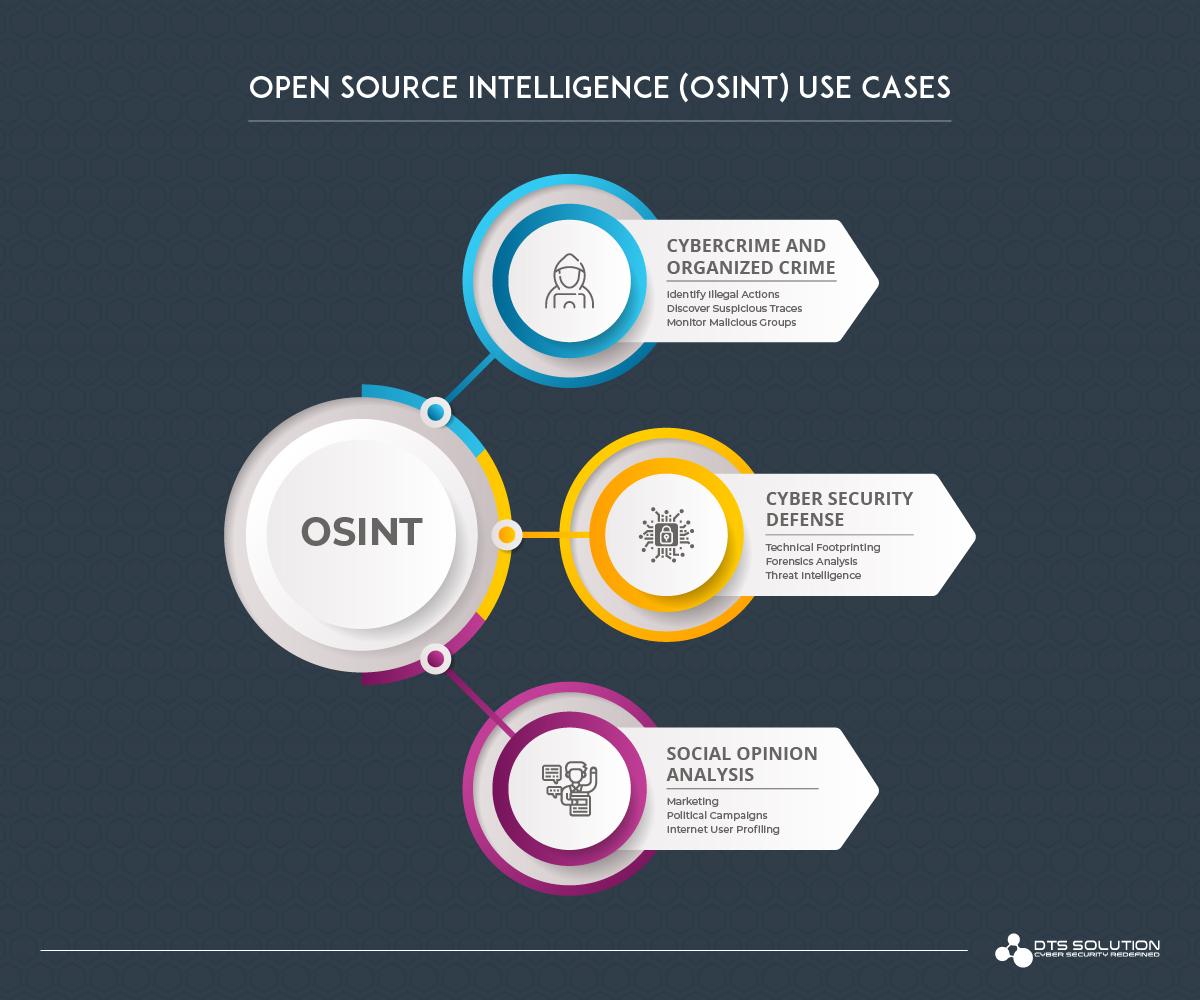
Cyber Threat Intelligence and OSINT
The main purpose of threat intelligence is to help organizations and understand the risks of the most common and severe external threats, such as advanced persistent threats (APTs), zero-day threats, and exploits. After all, threats require appropriate defense, and cyber threat intelligence delivers the capability to defend more proactively. It provides context — like who is attacking you, what their motivation and capabilities are, and what are the Indicators of Compromise (IoC) in your systems to look for — that helps to make informed decisions about your security.
Cyber Threat Intelligence and OSINT
The main purpose of threat intelligence is to help organizations and understand the risks of the most common and severe external threats, such as advanced persistent threats (APTs), zero-day threats, and exploits. After all, threats require appropriate defense, and cyber threat intelligence delivers the capability to defend more proactively. It provides context — like who is attacking you, what their motivation and capabilities are, and what are the Indicators of Compromise (IoC) in your systems to look for — that helps to make informed decisions about your security.
- Ethical Hacking and Penetration Testing
- Recognizing External Threats
- Ethical Hacking and Penetration Testing
- Recognizing External Threats
See also: