Thick Client Assessment
What is a Thick Client?
Thick Client is defined as an application client that process some data in addition to rendering it. An example of thick client applications are applications written in VB, JAVA or VB.NET that communicates with a database.
Why Assess your Thick Client?
Attackers can exploit a thick client application which may lead to sensitive data leakage, viewing of unauthorized information, perform MITM attack, RCE on database server, retrieval of database credentials, retrieval of user credentials.
Since some thick client applications come with custom DLLs, privilege escalation and/or Code execution may also be performed by an attacker.
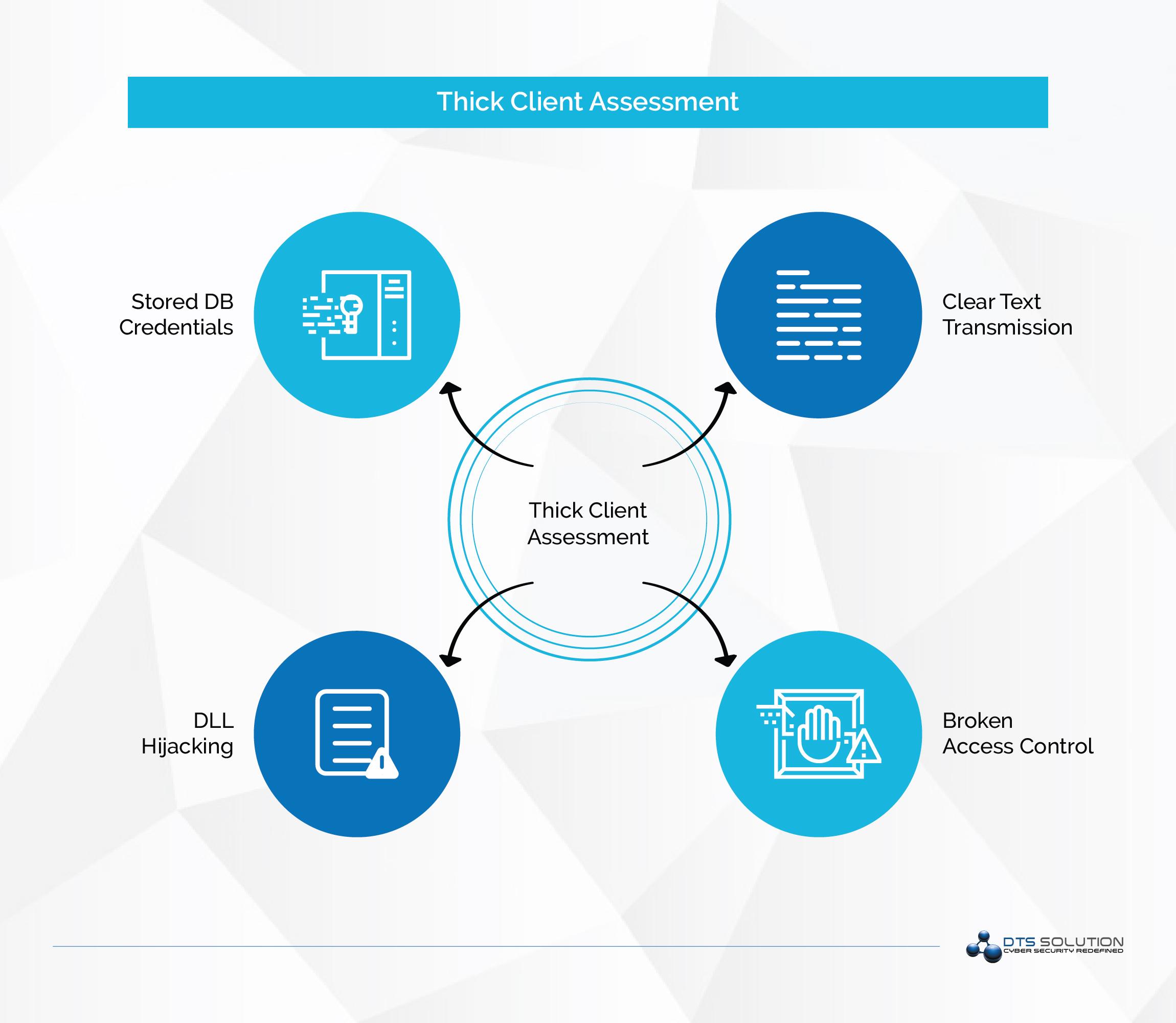
Thick Client Application Vulnerabilities:
The following are the most frequently found vulnerabilities in a thick client application:
- Unvalidated Input
- Broken Access Control
- Weak Authentication and session management
- Buffer Overflows
- DLL Hijacking
- Injection Flaws
- Insecure Storage
- Insecure Configuration Management
- Insecure binary compilation
Thick Client Security Checklist:
The primary purpose of a Thick Client (TC) is to interact with a webserver or a database. Communication to a server or DB maybe via HTTP/HTTPS or via custom protocols. Multiple standard and custom tools are used by the DTS team for thick client assessment. Primary checks are conducted for the following:
- Client to DB data traffic analysis
- Client to DB data traffic encryption checks
- Client to DB data manipulation checks
- Custom client DLL checks
- Client Session Management Checks
- Client Credential Management Checks
- Client Access Control Checks
- Forced URL access via browser
- Error/Exception Handling
- Log file tampering analysis
- Sensitive data exfiltration from disk & memory
- Configuration files analysis
- Reverse Engineering
- Sensitive data leakage in the binary strings
Thick Client Assessment
What is a Thick Client?
Thick Client is defined as an application client that process some data in addition to rendering it. An example of thick client applications are applications written in VB, JAVA or VB.NET that communicates with a database.
Why Assess your Thick Client?
Attackers can exploit a thick client application which may lead to sensitive data leakage, viewing of unauthorized information, perform MITM attack, RCE on database server, retrieval of database credentials, retrieval of user credentials.
Since some thick client applications come with custom DLLs, privilege escalation and/or Code execution may also be performed by an attacker.

Thick Client Application Vulnerabilities:
The following are the most frequently found vulnerabilities in a thick client application:
- Unvalidated Input
- Broken Access Control
- Weak Authentication and session management
- Buffer Overflows
- DLL Hijacking
- Injection Flaws
- Insecure Storage
- Insecure Configuration Management
- Insecure binary compilation
Thick Client Security Checklist:
The primary purpose of a Thick Client (TC) is to interact with a webserver or a database. Communication to a server or DB maybe via HTTP/HTTPS or via custom protocols. Multiple standard and custom tools are used by the DTS team for thick client assessment. Primary checks are conducted for the following:
- Client to DB data traffic analysis
- Client to DB data traffic encryption checks
- Client to DB data manipulation checks
- Custom client DLL checks
- Client Session Management Checks
- Client Credential Management Checks
- Client Access Control Checks
- Forced URL access via browser
- Error/Exception Handling
- Log file tampering analysis
- Sensitive data exfiltration from disk & memory
- Configuration files analysis
- Reverse Engineering
- Sensitive data leakage in the binary strings
See also:

