- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Penetration Testing
These tests are usually conducted outside business hours or when networks and applications are least used, thereby minimising the impact on everyday operations.
PENETRATION TESTING
Our penetration testing engagements identify the threats to your organization, key assets that may be at risk, and the threat agents that may attempt to compromise them. Each engagement is customized to your requirements and may span from breaching a single host to gaining deep network access.
We begin by identifying assignment objectives, scope of work, systems under test and execute a rule of engagement based on the OSSTMM methodology to ensure all parties understand the obligations towards conducting a penetration test. DTS then performs the various attack vectors and scenarios, in many cases getting extremely creative in putting test scenarios together. Throughout the engagement, we provide ongoing status reports, immediate identification and reporting of critical risks, and knowledge transfer to your technical team. At the end of the process, we ensure you have a complete understanding of the exploitable vulnerabilities in your environment as well as recommended remediation strategies from a technical and management perspective.
PENETRATION TESTING
We begin by identifying assignment objectives, scope of work, systems under test and execute a rule of engagement based on the OSSTMM methodology to ensure all parties understand the obligations towards conducting a penetration test. DTS then performs the various attack vectors and scenarios, in many cases getting extremely creative in putting test scenarios together. Throughout the engagement, we provide ongoing status reports, immediate identification and reporting of critical risks, and knowledge transfer to your technical team. At the end of the process, we ensure you have a complete understanding of the exploitable vulnerabilities in your environment as well as recommended remediation strategies from a technical and management perspective.
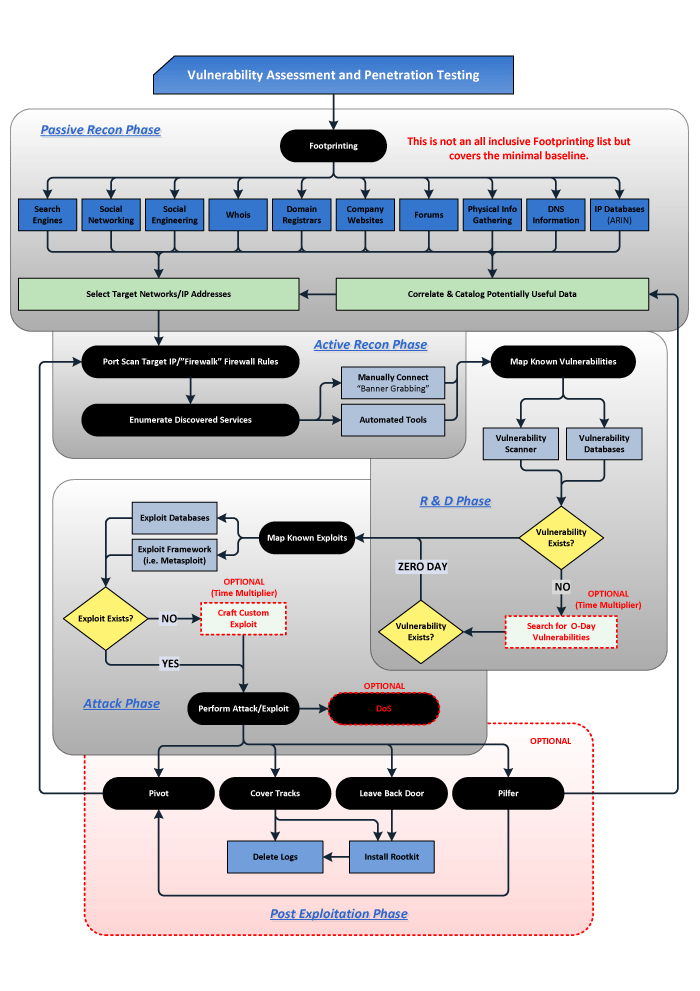
PASSIVE RECON PHASE
Performing passive reconnaissance provides the tester large amounts of knowledge that has already been previously created and captured by various sources without sending any data directly at the target. Some of the sources are part of the infrastructure required by the Internet, such as DNS information, IP databases (ARIN), Domain Registrars, and other information that can be queried by different WHOIS requests.
The results from the passive recon phase would be a knowledge base of potentially useful information about the target’s Internet presence, key employees, IP addresses, domain names, products, or services that would be targeted in further phases.
PASSIVE RECON PHASE
The results from the passive recon phase would be a knowledge base of potentially useful information about the target’s Internet presence, key employees, IP addresses, domain names, products, or services that would be targeted in further phases.
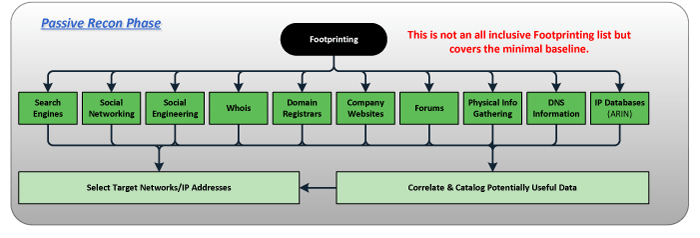
ACTIVE RECON PHASE
Performing passive reconnaissance provides the tester large amounts of knowledge that has already been previously created and captured by various sources without sending any data directly at the target. Some of the sources are part of the infrastructure required by the Internet, such as DNS information, IP databases (ARIN), Domain Registrars, and other information that can be queried by different WHOIS requests.
The output from this phase is a list of hosts detailing the running services, ideally with service version identified.
ACTIVE RECON PHASE
The output from this phase is a list of hosts detailing the running services, ideally with service version identified.
Enumeration
- Network mapping and host discovery
- Service identification, vulnerability scanning, and web application discovery
- Identification of critical systems and network protections
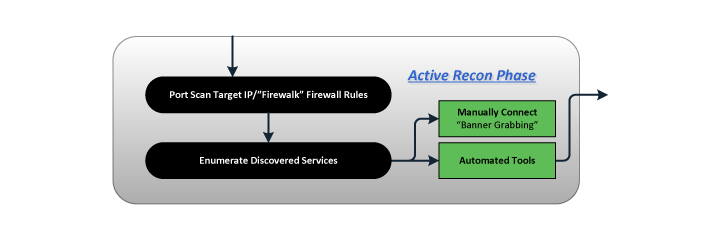
RESEARCH AND DEVELOPMENT
From this phase, a list will be created of hosts with the vulnerabilities specified.
Enumeration
- Network mapping and host discovery
- Service identification, vulnerability scanning, and web application discovery
- Identification of critical systems and network protections
RESEARCH AND DEVELOPMENT
From this phase, a list will be created of hosts with the vulnerabilities specified.
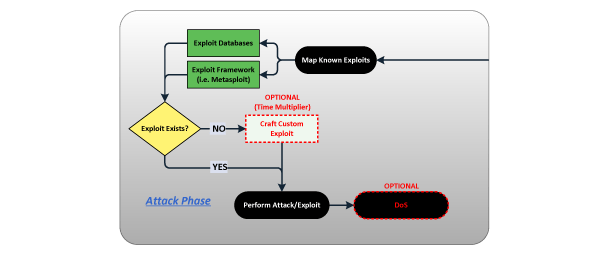
ATTACK PHASE
If exploit code does not exist, it can be created, however this will take longer for a custom exploit than one readily available. Once a tested exploit is available for a specific vulnerability, it will be launched against the target.
- Research exploits and attacks based on enumerated information
- Active exploitation of vulnerable systems and applications
- Manual testing tailored to the deployment and business purpose of the target
ATTACK PHASE
- Research exploits and attacks based on enumerated information
- Active exploitation of vulnerable systems and applications
- Manual testing tailored to the deployment and business purpose of the target
In some cases, for longer-term testing, a back door access will be left or rootkit installed to allow the tester access after the initial exploit. From this access the tester will be able to pilfer or look for sensitive or targeted information relevant to the engagement.
- Escalate privileges and compromise credentials
- Leverage compromised systems to gain new access further into the network
- Attempt to access business-critical systems or information to demonstrate impact
POST-EXPLOITATION PHASE (OPTIONAL)
- Escalate privileges and compromise credentials
- Leverage compromised systems to gain new access further into the network
- Attempt to access business-critical systems or information to demonstrate impact
PENETRATION TEST REPORT
After completion of the testing, the findings will be categorized, risk ratings assigned based on likelihood and impact of exploitation, and mitigations recommended to prevent others from using the same exploits and vulnerabilities. The findings will be contained in a report that will contain summarized data as well as individual data that can be passed to technical remediation teams in order to create a Plan of Action and Milestones (POAM)
PENETRATION TEST REPORT
After completion of the testing, the findings will be categorized, risk ratings assigned based on likelihood and impact of exploitation, and mitigations recommended to prevent others from using the same exploits and vulnerabilities. The findings will be contained in a report that will contain summarized data as well as individual data that can be passed to technical remediation teams in order to create a Plan of Action and Milestones (POAM)
Why Choose DTS as your Penetration Testing Partner
- Extend beyond the tools: Our approach goes beyond the use of automated tools and processes to include deep knowledge of how compromises can occur in government, financial and commercial organizations.
- Follow a time-efficient process: We ensure all assessments are effectively executed within limited engagement windows by prioritizing the testing of critical devices and components and its respective potential vulnerabilities and ensuring we abide by the rule of engagement.
- Deliver deep insight: Our assessments provide you with valuable and actionable insights into discovered vulnerabilities, potential attack paths, business impact of breaches, and remediation steps.
- Help you address the issues: Experienced, skilled tests develop our comprehensive reports, so you can easily understand the actionable information contained within them.
- Stay ahead of the evolving landscape: Our team members undergo extensive training, participate as industry thought leaders, participate in hackathons and CTFs, and have earned industry certifications, including LPT, GCIH, GWAPT, CREST CRT, MCSE, RHCT, OSWP, OSCP, OSCE, CEH, eWPTX, PMP, and CISSP.
Why Choose DTS as your Penetration Testing Partner
More than 300+ clients rely on our comprehensive technical security assessment services because we:
- Extend beyond the tools: Our approach goes beyond the use of automated tools and processes to include deep knowledge of how compromises can occur in government, financial and commercial organizations.
- Follow a time-efficient process: We ensure all assessments are effectively executed within limited engagement windows by prioritizing the testing of critical devices and components and its respective potential vulnerabilities and ensuring we abide by the rule of engagement.
- Deliver deep insight: Our assessments provide you with valuable and actionable insights into discovered vulnerabilities, potential attack paths, business impact of breaches, and remediation steps.
- Help you address the issues: Experienced, skilled tests develop our comprehensive reports, so you can easily understand the actionable information contained within them.
- Stay ahead of the evolving landscape: Our team members undergo extensive training, participate as industry thought leaders, participate in hackathons and CTFs, and have earned industry certifications, including LPT, GCIH, GWAPT, CREST CRT, MCSE, RHCT, OSWP, OSCP, OSCE, CEH, eWPTX, PMP, and CISSP.


Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.