On February 12, 2014, the National Institute of Standards and Technology released version 1.0 of its Cybersecurity Framework (CSF), which details a set of guidelines, best practices, and standards aimed primarily at assisting target organisations in managing and improving their cybersecurity posture. The framework was described as a year-long endeavour by professionals from several fields, including industry, academia, and the government. The document comprised three major elements, which included:
- Core
- Tiers
- Profiles
On February 12, 2014, the National Institute of Standards and Technology released version 1.0 of its Cybersecurity Framework (CSF), which details a set of guidelines, best practices, and standards aimed primarily at assisting target organisations in managing and improving their cybersecurity posture. The framework was described as a year-long endeavour by professionals from several fields, including industry, academia, and the government. The document comprised three major elements, which included:
- Core
- Tiers
- Profiles
The core was divided into five key functions, each of which was further divided into categories and subcategories to help organisations better understand and customise their security posture. This gave organisations a methodical way to evaluate and enhance their cybersecurity risk management procedures.
The functions include:
- Identify
- Protect
- Detect
- Respond
- Recover
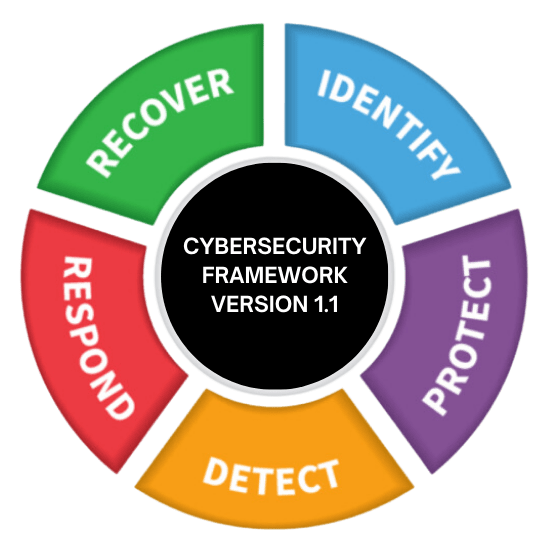
Even though a version 1.1 upgrade was issued in 2018, the core element’s functions remained unchanged. The version included updates for:
- Authentication and identity,
- Self-assessing cybersecurity risk,
- Managing cybersecurity within the supply chain and
- Vulnerability disclosure.
The implementation tiers defined the extent to which an organization’s risk management initiatives ought to meet the framework’s objectives. The non-hierarchical layers were created so that organisations could move through them as their cybersecurity programmes matured. They include:
- Partial
- Risk-Informed
- Repeatable
- Adaptive
Finally, the profiles were designed to assist organisations in moving from their existing degree of cybersecurity competence to a desired and enhanced condition that was at least close to their organisational needs.
NIST referred to version 1.0 as a “living” document since it was subject to upgrades and adjustments to keep up with changing technology, threats, and to integrate lessons learned from its use. Fast forward ten years, to February 26, 2024, and NIST has released the second version of its living CSF document, its first substantial upgrade since 2014.
The core was divided into five key functions, each of which was further divided into categories and subcategories to help organisations better understand and customise their security posture. This gave organisations a methodical way to evaluate and enhance their cybersecurity risk management procedures. The functions include:
- Identify
- Protect
- Detect
- Respond
- Recover
Even though a version 1.1 upgrade was issued in 2018, the core element’s functions remained unchanged. The version included updates for:
- Authentication and identity,
- Self-assessing cybersecurity risk,
- Managing cybersecurity within the supply chain and
- Vulnerability disclosure.

The implementation tiers defined the extent to which an organization’s risk management initiatives ought to meet the framework’s objectives. The non-hierarchical layers were created so that organisations could move through them as their cybersecurity programmes matured. They include:
- Partial
- Risk-Informed
- Repeatable
- Adaptive
Finally, the profiles were designed to assist organisations in moving from their existing degree of cybersecurity competence to a desired and enhanced condition that was at least close to their organisational needs.
NIST referred to version 1.0 as a “living” document since it was subject to upgrades and adjustments to keep up with changing technology, threats, and to integrate lessons learned from its use. Fast forward ten years, to February 26, 2024, and NIST has released the second version of its living CSF document, its first substantial upgrade since 2014.
What’s New?
In response to comments on an early draft that was made public in August 2023, the CSF, in their own words, “now explicitly aims to help ALL organizations”. This signifies that its initial target market, which consisted mostly of businesses running critical systems, including those in finance, energy, healthcare, and other industries, has grown. This updated version now includes provisions for small, medium, large, and major organisations. Everyone, irrespective of level of capability in cybersecurity.
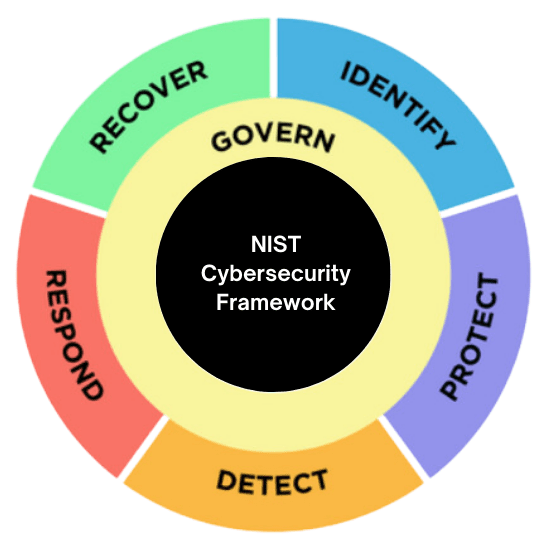
In addition, a new and refined Reference Tool was introduced. The tool is projected to improve user experience by making it easier to explore, search, and export data and details from the framework’s core guidelines in both human and machine-readable formats. The CSF 2.0 provides a searchable collection of informative references that demonstrate how their present actions relate to the CSF. The catalogue also allows users to cross-reference the CSF’s guidelines to over 50 other cybersecurity documents, including NIST publications such as SP 800-53 Rev. 5.
Organisations can also use the Cybersecurity and Privacy Reference Tool (CPRT), which offers an interconnected, browsable, and downloadable set of NIST guideline documents that contextualise various NIST resources, including the CSF, with other widely used resources. The CPRT also provides methods for communicating these ideas to both technical experts and C-level, ensuring that all levels of an organisation remain synchronised.
The recent changes to the NIST Cybersecurity Framework (CSF) underscore NIST’s continuous commitment to ensuring that the framework is not only effective but also highly useable across a variety of sectors. By constantly developing and upgrading the framework, NIST expects to equip organisations with a robust yet adaptable tool for effectively managing cybersecurity risk. With the introduction of these revisions just hours ago, it can be deduced that NIST is committed to keeping up with emerging cyber threats and technological advancements, hence increasing the CSF’s relevance and applicability in today’s quickly changing cybersecurity arena.
Looking ahead, we may expect widespread adoption of the updated CSF as organisations attempt to strengthen their cybersecurity defences and resilience. The release of the updated CSF marks a significant milestone in advancing cybersecurity readiness especially with its new inclusivity.
What’s New?
In response to comments on an early draft that was made public in August 2023, the CSF, in their own words, “now explicitly aims to help ALL organizations”. This signifies that its initial target market, which consisted mostly of businesses running critical systems, including those in finance, energy, healthcare, and other industries, has grown. This updated version now includes provisions for small, medium, large, and major organisations. Everyone, irrespective of level of capability in cybersecurity.
A new core element, the “Govern” element was added while the CSF’s core guidance was expanded. New relevant resources were also created to assist users in their unique way to maximise the framework’s capabilities. These resources are intended to provide customised pathways into the CSF for various audiences, as well as to make the framework more practical.

In addition, a new and refined Reference Tool was introduced. The tool is projected to improve user experience by making it easier to explore, search, and export data and details from the framework’s core guidelines in both human and machine-readable formats. The CSF 2.0 provides a searchable collection of informative references that demonstrate how their present actions relate to the CSF. The catalogue also allows users to cross-reference the CSF’s guidelines to over 50 other cybersecurity documents, including NIST publications such as SP 800-53 Rev. 5.
Organisations can also use the Cybersecurity and Privacy Reference Tool (CPRT), which offers an interconnected, browsable, and downloadable set of NIST guideline documents that contextualise various NIST resources, including the CSF, with other widely used resources. The CPRT also provides methods for communicating these ideas to both technical experts and C-level, ensuring that all levels of an organisation remain synchronised.
The recent changes to the NIST Cybersecurity Framework (CSF) underscore NIST’s continuous commitment to ensuring that the framework is not only effective but also highly useable across a variety of sectors. By constantly developing and upgrading the framework, NIST expects to equip organisations with a robust yet adaptable tool for effectively managing cybersecurity risk. With the introduction of these revisions just hours ago, it can be deduced that NIST is committed to keeping up with emerging cyber threats and technological advancements, hence increasing the CSF’s relevance and applicability in today’s quickly changing cybersecurity arena.
Looking ahead, we may expect widespread adoption of the updated CSF as organisations attempt to strengthen their cybersecurity defences and resilience. The release of the updated CSF marks a significant milestone in advancing cybersecurity readiness especially with its new inclusivity.
See also:

