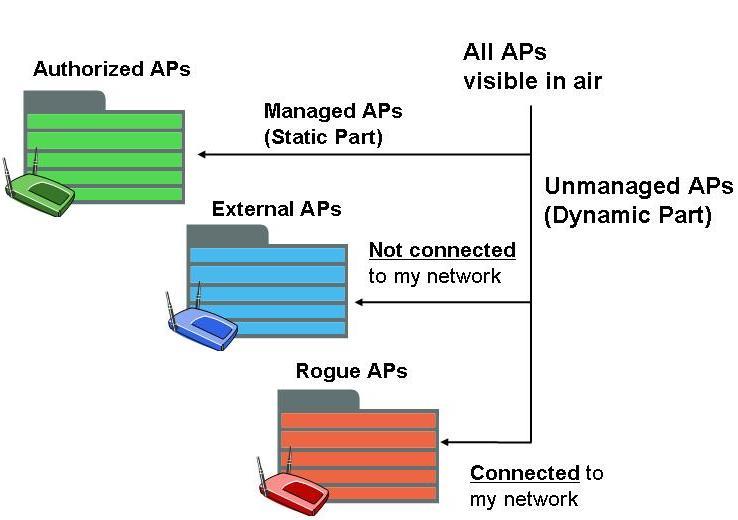
If an unauthorized access point is found connected to the secure network, it is the rogue access point of the first kind (also called as “wired rogue”). On the other hand, if the unauthorized access point is found not connected to the secure network, it is an external access points. Among the external access points, if any is found to be mischievous or potential risk (e.g., whose settings can attract or have already attracted secure network wireless clients), it is tagged as rogue access point of the second kind, which is often called an “evil twin”.
If an unauthorized access point is found connected to the secure network, it is the rogue access point of the first kind (also called as “wired rogue”). On the other hand, if the unauthorized access point is found not connected to the secure network, it is an external access points. Among the external access points, if any is found to be mischievous or potential risk (e.g., whose settings can attract or have already attracted secure network wireless clients), it is tagged as rogue access point of the second kind, which is often called an “evil twin”.
Type 1: Any AP Other than Mine Is Rogue!
Any AP other than authorized AP is rogue. Network connectivity of AP to enterprise network is not a criterion for rogue detection. Administrator will have to painstakingly manually separate out friendly neighbor APs. The manual inspection needs to be done on ongoing basis as new neighborhood APs pop up and old ones are reconfigured. If manual inspection is not promptly and regularly done, it creates security hole. Needless to say that automatic prevention of rogue APs cannot be turned on as administrator will have to first decide if a newly detected AP is on the network or just a friendly neighborhood AP.
Type 1: Any AP Other than Mine Is Rogue!
Any AP other than authorized AP is rogue. Network connectivity of AP to enterprise network is not a criterion for rogue detection. Administrator will have to painstakingly manually separate out friendly neighbor APs. The manual inspection needs to be done on ongoing basis as new neighborhood APs pop up and old ones are reconfigured. If manual inspection is not promptly and regularly done, it creates security hole. Needless to say that automatic prevention of rogue APs cannot be turned on as administrator will have to first decide if a newly detected AP is on the network or just a friendly neighborhood AP.
Type 2: AP Other Than Mine Is Rogue, Unless It Matches Pre-configured Wireless Side Properties For Friendly Neighbor APs.
Manual inspection: If legitimate neighbor APs change their wireless side settings or if new friendly neighbor APs are deployed, they will not fit the pre-configured template for friendly neighbors. So turning on automatic prevention is a risk as well as frequent manual inspection will be required.
Type 2: AP Other Than Mine Is Rogue, Unless It Matches Pre-configured Wireless Side Properties For Friendly Neighbor APs.
Manual inspection: If legitimate neighbor APs change their wireless side settings or if new friendly neighbor APs are deployed, they will not fit the pre-configured template for friendly neighbors. So turning on automatic prevention is a risk as well as frequent manual inspection will be required.
Type 3: AP Other than Mine Is Rogue, If It Is Connected To My Network.
Automatic prevention can be safely turned on and there is no security lapse. No manual effort is required either at the beginning to configure any neighborhood AP properties templates or on ongoing basis as new APs come up and old ones change their properties.
Type 3: AP Other than Mine Is Rogue, If It Is Connected To My Network.
AP’s connectivity to monitored enterprise network is essential criterion in AP classification as the rogue AP threat definition mandates; of course in addition to that the AP is not on the authorized AP list. Wired network connectivity of every AP visible in air is instantly, automatically and accurately determined by the system. If it is not on the authorized AP list and connected to the monitored network, it is rogue access point. If it is not on the authorized AP list and not connected to the monitored enterprise network, it is external (friendly neighbor) AP.
Automatic prevention can be safely turned on and there is no security lapse. No manual effort is required either at the beginning to configure any neighborhood AP properties templates or on ongoing basis as new APs come up and old ones change their properties.
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Sama Tower, Floor 7
Moh. Thunayan AlGhanim Str.
Jibla, Kuwait City
Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.