The global shift to remote work has created unprecedented opportunities for talent acquisition across borders. However, this expansion has also opened new attack vectors for sophisticated state actors. North Korea’s Democratic People’s Republic of Korea (DPRK) has transformed remote employment into a weapon of economic warfare, orchestrating one of the most elaborate insider threat campaigns in modern cybersecurity.
The Anatomy of Economic Espionage
The DPRK’s remote IT worker scheme represents a masterclass in long-term strategic deception. Rather than traditional smash-and-grab cryptocurrency raids, this operation focuses on sustainable income generation through legitimate employment channels. The scheme operates through a carefully coordinated network spanning multiple countries, with each participant playing a specific role in the broader deception.
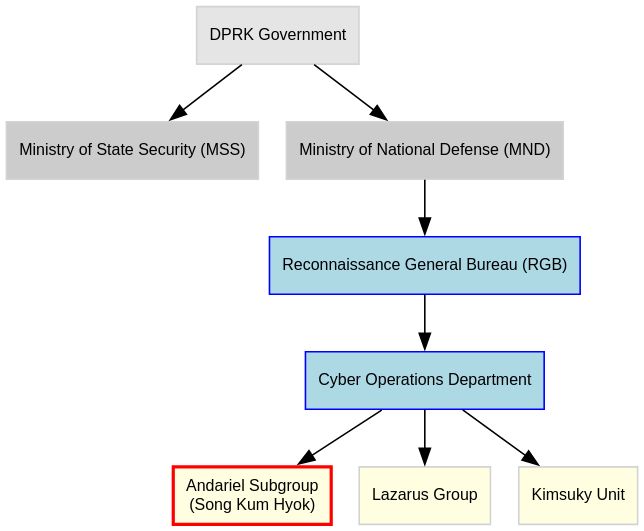
At the operational core stands Song Kum Hyok, a senior officer within the Andariel subgroup of North Korea’s Reconnaissance General Bureau (RGB). Under his coordination, the regime has developed a scalable model that transforms stolen identities into legitimate-appearing job applications. These operations generate millions in revenue annually while providing unprecedented access to sensitive corporate infrastructure.
Identity Theft as Infrastructure
The foundation of this scheme rests on comprehensive identity packages complete with Social Security numbers, background checks, and even Green Card documentation. These materials, sourced from data breaches and underground markets, create convincing personas like “Joshua Palmer” and “Sandy Nguyen” – complete with professional GitHub profiles and employment histories.
The sophistication extends beyond simple document forgery. AI-generated content enhances resumes and LinkedIn profiles, while operatives maintain consistent communication patterns that align with their assumed identities. This attention to detail allows them to pass through automated verification systems and cursory HR screenings without raising suspicion.
The American Connection: Laptop Farms and Shell Companies
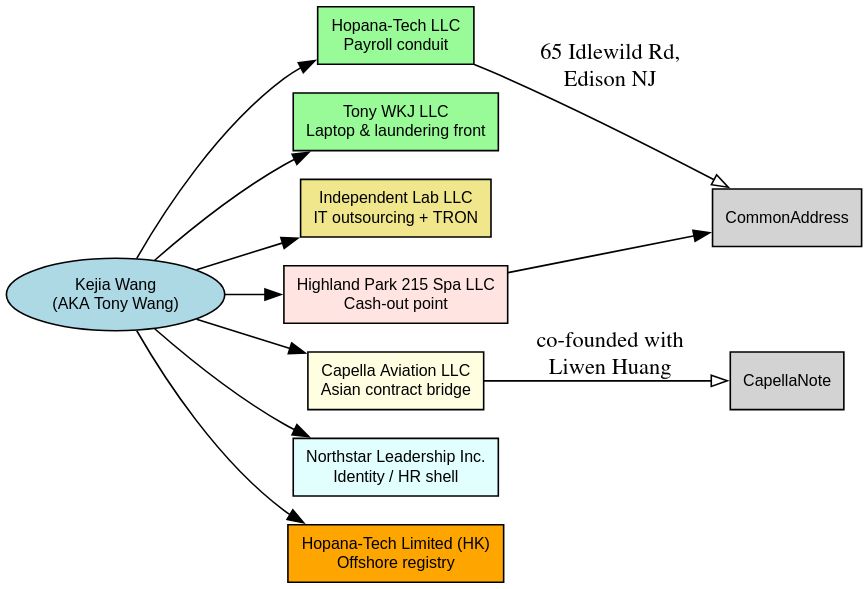
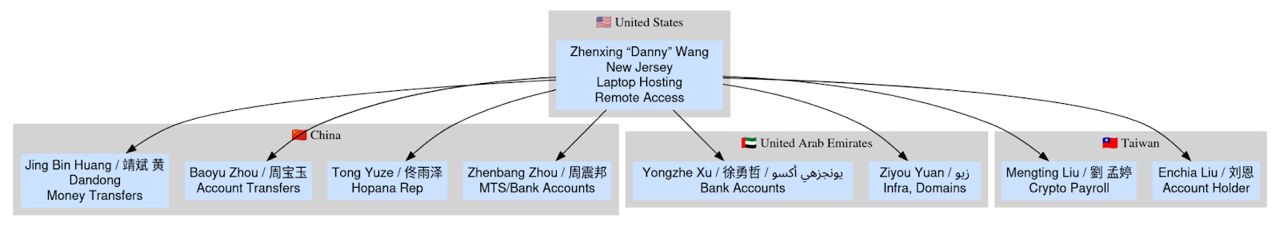
The scheme’s U.S. operations centered around facilitators like Kejia Wang, operating from Edison, New Jersey. Wang established a network of shell companies including Hopana-Tech LLC, Tony WKJ LLC, and Independent Lab LLC, each serving distinct functions in the laundering ecosystem. These entities processed salary payments, managed laptop deployments, and provided seemingly legitimate business addresses for employment verification.
The “laptop farm” concept represents a particularly ingenious aspect of the operation. Companies would ship work equipment to U.S. addresses, believing they were sending devices to domestic contractors. Instead, these laptops were configured with KVM switches and remote access software, allowing DPRK operatives to work as if they were physically located in America.
Recent DOJ indictments revealed that Christina Chapman in Arizona operated similar laptop farms, maintaining devices for continuous remote access while ensuring all network traffic appeared to originate from U.S. soil. This geographic spoofing proved crucial for bypassing basic security controls and maintaining operational security.
Platform Evolution and Global Expansion
As major freelancing platforms like Upwork and Fiverr implemented stricter verification procedures, DPRK operatives adapted by targeting less-regulated regional platforms, particularly in the Middle East and North Africa. This strategic pivot demonstrated the regime’s operational flexibility and commitment to maintaining revenue streams despite increased scrutiny.
The expansion strategy included synthetic voice technology for video interviews, AI-generated profile images, and automated deployment of identity documents. These technological enhancements allowed operatives to maintain their facades even under more rigorous vetting processes.
Financial Infrastructure and Money Laundering
The monetary flow operated through a sophisticated three-phase pipeline. Initial payments from unsuspecting companies were directed to GitHub-linked wallet addresses or shell company accounts. Smart contracts then automatically fragmented these funds across multiple cryptocurrency wallets, obscuring transaction trails and complicating forensic analysis.
The final phase involved over-the-counter crypto brokers in Russia, the UAE, and Hong Kong, who specialized in converting large cryptocurrency volumes into fiat currency while avoiding compliance triggers. This distributed approach allowed the DPRK to convert fraudulent earnings into usable capital for weapons development programs.
The global shift to remote work has created unprecedented opportunities for talent acquisition across borders. However, this expansion has also opened new attack vectors for sophisticated state actors. North Korea’s Democratic People’s Republic of Korea (DPRK) has transformed remote employment into a weapon of economic warfare, orchestrating one of the most elaborate insider threat campaigns in modern cybersecurity.
The Anatomy of Economic Espionage
The DPRK’s remote IT worker scheme represents a masterclass in long-term strategic deception. Rather than traditional smash-and-grab cryptocurrency raids, this operation focuses on sustainable income generation through legitimate employment channels. The scheme operates through a carefully coordinated network spanning multiple countries, with each participant playing a specific role in the broader deception.
At the operational core stands Song Kum Hyok, a senior officer within the Andariel subgroup of North Korea’s Reconnaissance General Bureau (RGB). Under his coordination, the regime has developed a scalable model that transforms stolen identities into legitimate-appearing job applications. These operations generate millions in revenue annually while providing unprecedented access to sensitive corporate infrastructure.
Identity Theft as Infrastructure
The foundation of this scheme rests on comprehensive identity packages complete with Social Security numbers, background checks, and even Green Card documentation. These materials, sourced from data breaches and underground markets, create convincing personas like “Joshua Palmer” and “Sandy Nguyen” – complete with professional GitHub profiles and employment histories.
The sophistication extends beyond simple document forgery. AI-generated content enhances resumes and LinkedIn profiles, while operatives maintain consistent communication patterns that align with their assumed identities. This attention to detail allows them to pass through automated verification systems and cursory HR screenings without raising suspicion.
The American Connection: Laptop Farms and Shell Companies
The scheme’s U.S. operations centered around facilitators like Kejia Wang, operating from Edison, New Jersey. Wang established a network of shell companies including Hopana-Tech LLC, Tony WKJ LLC, and Independent Lab LLC, each serving distinct functions in the laundering ecosystem. These entities processed salary payments, managed laptop deployments, and provided seemingly legitimate business addresses for employment verification.
The “laptop farm” concept represents a particularly ingenious aspect of the operation. Companies would ship work equipment to U.S. addresses, believing they were sending devices to domestic contractors. Instead, these laptops were configured with KVM switches and remote access software, allowing DPRK operatives to work as if they were physically located in America.
Recent DOJ indictments revealed that Christina Chapman in Arizona operated similar laptop farms, maintaining devices for continuous remote access while ensuring all network traffic appeared to originate from U.S. soil. This geographic spoofing proved crucial for bypassing basic security controls and maintaining operational security.
Platform Evolution and Global Expansion
As major freelancing platforms like Upwork and Fiverr implemented stricter verification procedures, DPRK operatives adapted by targeting less-regulated regional platforms, particularly in the Middle East and North Africa. This strategic pivot demonstrated the regime’s operational flexibility and commitment to maintaining revenue streams despite increased scrutiny.
The expansion strategy included synthetic voice technology for video interviews, AI-generated profile images, and automated deployment of identity documents. These technological enhancements allowed operatives to maintain their facades even under more rigorous vetting processes.
Financial Infrastructure and Money Laundering
The monetary flow operated through a sophisticated three-phase pipeline. Initial payments from unsuspecting companies were directed to GitHub-linked wallet addresses or shell company accounts. Smart contracts then automatically fragmented these funds across multiple cryptocurrency wallets, obscuring transaction trails and complicating forensic analysis.
The final phase involved over-the-counter crypto brokers in Russia, the UAE, and Hong Kong, who specialized in converting large cryptocurrency volumes into fiat currency while avoiding compliance triggers. This distributed approach allowed the DPRK to convert fraudulent earnings into usable capital for weapons development programs.
The Insider Threat Reality
Once embedded within target organizations, these operatives gained access to critical infrastructure, including GitHub repositories, CI/CD pipelines, and cloud configuration files. This privileged access created opportunities for intellectual property theft, backdoor insertion, and long-term surveillance operations.
While official disclosures haven’t confirmed specific instances of malicious code deployment, the potential for strategic espionage through these insider positions represents a significant national security concern. The operatives’ access to production environments, encryption logic, and proprietary APIs created numerous vectors for both immediate exploitation and future attack preparation.
Corporate Vulnerabilities Exposed
The success of this scheme highlighted fundamental weaknesses in corporate hiring and security practices. Many organizations relied heavily on automated background check platforms without implementing additional verification measures. The absence of robust identity verification, combined with inadequate access monitoring, created an environment where foreign operatives could operate undetected for extended periods.
Key vulnerabilities included:
- Over-reliance on third-party background verification services
- Insufficient geographic and behavioral analysis during onboarding
- Lack of continuous access monitoring for remote employees
- Inadequate endpoint security for contractor-managed devices
- Weak identity correlation across multiple employment platforms
Building Defensive Capabilities
Organizations must implement comprehensive security measures that address both the technical and human elements of this threat. Effective defense requires a multi-layered approach spanning HR processes, technical controls, and ongoing monitoring capabilities.
Enhanced Identity Verification: Companies should implement biometric verification, conduct live video interviews, and cross-reference employment histories across multiple databases. These measures help identify inconsistencies that may indicate fraudulent identities.
Zero-Trust Access Controls: Every remote worker should operate within a zero-trust security model, where access privileges are continuously evaluated based on device health, location, and behavioral patterns. This approach minimizes the impact of compromised identities.
Comprehensive Monitoring: Organizations need real-time visibility into who accesses which systems, when, and from where. Behavioral anomaly detection can identify unusual access patterns that may indicate malicious activity.
Incident Response Planning: Organizations should develop specific response protocols for suspected insider threats, including immediate access revocation, forensic analysis capabilities, and coordination with law enforcement agencies.
The Regulatory Response
The scale and sophistication of this scheme prompted significant regulatory action. U.S. authorities seized $7.7 million in cryptocurrency assets connected to the operation in June 2025, targeting wallets tied to known DPRK aliases. However, this represents only a fraction of the estimated $17 million directly attributed to the scheme, with broader DPRK cryptocurrency operations generating over $1.6 billion globally.
The regulatory response extends beyond financial seizures to include enhanced screening requirements for remote workers and stricter verification protocols for freelancing platforms. These measures aim to close the regulatory gaps that enabled the scheme’s initial success.
Conclusion
The DPRK’s remote worker scheme demonstrates the regime’s ability to adapt traditional espionage techniques to modern employment practices. This evolution from external cyberattacks to insider threats represents a fundamental shift in nation-state operations, requiring corresponding changes in defensive strategies.
Organizations must immediately assess their remote worker verification procedures and implement enhanced security controls. This includes comprehensive identity verification, zero-trust access models, continuous monitoring, and robust incident response capabilities.
At DTS, we understand the evolving tactics of nation-state actors and help organizations build resilient defenses against sophisticated infiltration attempts. If your organization needs expert assistance in developing these capabilities, contact us for specialized consulting services focused on sanctions compliance and remote worker verification.
The DPRK’s remote worker playbook serves as a stark reminder that modern cybersecurity must address human elements as rigorously as technical vulnerabilities. Organizations that adapt quickly will be best positioned to harness the benefits of global talent while protecting against sophisticated state-sponsored threats.
The Insider Threat Reality
Once embedded within target organizations, these operatives gained access to critical infrastructure, including GitHub repositories, CI/CD pipelines, and cloud configuration files. This privileged access created opportunities for intellectual property theft, backdoor insertion, and long-term surveillance operations.
While official disclosures haven’t confirmed specific instances of malicious code deployment, the potential for strategic espionage through these insider positions represents a significant national security concern. The operatives’ access to production environments, encryption logic, and proprietary APIs created numerous vectors for both immediate exploitation and future attack preparation.
Corporate Vulnerabilities Exposed
The success of this scheme highlighted fundamental weaknesses in corporate hiring and security practices. Many organizations relied heavily on automated background check platforms without implementing additional verification measures. The absence of robust identity verification, combined with inadequate access monitoring, created an environment where foreign operatives could operate undetected for extended periods.
Key vulnerabilities included:
- Over-reliance on third-party background verification services
- Insufficient geographic and behavioral analysis during onboarding
- Lack of continuous access monitoring for remote employees
- Inadequate endpoint security for contractor-managed devices
- Weak identity correlation across multiple employment platforms
Building Defensive Capabilities
Organizations must implement comprehensive security measures that address both the technical and human elements of this threat. Effective defense requires a multi-layered approach spanning HR processes, technical controls, and ongoing monitoring capabilities.
Enhanced Identity Verification: Companies should implement biometric verification, conduct live video interviews, and cross-reference employment histories across multiple databases. These measures help identify inconsistencies that may indicate fraudulent identities.
Zero-Trust Access Controls: Every remote worker should operate within a zero-trust security model, where access privileges are continuously evaluated based on device health, location, and behavioral patterns. This approach minimizes the impact of compromised identities.
Comprehensive Monitoring: Organizations need real-time visibility into who accesses which systems, when, and from where. Behavioral anomaly detection can identify unusual access patterns that may indicate malicious activity.
Incident Response Planning: Organizations should develop specific response protocols for suspected insider threats, including immediate access revocation, forensic analysis capabilities, and coordination with law enforcement agencies.
The Regulatory Response
The scale and sophistication of this scheme prompted significant regulatory action. U.S. authorities seized $7.7 million in cryptocurrency assets connected to the operation in June 2025, targeting wallets tied to known DPRK aliases. However, this represents only a fraction of the estimated $17 million directly attributed to the scheme, with broader DPRK cryptocurrency operations generating over $1.6 billion globally.
The regulatory response extends beyond financial seizures to include enhanced screening requirements for remote workers and stricter verification protocols for freelancing platforms. These measures aim to close the regulatory gaps that enabled the scheme’s initial success.
Conclusion
The DPRK’s remote worker scheme demonstrates the regime’s ability to adapt traditional espionage techniques to modern employment practices. This evolution from external cyberattacks to insider threats represents a fundamental shift in nation-state operations, requiring corresponding changes in defensive strategies.
Organizations must immediately assess their remote worker verification procedures and implement enhanced security controls. This includes comprehensive identity verification, zero-trust access models, continuous monitoring, and robust incident response capabilities.
At DTS, we understand the evolving tactics of nation-state actors and help organizations build resilient defenses against sophisticated infiltration attempts. If your organization needs expert assistance in developing these capabilities, contact us for specialized consulting services focused on sanctions compliance and remote worker verification.
The DPRK’s remote worker playbook serves as a stark reminder that modern cybersecurity must address human elements as rigorously as technical vulnerabilities. Organizations that adapt quickly will be best positioned to harness the benefits of global talent while protecting against sophisticated state-sponsored threats.
See also: