Background
Multi-Factor Authentication adds an additional level of protection for user accounts. MFA should stop threat actors from accessing an account if they are able to get the password and login credentials for the account through phishing or other means. It provides an additional stage in the process to verify the true identity of the user seeking to log in as a secondary level of protection in addition to passwords. Many MFA options include SMS, One Time Passwords (OTP), and push notifications from an app. With the increasing adoption of MFA, multi-factor authentication (MFA) fatigue attacks have become more prevalent.
Background
Multi-Factor Authentication adds an additional level of protection for user accounts. MFA should stop threat actors from accessing an account if they are able to get the password and login credentials for the account through phishing or other means. It provides an additional stage in the process to verify the true identity of the user seeking to log in as a secondary level of protection in addition to passwords. Many MFA options include SMS, One Time Passwords (OTP), and push notifications from an app. With the increasing adoption of MFA, multi-factor authentication (MFA) fatigue attacks have become more prevalent.
MFA Fatigue Attack
Attackers utilize the method known as (MFA) fatigue, also known as MFA Prompt Spamming or MFA bombing, to bombard a user’s authentication app with push notifications in the hopes that they will accept, giving the attacker access to an account or device. This attack is extremely successful not because of the technology used, but rather because it goes after the MFA human aspect. Many MFA users are not accustomed to this kind of attack and might not be aware that they are approving a false notification. Others merely want it gone and are simply unaware of what they are doing because they often approve notifications with identical requests. Because of the notification overload, they are unable to recognize the danger.
MFA Fatigue Attack
Attackers utilize the method known as (MFA) fatigue, also known as MFA Prompt Spamming or MFA bombing, to bombard a user’s authentication app with push notifications in the hopes that they will accept, giving the attacker access to an account or device. This attack is extremely successful not because of the technology used, but rather because it goes after the MFA human aspect. Many MFA users are not accustomed to this kind of attack and might not be aware that they are approving a false notification. Others merely want it gone and are simply unaware of what they are doing because they often approve notifications with identical requests. Because of the notification overload, they are unable to recognize the danger.
Working of MFA Fatigue Attack
MFA fatigue attacks begin by obtaining a user’s email address and password, which serve as their default login information. Unfortunately, it’s much simpler: User credentials can be stolen by cybercriminals using a number of different techniques. To see if someone has used a password across several applications, they can utilize passwords that have been exposed in earlier thefts. They can start phishing attempts to deceive people into voluntarily providing their information. They can even attempt randomly guessing well-known passwords until they find a successful combination.
The second element of an MFA fatigue attack is to continually spam authentication prompts in the hopes that the person on the other end will either make a mistake or give in under pressure after the attacker has successfully completed the initial login step by inputting the proper username and password. MFA fatigue attacks cannot force the account holder to confirm the login, hence they are not always successful. However, MFA fatigue is a relatively simple method that can be automated and scaled out quite cheaply, therefore attackers frequently run several of these campaigns at once.
Working of MFA Fatigue Attack
MFA fatigue attacks begin by obtaining a user’s email address and password, which serve as their default login information. Unfortunately, it’s much simpler: User credentials can be stolen by cybercriminals using a number of different techniques. To see if someone has used a password across several applications, they can utilize passwords that have been exposed in earlier thefts. They can start phishing attempts to deceive people into voluntarily providing their information. They can even attempt randomly guessing well-known passwords until they find a successful combination.
The second element of an MFA fatigue attack is to continually spam authentication prompts in the hopes that the person on the other end will either make a mistake or give in under pressure after the attacker has successfully completed the initial login step by inputting the proper username and password. MFA fatigue attacks cannot force the account holder to confirm the login, hence they are not always successful. However, MFA fatigue is a relatively simple method that can be automated and scaled out quite cheaply, therefore attackers frequently run several of these campaigns at once.
Recent Campaigns
In the most recent attacks against Cisco and Uber, this technique was used. By incorporating social engineering into the attack on Uber, the attacker boosted their chances of success. They got in touch with the victim via WhatsApp and demanded that they authorize the login so that the MFA notifications would stop, while posing as an IT staff member. You can read more about the Uber breach in our detailed article – Recent Uber Breach and Lessons Learnt
Recent Campaigns
In the most recent attacks against Cisco and Uber, this technique was used. By incorporating social engineering into the attack on Uber, the attacker boosted their chances of success. They got in touch with the victim via WhatsApp and demanded that they authorize the login so that the MFA notifications would stop, while posing as an IT staff member. You can read more about the Uber breach in our detailed article – Recent Uber Breach and Lessons Learnt
In the case of Cisco, an employee became a victim of an attack after receiving just one of a flood of false push notifications and voice phishing efforts, which resulted in a network breach and an attempt to extort the business. The Yanluowang ransomware gang has been blamed for the Cisco network compromise, however, the organization was fortunate in that ransomware was never really used. An employee had synced their internal network credentials with Google Chrome, which allowed the attacker access. The attacker then used voice phishing to pretend to be calling from various tech businesses in order to access the Google account. The employee eventually succumbed to MFA fatigue as the attacker constantly bombarded them with push requests to allow a login despite this warning of suspicious activity.
Detecting MFA Fatigue Attacks
- Check the application logs for unusual occurrences, such as persistent MFA failures that might point to a breach of the user’s primary credentials.
- Keep an eye out for suspicious activity in the 2FA/MFA application logs, such as frequent login attempts made with valid credentials.
- Keep an eye out for suspicious activity in the 2FA/MFA application logs, such as unexpected login attempt source locations, inconsistent login attempt locations, and smart devices granting 2FA/MFA request prompts.
Detecting MFA Fatigue Attacks
- Check the application logs for unusual occurrences, such as persistent MFA failures that might point to a breach of the user’s primary credentials.
- Keep an eye out for suspicious activity in the 2FA/MFA application logs, such as frequent login attempts made with valid credentials.
- Keep an eye out for suspicious activity in the 2FA/MFA application logs, such as unexpected login attempt source locations, inconsistent login attempt locations, and smart devices granting 2FA/MFA request prompts.
Mitigating MFA Fatigue Attacks
- Enable account limits to stop login attempts from being made from questionable places or when the source of the login attempts does not coincide with the location of the 2FA/MFA smart device. This will prohibit the subsequent 2FA/MFA service requests.
- Replace straightforward push or one-click 2FA/MFA options with more secure 2FA/MFA techniques. For instance, using various out-of-band 2FA/MFA technologies or requiring users to enter a one-time code from the login screen into the 2FA/MFA application may be more secure.
- Users should be trained to only accept 2FA/MFA requests from login attempts they initiated, to check the location of the login attempt’s source, to report suspicious or unwanted prompts, and to do all of the above.
- Enable push notification that not only asks users to enter a number into the authenticator app but to add context – such as the sign-in location. This feature was recently introduced by Microsoft Authenticator.
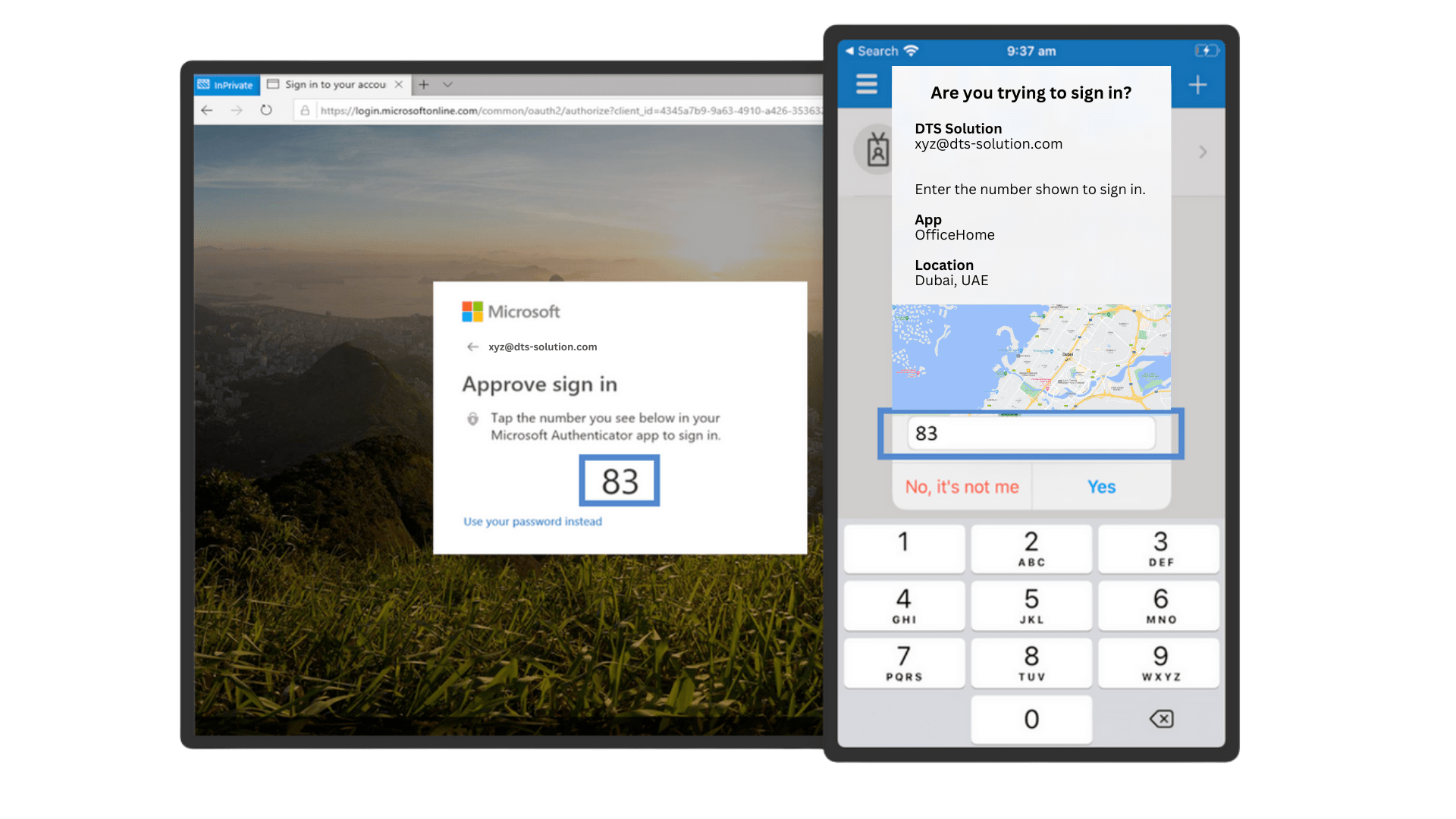
Mitigating MFA Fatigue Attacks
- Enable account limits to stop login attempts from being made from questionable places or when the source of the login attempts does not coincide with the location of the 2FA/MFA smart device. This will prohibit the subsequent 2FA/MFA service requests.
- Replace straightforward push or one-click 2FA/MFA options with more secure 2FA/MFA techniques. For instance, using various out-of-band 2FA/MFA technologies or requiring users to enter a one-time code from the login screen into the 2FA/MFA application may be more secure.
- Users should be trained to only accept 2FA/MFA requests from login attempts they initiated, to check the location of the login attempt’s source, to report suspicious or unwanted prompts, and to do all of the above.
- Enable push notification that not only asks users to enter a number into the authenticator app but to add context – such as the sign-in location. This feature was recently introduced by Microsoft Authenticator.

See also:

