Most organizations assume their SharePoint environment is secure. After all, it’s Microsoft’s platform with enterprise-grade security, right? Tell that to the companies discovering months-old breaches where attackers used legitimate SharePoint features to exfiltrate terabytes of sensitive data without triggering a single security alert.
Your organization’s SharePoint systems could be under attack right now, and you might not even know it. A recently disclosed Microsoft SharePoint remote code execution (RCE) vulnerability, tracked as CVE-2024-38094, is being exploited to gain initial access to corporate networks, and this is just the tip of the iceberg.
The recent surge in SharePoint Online attacks reveals a disturbing pattern. Cybercriminals have weaponized your trusted productivity platform, turning collaborative features into attack vectors. Understanding how they operate across the attack matrix gives you the defensive advantage you need.
Why SharePoint Becomes an Attack Target
A SharePoint environment contains everything attackers want: sensitive documents, user credentials, and direct access to a broader Microsoft 365 ecosystem. Unlike traditional network attacks that trigger security alerts, SharePoint attacks blend with normal user activity.
Consider this scenario: an attacker Google Dorks your SharePoint URLs, discovers anonymous share links containing financial reports, and proceeds to use Graph Search to discover additional high-value libraries. Your security products flag legitimate SharePoint API requests, not reconnaissance.
This invisibility makes SharePoint attacks particularly dangerous. DTS Solution’s red team assessments consistently find organizations with robust network security but completely exposed SharePoint environments.
The SharePoint Online Attack Matrix
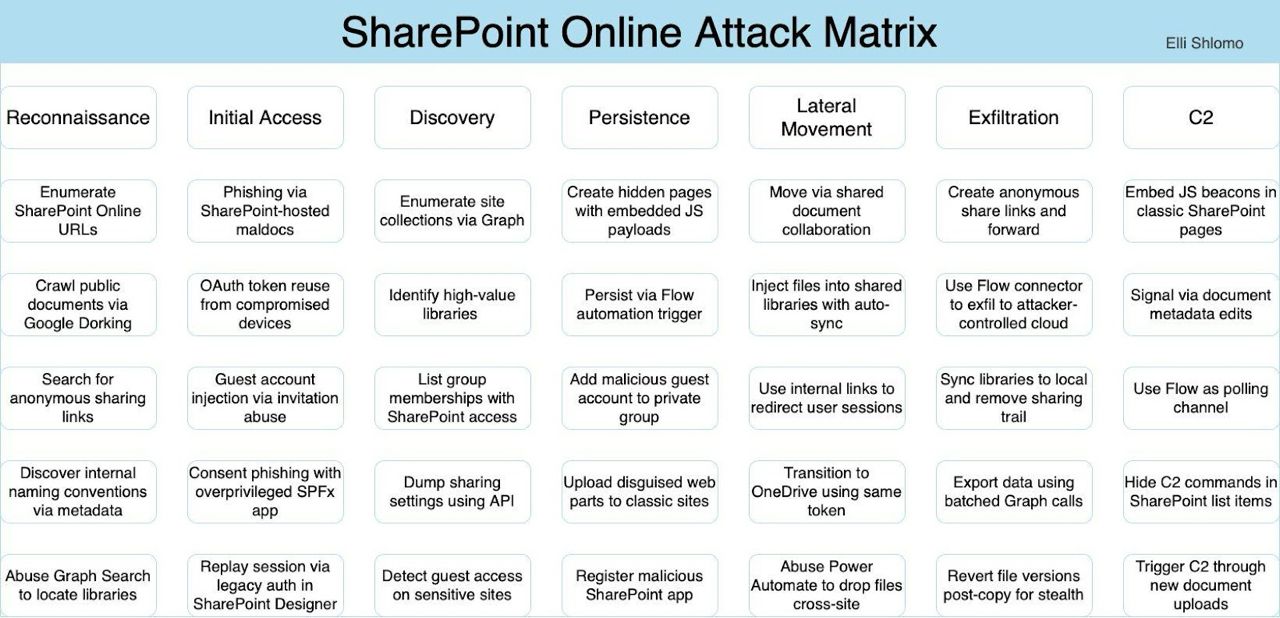
Adversaries systematically compromise SharePoint environments through six distinct phases. Each column represents a critical stage where your security team needs to maintain vigilance, from initial reconnaissance through command and control operations.
Reconnaissance is the foundation of any SharePoint attack. Attackers begin by listing your SharePoint Online URLs, Google Dorking publicly available documents, and searching for anonymous share links revealing sensitive data. They abuse Graph Search capabilities to locate valuable document libraries while discovering internal naming conventions through metadata analysis.
This reconnaissance phase will typically go unnoticed because the attackers utilize legitimate SharePoint features in an effort to gather information. Your security monitoring may completely miss this activity because it appears as normal user traffic. This is precisely why advanced XDR platforms like HawkEye are essential for correlating SharePoint API behaviors with threat intelligence to identify reconnaissance that traditional tools miss.
Most organizations assume their SharePoint environment is secure. After all, it’s Microsoft’s platform with enterprise-grade security, right? Tell that to the companies discovering months-old breaches where attackers used legitimate SharePoint features to exfiltrate terabytes of sensitive data without triggering a single security alert.
Your organization’s SharePoint systems could be under attack right now, and you might not even know it. A recently disclosed Microsoft SharePoint remote code execution (RCE) vulnerability, tracked as CVE-2024-38094, is being exploited to gain initial access to corporate networks, and this is just the tip of the iceberg.
The recent surge in SharePoint Online attacks reveals a disturbing pattern. Cybercriminals have weaponized your trusted productivity platform, turning collaborative features into attack vectors. Understanding how they operate across the attack matrix gives you the defensive advantage you need.
Why SharePoint Becomes an Attack Target.
A SharePoint environment contains everything attackers want: sensitive documents, user credentials, and direct access to a broader Microsoft 365 ecosystem. Unlike traditional network attacks that trigger security alerts, SharePoint attacks blend with normal user activity.
Consider this scenario: an attacker Google Dorks your SharePoint URLs, discovers anonymous share links containing financial reports, and proceeds to use Graph Search to discover additional high-value libraries. Your security products flag legitimate SharePoint API requests, not reconnaissance.
This invisibility makes SharePoint attacks particularly dangerous. DTS Solution’s red team assessments consistently find organizations with robust network security but completely exposed SharePoint environments.
The SharePoint Online Attack Matrix

Adversaries systematically compromise SharePoint environments through six distinct phases. Each column represents a critical stage where your security team needs to maintain vigilance, from initial reconnaissance through command and control operations.
Reconnaissance is the foundation of any SharePoint attack. Attackers begin by listing your SharePoint Online URLs, Google Dorking publicly available documents, and searching for anonymous share links revealing sensitive data. They abuse Graph Search capabilities to locate valuable document libraries while discovering internal naming conventions through metadata analysis.
This reconnaissance phase will typically go unnoticed because the attackers utilize legitimate SharePoint features in an effort to gather information. Your security monitoring may completely miss this activity because it appears as normal user traffic. This is precisely why advanced XDR platforms like HawkEye are essential for correlating SharePoint API behaviors with threat intelligence to identify reconnaissance that traditional tools miss.
The Initial Access Gateway
Initial Access is where the attackers breach your perimeter. The matrix reveals multiple attack vectors that get past standard security controls:
Phishing attacks specifically target SharePoint-hosted malicious documents, relying on user trust in SharePoint. More than 68 million malicious messages were attributed to Microsoft products and brand during 2023, establishing Microsoft as the world’s most abused brand used by cybercriminals. The attacks work because users instinctively trust SharePoint-hosted content.
Reusing OAuth tokens on compromised systems represents one more attack vector. With the attacker stealing authentication tokens, they can access SharePoint without triggering additional authentication hurdles. Guest account injection through invitation abuse gives outside threat actors a means of creating sustained access using supposedly valid credentials.
The consent phishing attack is also significant. Attackers craft over-permissioned SharePoint controls and request excessive permissions. Once the victims approve these malicious controls, attackers gain broad access to SharePoint data and functions.
Discovery and Mapping
After gaining access, attackers systematically map your SharePoint environment using legitimate tools and APIs. They enumerate site collections, identify document libraries containing sensitive data, and analyze group memberships to understand your access hierarchies.
The sharing settings dump reveals misconfigured permissions that expand attack possibilities. Attackers specifically look for guest access on sensitive sites, overprivileged service accounts, and anonymous sharing links that provide broader data access.
Your audit logs might capture these activities, but they appear as normal administrative tasks. Understanding the difference between legitimate discovery and malicious reconnaissance patterns becomes critical when building defensive capabilities that can actually detect these subtle attack behaviors.
Establishing Persistence
Persistence mechanisms ensure attackers maintain access even after security teams detect initial compromise. The matrix shows how attackers create hidden pages embedded with JavaScript payloads that execute whenever users visit SharePoint sites. These malicious pages often masquerade as legitimate content, making detection challenging.
Flow automation triggers provide another persistence method. Attackers configure malicious Power Automate flows that execute when specific conditions are met, such as document uploads or user access events. These flows can exfiltrate data, modify permissions, or execute additional payloads without direct attacker intervention.
Adding malicious guest accounts to private groups creates persistent access channels. Even if primary accounts are discovered and disabled, these secondary accounts remain active, providing continued access to sensitive resources. HawkEye’s multi-event correlation excels at detecting these persistence mechanisms by analyzing relationships between SharePoint customizations and authentication anomalies.
Lateral Movement Tactics
Lateral Movement represents the expansion phase where attackers spread throughout your environment. They leverage shared document collaboration features to move between sites and access additional resources. File injection into shared libraries with auto-sync capabilities spreads malicious content across multiple endpoints.
Internal link redirection attacks manipulate SharePoint’s linking mechanisms to redirect user sessions to attacker-controlled resources. The transition to OneDrive using the same authentication token extends the attack surface beyond SharePoint into personal storage areas.
Power Automate abuse for cross-site file drops demonstrates how attackers weaponize legitimate productivity tools. They create automated workflows that distribute malicious content or exfiltrate data across multiple SharePoint sites and external services.
Data Exfiltration
Exfiltration techniques aim to steal data while avoiding detection. Creating anonymous sharing links offers a covert method for data extraction, allowing attackers to generate links for sensitive files and access them externally without leaving user-specific audit trails.
Flow connectors facilitate exfiltration by syncing SharePoint libraries to attacker-controlled cloud storage, with permissions removed to erase evidence. The batched Graph API calls enable bulk data exports that seem like legitimate administrative actions.
File version reversion is a sophisticated tactic where attackers copy sensitive data and revert files to earlier versions, obscuring access. This technique can bypass basic audit logging since the final file appears unchanged.
Command and Control Operations
The final C2 stage establishes persistent communication channels. Attackers inject JavaScript beacons into standard SharePoint pages, establishing persistent communication channels that execute whenever the user browses such pages. Document metadata manipulation provides covert signaling channels that do not trigger normal security alerts.
Flow-based polling channels establish systems of automated communication that periodically seek new commands or exfiltrate collected data. SharePoint list items can hide C2 commands in seemingly innocuous-looking data structures that merge with commonplace business content.
SharePoint Vulnerability: CVE-2024-38094
CVE-2024-38094 (CVSS score: 7.2), has been described as a deserialization vulnerability impacting SharePoint that could result in remote code execution. Recent incidents demonstrate how attackers leverage these vulnerabilities in coordinated campaigns.
The consequences do not end with data stealing. The attackers can disable security controls, insert persistent backdoors, and breach whole domains with SharePoint being their first point of entry. Organizations often discover these breaches weeks or months after initial compromise, when attackers have already established deep persistence and extracted significant data. This delayed detection highlights why continuous monitoring through HawkEye’s managed CSOC is critical for identifying compromise indicators in real-time.
Conclusion
Knowledge of the SharePoint Online attack matrix enables your security team to implement customized defenses at each stage of an attack. Reconnaissance detection includes the detection of unusual Graph API calls and unusual external access patterns. Prevention of initial access requires successful email security, OAuth application screening, and guest account monitoring.
The discovery phase includes analysis of Graph API usage and SharePoint access logs to search for enumeration behavior. Prevention of persistence includes regular auditing of SharePoint customizations, Flow configurations, and membership in groups.
At DTS Solution, we specialize in both red team offensive operations that simulate these attacks against your environment and blue team defensive strategies that detect and respond to SharePoint threats.
Understanding how attackers attack SharePoint Online is the first step toward building a solid defense plan. The attack matrix outlines the particular ways that enemies utilize the platform, so security teams can align controls with reality.
Use the matrix to discover your blind spots and strengthen your defenses before the attack occurs. It reveals the likely paths of intrusion; your job is to ensure those paths are shut down.
SharePoint Vulnerability: CVE-2024-38094
CVE-2024-38094 (CVSS score: 7.2), has been described as a deserialization vulnerability impacting SharePoint that could result in remote code execution. Recent incidents demonstrate how attackers leverage these vulnerabilities in coordinated campaigns.
The consequences do not end with data stealing. The attackers can disable security controls, insert persistent backdoors, and breach whole domains with SharePoint being their first point of entry. Organizations often discover these breaches weeks or months after initial compromise, when attackers have already established deep persistence and extracted significant data. This delayed detection highlights why continuous monitoring through HawkEye’s managed CSOC is critical for identifying compromise indicators in real-time.
Conclusion
Knowledge of the SharePoint Online attack matrix enables your security team to implement customized defenses at each stage of an attack. Reconnaissance detection includes the detection of unusual Graph API calls and unusual external access patterns. Prevention of initial access requires successful email security, OAuth application screening, and guest account monitoring.
The discovery phase includes analysis of Graph API usage and SharePoint access logs to search for enumeration behavior. Prevention of persistence includes regular auditing of SharePoint customizations, Flow configurations, and membership in groups.
At DTS Solution, we specialize in both red team offensive operations that simulate these attacks against your environment and blue team defensive strategies that detect and respond to SharePoint threats.
Understanding how attackers attack SharePoint Online is the first step toward building a solid defense plan. The attack matrix outlines the particular ways that enemies utilize the platform, so security teams can align controls with reality.
Use the matrix to discover your blind spots and strengthen your defenses before the attack occurs. It reveals the likely paths of intrusion; your job is to ensure those paths are shut down.
See also:

