Digital twins are one of the most promising technologies in the era of Industry 4.0. They are virtual representations of physical objects, systems, or processes. A good example is software like Google Maps, which models the earth’s surface digitally. By creating a digital twin, one can collect, analyze, and visualize data from the real-world counterpart and test different scenarios and outcomes without affecting the actual asset or system.
While they provide many benefits, digital twins also experience significant challenges and threats in terms of cybersecurity. As digital twins rely on constant data exchange between the physical and virtual worlds, they are vulnerable to cyberattacks that could compromise their functionality, integrity, or confidentiality. Given the increasing reliance on digital twins across industries, it is imperative to ensure robust cybersecurity measures are in place to protect these virtual replicas from potential threats.
Let’s explore the cybersecurity threats and risks for digital twins and propose some solutions and best practices to keep them safe.
Digital twins are one of the most promising technologies in the era of Industry 4.0. They are virtual representations of physical objects, systems, or processes. A good example is software like Google Maps, which models the earth’s surface digitally. By creating a digital twin, one can collect, analyze, and visualize data from the real-world counterpart and test different scenarios and outcomes without affecting the actual asset or system.
While they provide many benefits, digital twins also experience significant challenges and threats in terms of cybersecurity. As digital twins rely on constant data exchange between the physical and virtual worlds, they are vulnerable to cyberattacks that could compromise their functionality, integrity, or confidentiality. Given the increasing reliance on digital twins across industries, it is imperative to ensure robust cybersecurity measures are in place to protect these virtual replicas from potential threats.
Let’s explore the cybersecurity threats and risks for digital twins and propose some solutions and best practices to keep them safe.
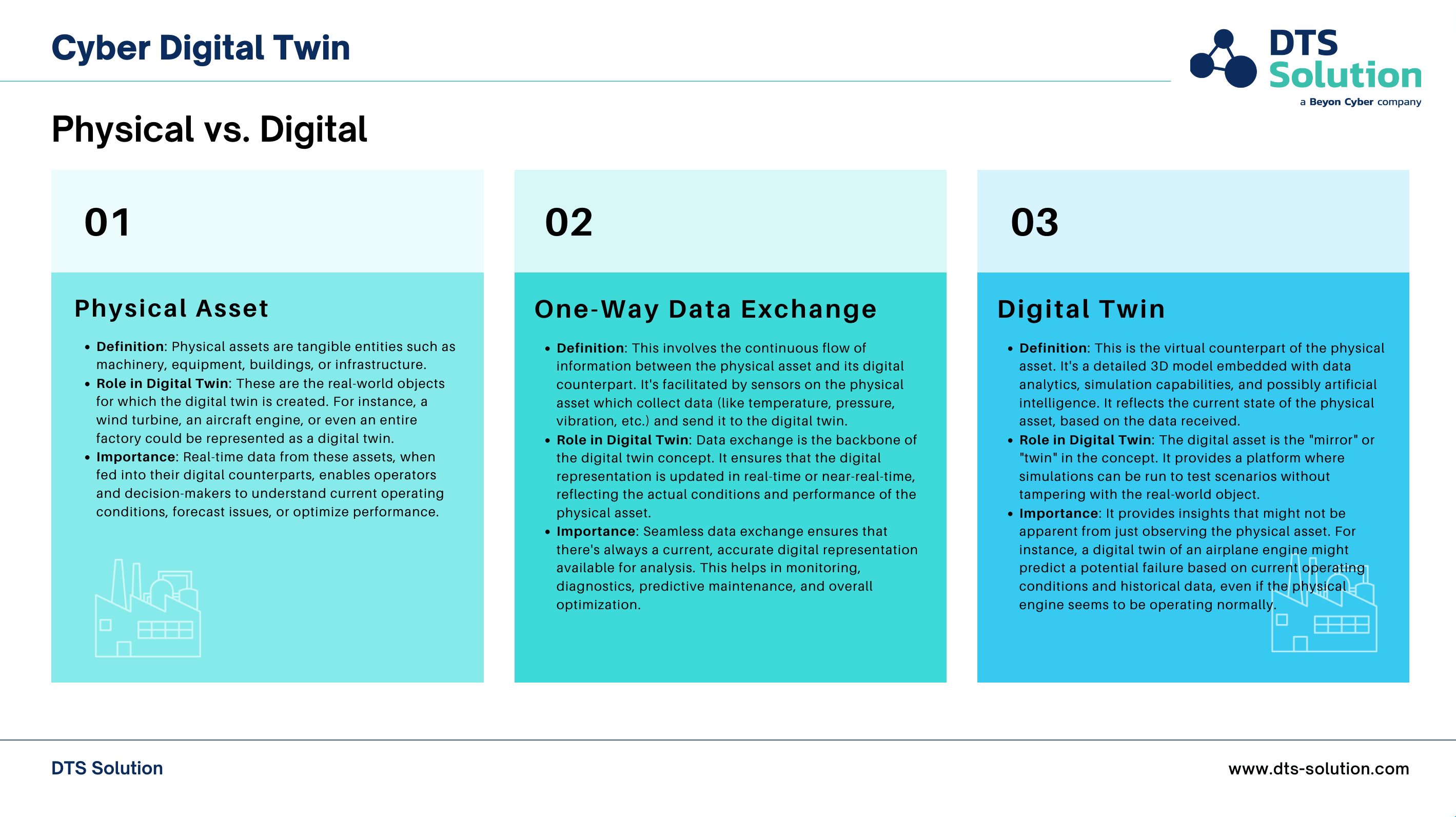
Understanding Digital Twin
Digital twins are virtual replicas of physical objects, processes, or systems that are created using data derived from IoT/IIoT/xIoT or OT sensor technologies. These virtual replicas enable real-time monitoring, analysis, and optimization of their physical counterparts.
Digital twins have many applications and benefits across all economic sectors. It can help to improve product design and quality, reduce operational costs and risks, enhance customer experience and satisfaction, and enable innovation and sustainability. Some of the use cases of this technology include:
- Creating a digital twin of a jet engine to optimize its performance and maintenance.
- Developing a digital twin of a factory to monitor its operations and energy consumption.
- Simulating a digital twin of a smart city to manage its traffic and infrastructure.
Understanding Digital Twin
Digital twins are virtual replicas of physical objects, processes, or systems that are created using data derived from IoT/IIoT/xIoT or OT sensor technologies. These virtual replicas enable real-time monitoring, analysis, and optimization of their physical counterparts.
Digital twins have many applications and benefits across all economic sectors. It can help to improve product design and quality, reduce operational costs and risks, enhance customer experience and satisfaction, and enable innovation and sustainability. Some of the use cases of this technology include:
- Creating a digital twin of a jet engine to optimize its performance and maintenance.
- Developing a digital twin of a factory to monitor its operations and energy consumption.
- Simulating a digital twin of a smart city to manage its traffic and infrastructure.

Cybersecurity Challenges Faced by Digital Twins
Digital twins are exposed to various forms of cyberattacks that could target their data, communication, or functionality.
One of the primary challenges facing digital twins is the generally poor state of security on IoT/IioT/xIoT or OT devices used as sensors within digital twin setups. These devices are often shipped with known default usernames and passwords, making them vulnerable to exploitation by malicious actors. Additionally, there is often a lag in cybersecurity expertise regarding digital twins. This knowledge gap can result in insufficient security measures being implemented, leaving digital twins exposed to potential threats.
Some other common types of cyberattacks that could affect it are:
- Data theft: When an unauthorized party accesses, copies, or exfiltrates the data from the digital twin or the physical asset or system, it could result in loss of intellectual property, breach of privacy, or competitive disadvantage. For example, a hacker could steal the design specifications or performance data of a digital twin of a new product and sell it to a rival company.
- Data manipulation: Unauthorized parties can manipulate, alter, delete, or inject the data from or to the digital twin or the physical asset or system. This could result in false or inaccurate information, malfunction or damage, or misguided decisions.
- Denial of service: A common cybersecurity challenge digital twins face is unexpected disruptions, blocks, or overwhelms in the communication or functionality of the digital twin or the physical asset or system through the data exchange layer.
Cybersecurity Challenges Faced by Digital Twins
Digital twins are exposed to various forms of cyberattacks that could target their data, communication, or functionality.
One of the primary challenges facing digital twins is the generally poor state of security on IoT/IioT/xIoT or OT devices used as sensors within digital twin setups. These devices are often shipped with known default usernames and passwords, making them vulnerable to exploitation by malicious actors. Additionally, there is often a lag in cybersecurity expertise regarding digital twins. This knowledge gap can result in insufficient security measures being implemented, leaving digital twins exposed to potential threats.
Some other common types of cyberattacks that could affect it are:
- Data theft: When an unauthorized party accesses, copies, or exfiltrates the data from the digital twin or the physical asset or system, it could result in loss of intellectual property, breach of privacy, or competitive disadvantage. For example, a hacker could steal the design specifications or performance data of a digital twin of a new product and sell it to a rival company.
- Data manipulation: Unauthorized parties can manipulate, alter, delete, or inject the data from or to the digital twin or the physical asset or system. This could result in false or inaccurate information, malfunction or damage, or misguided decisions.
- Denial of service: A common cybersecurity challenge digital twins face is unexpected disruptions, blocks, or overwhelms in the communication or functionality of the digital twin or the physical asset or system through the data exchange layer.
Possible Use Cases
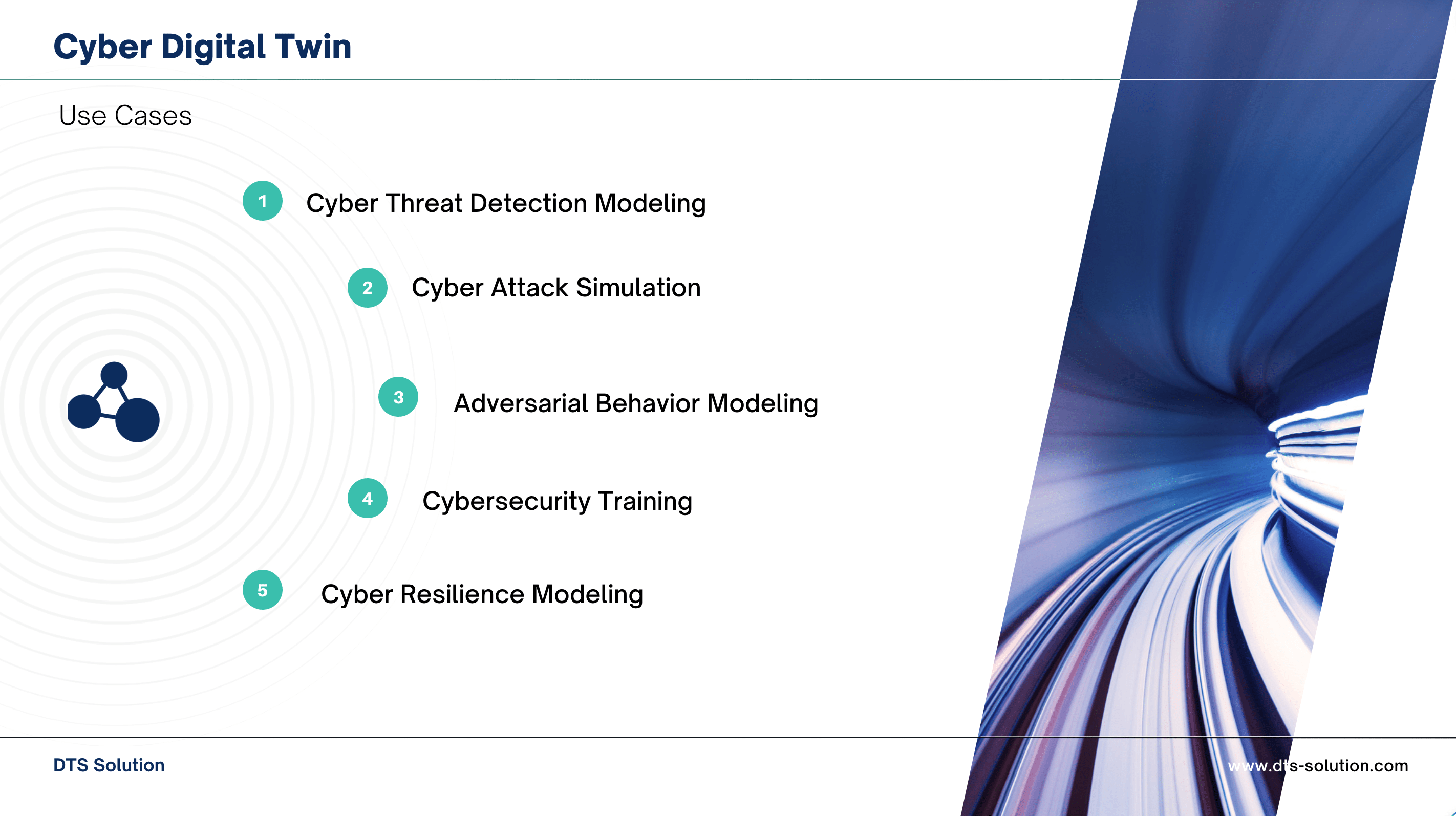
Possible Use Cases

Best Practices for Securing Digital Twins
- Creating detailed threat models and risk assessments for digital twins: Addressing the cybersecurity risks that digital twins face requires identifying and analyzing the potential threats and risks that could affect the digital twin or the physical asset or system. This knowledge helps to prioritize and mitigate the most critical vulnerabilities and impacts. Organizations can use a framework such as STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege), for example, to model the threats and risks of their digital twins.
- Following basic cybersecurity hygiene and adopting zero-trust principles: Applying the fundamental and essential cybersecurity measures and policies that could prevent or reduce the exposure of digital twins to cyberattacks. These measures include updating software and firmware, using strong passwords and multi-factor authentication, enforcing role-based access control, segmenting networks and devices, monitoring logs and activities, and educating users and stakeholders. Moreover, adopting a zero-trust approach—that assumes that no entity or request is trusted by default and requires continuous verification and validation—further improves digital twin security.
- Using encryption, authentication, and authorization mechanisms for data transmission and storage: This technique uses cryptographic methods to protect the confidentiality, integrity, and availability of the data that flows between or within the digital twin or the physical asset or system. It involves encrypting data at rest and in transit, authenticating the identity and legitimacy of the data sources and destinations, and authorizing the access and usage of the data based on predefined rules and policies.
- Applying machine learning and human expertise to detect and respond to anomalies or indicators of cyberattacks: Artificial intelligence systems are here to streamline the effectiveness of various digital processes. It is essential to combine the power of AI and human intelligence to monitor and analyze the data and behavior of the digital twin or the physical system. This will help to detect and respond to any anomalies or indicators of cyberattacks that deviate from the expected patterns or trends. For example, one could use machine learning models such as deep neural networks or reinforcement learning to learn from the data and behavior of the digital twin and the physical asset and alert or act upon any suspicious activities.
- Collaborating with cybersecurity experts and vendors to ensure compliance and interoperability: Working with external parties with specialized knowledge, skills, or resources in cybersecurity for digital twins is also a good practice that organizations must adopt. This will help leverage another person’s expertise and experience to strengthen the cybersecurity posture of the digital twin. It will ensure compliance with relevant standards, regulations, best practices, and interoperability among different digital twins or systems sharing data or functionality.
Best Practices for Securing Digital Twins
Adopting a holistic and proactive approach to cybersecurity is imperative to protect digital twins from cyberattacks. This involves implementing various cybersecurity controls and best practices that could enhance digital twins’ security posture and resilience. Some of these solutions and best practices are:
- Creating detailed threat models and risk assessments for digital twins: Addressing the cybersecurity risks that digital twins face requires identifying and analyzing the potential threats and risks that could affect the digital twin or the physical asset or system. This knowledge helps to prioritize and mitigate the most critical vulnerabilities and impacts. Organizations can use a framework such as STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege), for example, to model the threats and risks of their digital twins.
- Following basic cybersecurity hygiene and adopting zero-trust principles: Applying the fundamental and essential cybersecurity measures and policies that could prevent or reduce the exposure of digital twins to cyberattacks. These measures include updating software and firmware, using strong passwords and multi-factor authentication, enforcing role-based access control, segmenting networks and devices, monitoring logs and activities, and educating users and stakeholders. Moreover, adopting a zero-trust approach—that assumes that no entity or request is trusted by default and requires continuous verification and validation—further improves digital twin security.
- Using encryption, authentication, and authorization mechanisms for data transmission and storage: This technique uses cryptographic methods to protect the confidentiality, integrity, and availability of the data that flows between or within the digital twin or the physical asset or system. It involves encrypting data at rest and in transit, authenticating the identity and legitimacy of the data sources and destinations, and authorizing the access and usage of the data based on predefined rules and policies.
- Applying machine learning and human expertise to detect and respond to anomalies or indicators of cyberattacks: Artificial intelligence systems are here to streamline the effectiveness of various digital processes. It is essential to combine the power of AI and human intelligence to monitor and analyze the data and behavior of the digital twin or the physical system. This will help to detect and respond to any anomalies or indicators of cyberattacks that deviate from the expected patterns or trends. For example, one could use machine learning models such as deep neural networks or reinforcement learning to learn from the data and behavior of the digital twin and the physical asset and alert or act upon any suspicious activities.
- Collaborating with cybersecurity experts and vendors to ensure compliance and interoperability: Working with external parties with specialized knowledge, skills, or resources in cybersecurity for digital twins is also a good practice that organizations must adopt. This will help leverage another person’s expertise and experience to strengthen the cybersecurity posture of the digital twin. It will ensure compliance with relevant standards, regulations, best practices, and interoperability among different digital twins or systems sharing data or functionality.
Conclusion
Conclusion
As digital twins become increasingly prevalent across industries, organizations must prioritize the security and integrity of these virtual replicas. By implementing robust cybersecurity measures, organizations can protect sensitive information, prevent unauthorized access, and ensure the smooth operation of their digital twin deployments.
See also: