- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
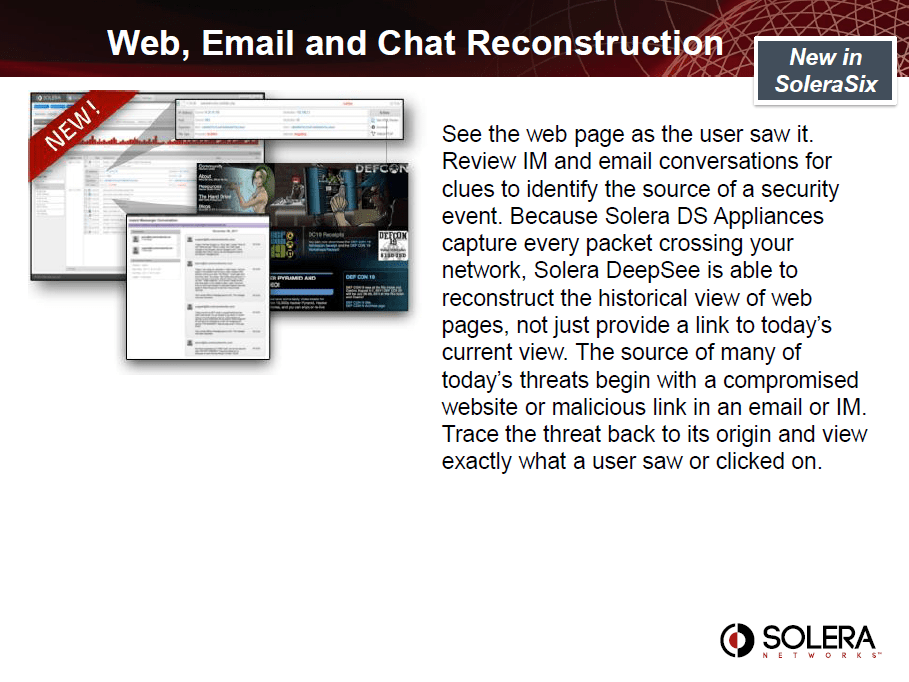
Network Security Analytics and Forensics
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Despite the allure of purchasing every security tool from the same vendor, in a world where almost 8,000 malware signatures are created EVERY DAY, enterprises must rely on the innovative technologies that address today’s ever-evolving threat landscape. When assessing security products and services, security teams should think in terms of best-of-breed integration to deliver end-to-end threat detection, analysis, and containment.
Network Security Analytics
To combat today’s sophisticated attacks, administrators and incident responders require the best equipment and the deepest visibility into the activities, applications, and personas on their network. They need the ability to react quickly to events in real time within the full context of the event, because the stakes, whether reputation, financial loss, or market cap exposure are too high. Every second matters. The difference between “set it and forget it” and the active response approach is data. Network Security Analytics can make sense of the data and provide actionable evidence on how to defend your network.
Network Security Analytics
To combat today’s sophisticated attacks, administrators and incident responders require the best equipment and the deepest visibility into the activities, applications, and personas on their network. They need the ability to react quickly to events in real time within the full context of the event, because the stakes, whether reputation, financial loss, or market cap exposure are too high. Every second matters. The difference between “set it and forget it” and the active response approach is data. Network Security Analytics can make sense of the data and provide actionable evidence on how to defend your network.
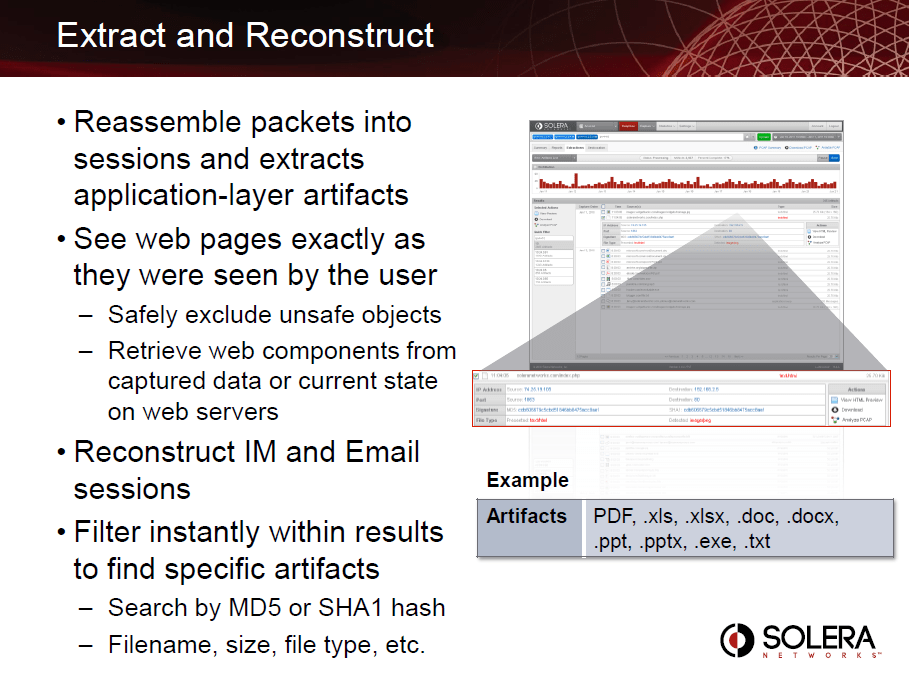
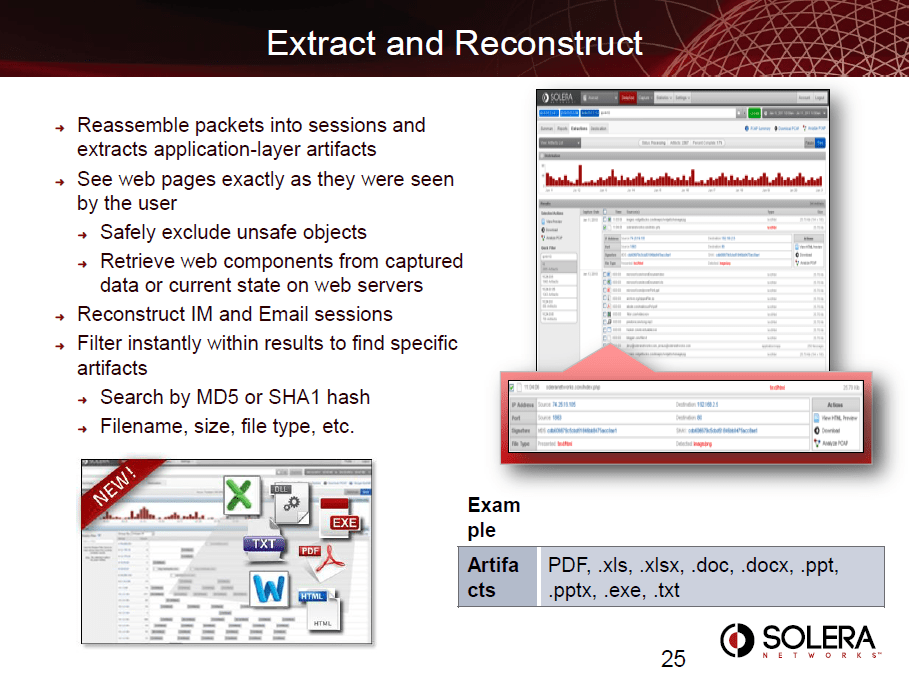
Packet Capture
Packet Capture
Network Forensics
Network Security Analytics
Network Forensics
Network Security Analytics
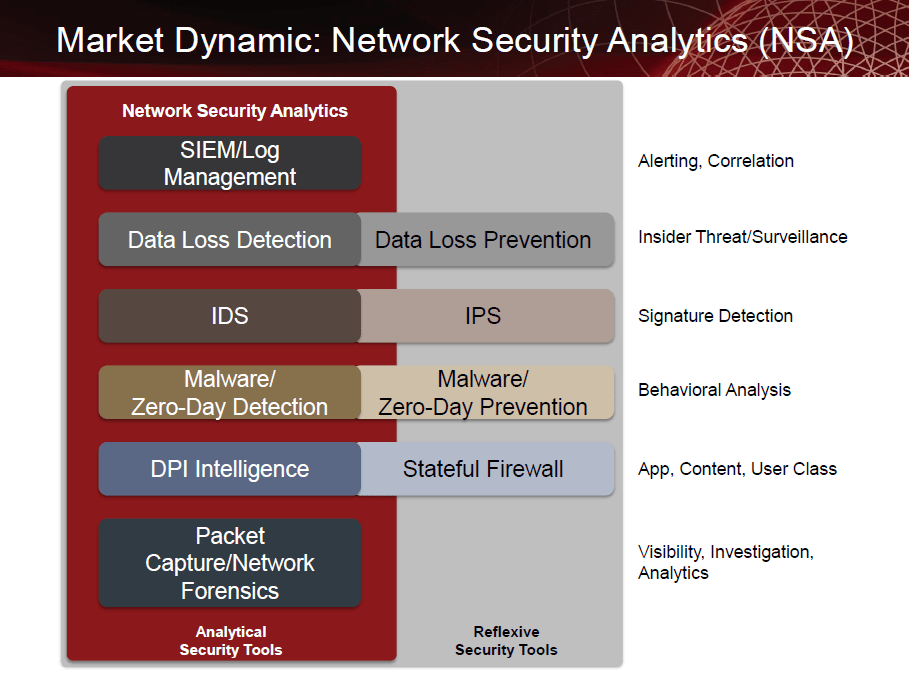
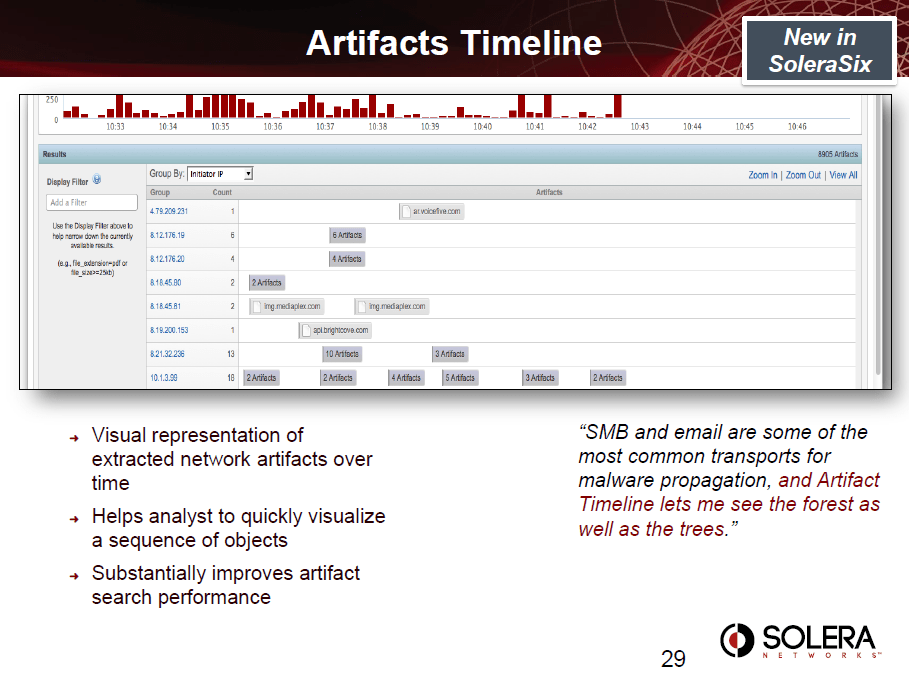
Network Security Analytics takes network forensics beyond captured and indexed network data into an environment where analysts can work across best-of-breed tools and have their difficult security questions answered using application-layer attributes. Network Security Analytics integrates Security Information Event Management (SIEM), Log Management, Intrusion Detection Systems (IDS), Data Loss Prevention (DLP), Deep Packet Inspection, and malware detection tools into the single workflow necessary to combat today’s threats.
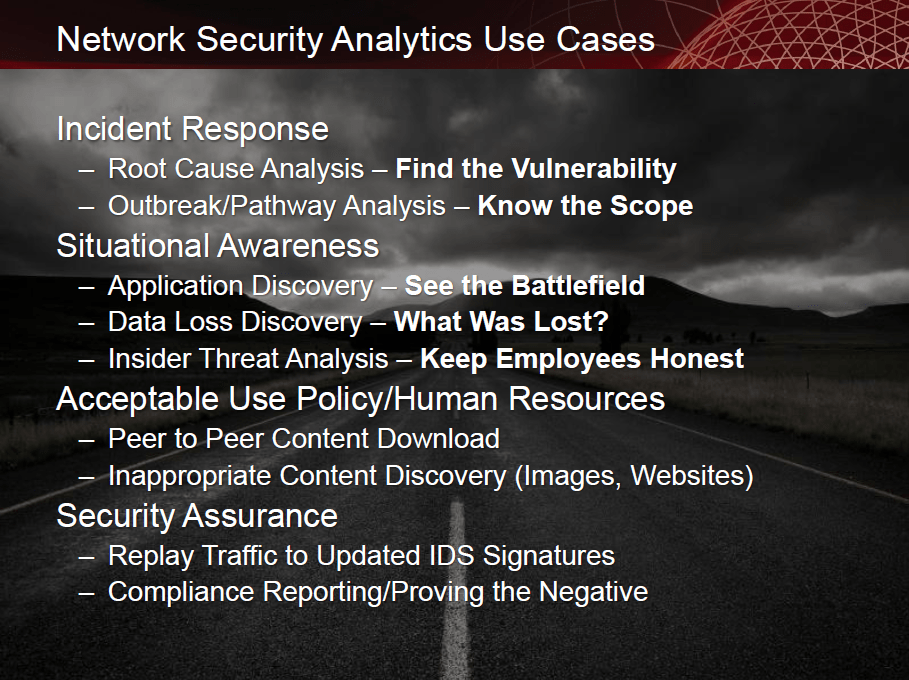
Incident Response
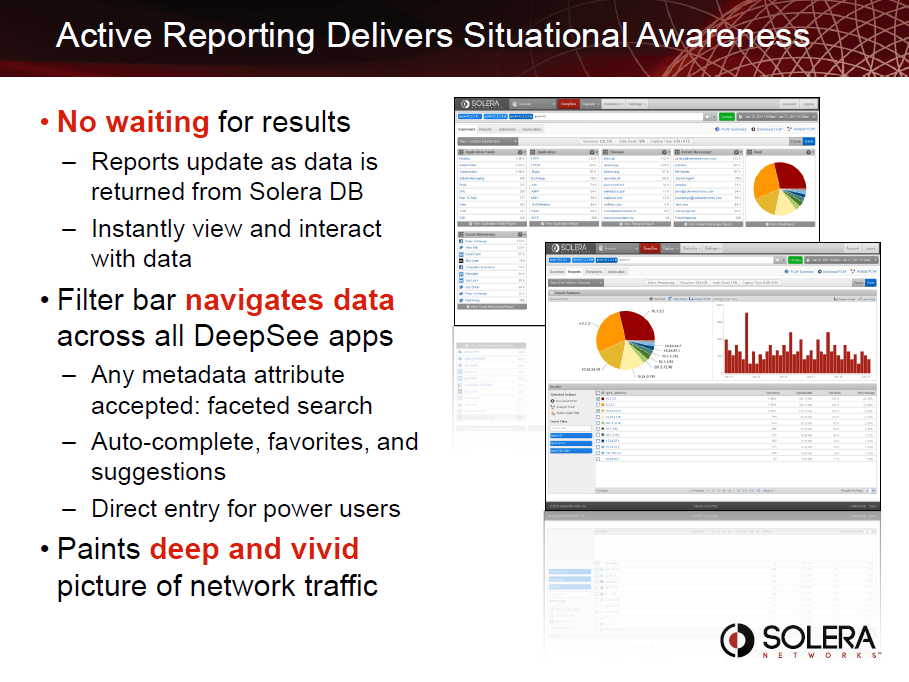
Situational Awareness
Network Security Analytics addresses the following needs:
Incident Response
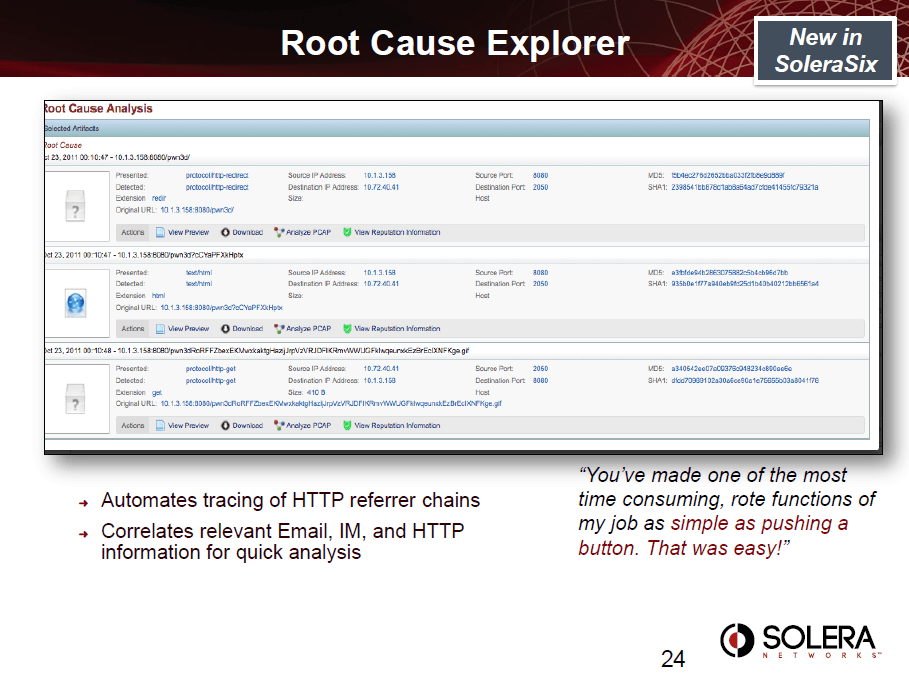
Root Cause Analysis – Solera DS Appliances give you the ability to go back in time from any security event to find the root cause. Also called the “t-minus zero” analysis, it fills the hole that is often left by traditional IPS/IDS, DLP, and Malware devices, where only metadata and log analysis are available. However, when coupled with a full forensic record of the packets, flows, and artifacts, security analysis can not only tell when something happened, but identify what it was, and how it got into the network. Having full context at the packet-level gives users the ability to shorten the time it takes to resolve the incident and minimizes the scope of current and future potential breaches. Solera DS Appliances can help you find and close the initial vulnerability to make your network more secure.
Outbreak/Pathway Analysis – Sometimes called the “t-plus zero,” this type of analysis goes forward in time from any security trigger to discover the full scope of the event. Again, since traditional security tools can only trigger alerts based on a specific moment in time, Solera DS Appliances are required in order to discover everywhere the event has traveled in your network so you can remediate.
Situational Awareness
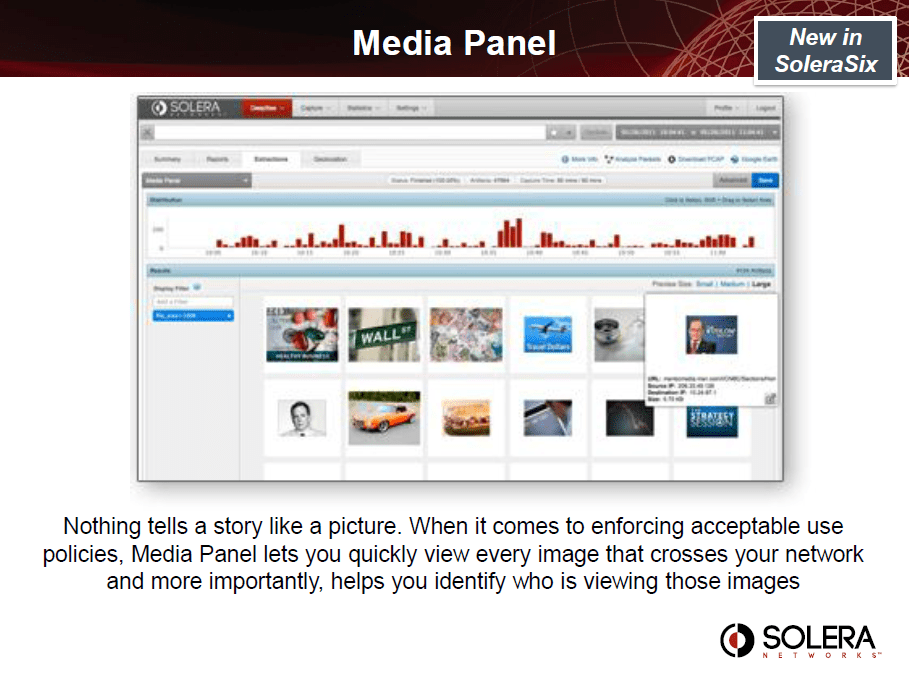
Acceptable Use Policy/Human Resources
Security Assurance
Acceptable Use Policy/Human Resources
Inappropriate Content Discovery – Your company may have an Acceptable Use Policy prohibiting users from downloading inappropriate content, but catching employees violating this policy can be difficult. Web filtering technology is often woefully inadequate, but Solera Networks provides the definitive proof you need to take swift action with the employee. With clear evidence, employees will often strictly align with policies and you are able to avoid costly expenses of termination and re-hiring, let alone legal action.
Security Assurance
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Sama Tower, Floor 7
Moh. Thunayan AlGhanim Str.
Jibla, Kuwait City
Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.